Using Raw Speech as a Watermark, Does it work?
|
|
|
- Kelley Edwin Lee
- 5 years ago
- Views:
Transcription
1 Using Raw Speech as a Watermark, Does it work? P. Nintanavongsa and T. Amomraksa Multimedia Communications Laboratory, Department of Computer Engineering, King Mongkut's University of Technology Thonburi, Bangkok 10140, Thailand Key words: Abstract: Digital Watermarking, Speech Coding Data piracy has become a great concern in today's multimedia applications since digital data can be reproduced without any quality loss. Digital watermarking is one technique that can be used against piracy. In this paper, we propose an idea of using raw speech data as a watermark signal to enhance the robustness of the watermark. To recover the information in the watermark, the extracted watermark will be played back as speech to a listener, and through the intelligent audio perception of the human listener, the contents of the speech may be recognized. Our approach is based on the fact that raw speech contains a considerable amount of redundancy, therefore, its contents can still be recognized after the extraction process, even if the watermarked data is badly attacked. As long as the raw speech, extracted from the attacked watermarked data, contains enough important information, its contents can be intelligible. Furthermore, the impressive intelligence of the human perceptual system, as it tends to adjust and learn quickly to determine the repeated speech, enhances the probability of recognizing the contents of the extracted raw speech. A set of experiments was carried out to show that the proposed method not only successfully survives the common attacks, but also yields high intelligibility. 1. INTRODUCTION The rapid growth of digital technology allows data to be readily stored in a digital form. Moreover, the unlimited reproduction with no loss in quality makes the digital data preferable to its analog counterpart. However, reproduction of the copyrighted data without permission from the owner results in data piracy. There are many approaches to protecting this kind of The original version of this chapter was revised: The copyright line was incorrect. This has been corrected. The Erratum to this chapter is available at DOI: / _36 R. Steinmetz et al. (eds.), Communications and Multimedia Security Issues of the New Century IFIP International Federation for Information Processing 2001
2 242 piracy, including the encryption of the data prior to. However, the problem is often not completely solved since an authorized user can copy and redistribute the data after the decryption process. Thus, for digital images, digital watermarking techniques serve as the last line of defense by embedding secret information into the original data in such a way that it is invisible to the Human Visual System (HVS). The embedded watermark data can be any information related to the copyright owner, authorized recipient or purchasing information. In this paper, we use the intelligibility contained in speech as a watermark signal. When a copyright violation occurs, the speech embedded as a watermark is extracted to determine the related information. The next section provides an overview of related work done by other researchers. Section 3 describes the details of the algorithm used and related principles. The experimental results and analysis are illustrated in sections 4 and 5, respectively. Finally, the conclusions are drawn in section PREVIOUS WORKS Sakaguchi et al. [1] investigated how the polarity inversion of speech signals affects human perception and applied this technique for data hiding. The experimental results showed that the data was successfully hidden and could then be restored automatically. A scheme for hiding a high bit-rate supplementary data was proposed in [2]. In this scheme, the high bit-rate supplementary data such as secondary video, was hidden into a digital video stream by directly modifying the pixels in the video frames. The experimental results showed that the instructional video can be transmitted with four language options to cover a wide range of interested parties. Recently, Mukherjee et al. [3] implemented a scheme for hiding 8KHz speech sampled at 16 bits/sample in a 30 frames/s QCIF video. The speech and video extracted from the compressed video were found to be intelligible, and acceptable for visual quality, respectively, even at high compression ratio. Rhoads [4] described a method that added or subtracted small random quantities from each pixel. The watermark was subtracted by first computing the difference between the original and watermarked images and then by examining the sign of the difference, pixel by pixel, to determine if it corresponded to the original sequence of additions and subtractions. In [5], two techniques that modified the least significant bits (LSB) of an image, based on the assumption that the LSB data were insignificant, were proposed. However, these two methods were highly sensitive to noise and easily destroyed since only the LSB data are modified. A similar result was obtained in [6), by the method called Patchwork. However, based on the
3 243 experimental results, these two techniques showed a lack of robustness to attacks. Kutter et al. [7] proposed the method for digitally signing the image using amplitude modulation. In this method, the signature bits were multiply embedded by modifying pixel values in the blue channel. The experimental results showed that this proposed method was immune to a variety of attacks. The main improvement brought by this proposed method is that the watermark can be retrieved regardless of the original, unmarked image. 3. BACKGROUND Digital watermarking is a technique, which secretly embeds robust and hidden marks into the material to designate its copyright-related information such as the origin, ownership, rights, and destinations. The basic requirements of the digital watermark, as stated in [8] and [9], can be concisely described as following: invisible, undetectable, irremovable, unalterable, unambiguous, and acceptable quality of the original data. Based on the watermark insertion methods, the watermark can be categorized into 2 types: Spatial watermark: In this method, the watermark is inserted in the spatial domain; thus, no time-frequency domain transformation is required. Spectral watermark: When the watermark is inserted in the frequency domain. In this case, some type of time domain-frequency domain is required. 3.1 Characteristics of speech signals Speech waveforms have a number of useful properties that can be exploited when designing an efficient encoder. Some of the properties that are most often utilized in encoder design include the non-uniform probability of distribution of speech amplitude, the nonzero auto-correlation between successive speech samples, the non-flat nature of the speech spectra, the existence of voiced and unvoiced segment in speech, and the quasiperiodicity of voiced speech signals. The most basic property of the speech waveforms that is exploited by all speech coding is that they are band limited. A finite bandwidth means that it can be sampled at a finite time interval and reconstructed completely from these samples, provided that the sampling frequency is greater than twice the highest frequency component in the low pass signal [10]. While the band limited property of the speech signal makes sampling possible, the aforementioned properties allow
4 244 quantization, another important process in speech coding, to be performed with greater efficiency. 3.2 Watermarking algorithm A watermarking algorithm based on [7] is used in this paper. The algorithm embeds the information into the blue channel, which is the one the human eye is least sensitive to. Furthermore, changes in regions of high frequency and high luminance are less perceptible, and thus favored. However, we make some modifications to the original scheme. The algorithm is described in this section. Let (x, y) be the coordinate corresponding to the position within image I= (R, G, B). The watermark bit is embedded by modifying the blue channel at the positionlp by a fraction of the luminance L = 0.299R G B as follow. when watermark bit is 1 when watermark bit is 0 (1) where a is a constant determining the signature strength. The value of ex is selected to offer the best trade-off between robustness and invisibility. In order to recover the embedded bit, a prediction of the original value of the pixel containing the information is needed. This prediction is based on a linear combination of pixel values in a neighborhood around considered positions. Empirical results show that taking a crossshaped neighborhood gives the best performance. The prediction J:J'xy is thus computed as follows: B'xy =- 1 ( c c ) LBx+k,y + LBx,y+k -2Bxy 4c k=-c k=-c (2) where cis the size of the cross-shaped neighborhood. To retrieve the embedded bit, the difference {3 between the prediction and the actual value of the pixel at position (x, y) is taken: a=b -B' p xy xy (3) The sign of the difference {3 determines the value of the embedded bit. That is, if {3 has a negative value then the embedded bit is zero and vice
5 245 versa. The embedding and the retrieval functions are not symmetric; that is, the retrieval function is not the inverse of thee embedding functions. Although correct retrieval is very likely, it is not guaranteed. To enhance the probability of correct retrieval, the bit is embedded several times, as described below. To improve the retrieval performance, the bit can be embedded n times at different locations. The embedded position is such that the bit is sequentially embedded bit-by-bit into the original image pixel-by-pixel. The information is embedded into the pixel sequentially until the last bit of the information is embedded, then the first bit of information is re-embedded into the pixel position next to where the information bit was previously embedded. The bit retrieval can be improved by computing the difference between the prediction and the value of the pixel for each embedded position k similar to (3). These differences are then averaged as shown in (4). 1 f3 =-2.f3k n k (4) where is a number of positions that each information bit is embedded. 3.3 Mode of Simulation Our proposed method exploits the fact that ordinary speech has considerable redundancy [11]. That is, even though parts of the raw speech are corrupted, the intelligibility of the remaining uncorrupted speech can still be perceptively recognized. The speech encoders reflect this fact as a wide range of speech quality can be provided. Note that less bit-rate speech normally gives lower quality of speech. In this paper. the content of speech is used as a watermark signal instead of its signals characteristics, to increase the robustness of watermarking scheme. The proposed method is distinct from many existing watermarking methods since, in our method, the watermark signal is the intelligent information contained in the speech, which most people can easily recognize through auditory perception. In the experiments, we used the Pulse Code Modulation (PCM) [12] technique for digitizing the speech input from a microphone. PCM is a widely used technique since it encodes each sample of the input waveform independently from all other samples. Therefore, the technique is inherently capable of encoding an arbitrarily random waveform. However, since it encodes every sample independently without regard to the correlation between each sample, a considerable amount of redundancy will be contained in each successive sample. Flanagan et al. [13] stated that the
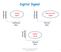
6 246 correlation coefficient between adjacent 8KHz samples is generally 0.85 or higher, and hence the high redundancy in the PCM codes can be used to provide more strength in the waterinarking scheme. In fact, at 8KHz sampling bit-rates, the significant correlations exist for upto two to three samples distances. In addition, the samples become even more correlated if the sampling rate is increased. The 11KHz raw speech of the word "Thank you", which is encoded by the PCM is chosen to be used as a watermark signal. The model of the watermarking process will be that the raw speech is embedded into the original color image with the amplitude modulation in the blue channel to obtain the watermarked image. The algorithm to be used to embed the watermark signal is similar to [7] while the attacks to be applied to the watermarked image are brightness and contrast enhancements, blurring, Gaussian noise, JPEG encoding/decoding, high-pass filtering and equally distributed random noise. After attacking, the corrupted raw speech as an embedded watermark signal is extracted and then played back by a speech decoder to observe its corrupted contents. The 10 English native speakers, 5 male and 5 female, with ages between year-old are chosen to listen to the extracted corrupted speech. Different versions of the corrupted speech will be randomly played back to a listener. After the listener hears the corrupted speech, he/she will tell what is recognized in the speech, that is, to indicate that they hear the phrase "Thank you". The format of the tests is recommended in [14] and [15]. The model of the watermarking scheme is illustrated in the figure below. Raw speech Watermark embedding in blue channel Extracted raw speech Original image AttJtcks Figure I. Model of the watermarking scheme 4. EXPERIMENTAL RESULTS In the experiment, the color image, 512 by 512 pixels and 24-bit color, of Lena taken from (16] is used as the original image. Then the image undergoes the watermark embedding process previously described with the trade-off factor of a= 0.2. The size of the cross-shape window, c, is set to 3
7 247 to embed the raw speech into the blue channel. The raw speech is embedded 4 times in different locations in the blue channel to enhance the probability of efficient retrieval. The simulation of watermark attack is then performed on the watermarked image. The raw speech to be embedded is 11KHz sampling frequency, 8-bit per sample. The original image and the original waveform of the speech are shown in figure 2. (a) (b) Figure 2. a) The original image Lena'b) the original waveform of the speech 4.1 Brightness an,d contrast enhancement Figure 3 illustrates an example of different versions of watermarked image after brightness enhancement is performed. In a), the watermarked image is brightness enhanced by 40% from the watermarked image and the extracted speech is shown in b). (a) (b) Figure 3. a) The watermarked image of Lena'with brightness enhancement b) the speech waveform with 40% brightness enhancement
8 Blurring Figure 4 shows another example of the watermarked images after blurring. The watermarked image is blurred by the factor of 5, which correspond to the number of neighboring pixels involved i.e. neighborhood of averaging filter = 5. The waveform of the extracted speech after blurring is also shown below. (a) (b) Figure 4. a) The watermarked image of Lena' after blurring by the factor of 5 b) the speech waveform after blurring by the factor of 5 In the experiments, we also performed three common attacks to the watermarked image, namely Gaussian additive noise adding, JPEG encoding and high-pass filtering. That is, the Gaussian additive noise is added into the watermarked image by different amount, 15% and 30% of the watermarked image. In JPEG encoding, the JPEG encoding cycle is performed on the watermarked image. Two different degrees of image quality, 70% quality and 40 % quality, are individually applied to the watermarked image. The final attack that we tested is by applying the high-pass filter with the radius of 10 pixels to the watermarked image and then observe whether the embedded watermark can still survive this type of attack. The experimental results are shown in the table below. Table I. Number of people who can recognize the word "Thank you" Tvpe of attack applied to watermarked ima2e Number of people 40% of Bri2htness enhancement 10 40% of Contrast enhancement 10 Blurring by factor of I 10 Blurring by factor of 5 0 Gaussian additive noise addin2 by 15% 10 Gaussian additive noise adding by 30% 0 JPEG cycle by 70% aualitv 10 JPEG cycle by 40% quality 8 Hi2h-pass filtering 10
9 Equally distributed random noise adding To further illustrate the effectiveness of our proposed technique, the equally distributed random noise is added to the image at various levels to simulate the attack. The different versions of extracted corrupted speech were played back to the listeners, and the listening tests'results are shown in table 2. Table 2. Number of people who can recognize the word "Thank you" 5. EXPERIMENTAL ANALYSIS AND DISCUSSIONS From the table 1, each person could recognize what was saying in the corrupted speech when the watermarked image passed through brightness enhancement. The same result was also achieved when contrast enhancement was applied to the watermarked image since all the participants precisely determined the content of the extracted speech. Moreover, when the watermarked image was blurred by a factor of 1, the embedded content can be correctly determined. However, when the watermarked image was severely attacked after blurring by a factor of 5, none of participants could determine the content of the extracted speech. The Gaussian additive noise attack also yielded similar results since the extracted speech could be precisely determined for the Gaussian additive noise added by 15% of image area. On the contrary, the content of the extracted speech could not be determined from the watermarked image with 30% added Gaussian additive noise. The experimental results also showed that it could impressively survive the brightness and contrast enhancement. Furthermore, the extracted speech after applying high-pass filter was highly perceptible since all participants recognized the content of the extracted speech. The JPEG encoding/decoding has the effect on the extracted speech, as the perceptibility of the extracted speech is proportional to the encoded image quality. That is, the lower the quality of the encoded image, the less perceptibility of the extracted speech is observed. However, a trade-off should be made between quality of the encoded image and the perceptibility of the extracted speech. From the table 2, at 10% of noise, everyone could recognize what was said in the corrupted speech. However, the number decreased when the level of noise got higher, for instance, at 60% of additive noise. Nevertheless, at 100% of noise adding, there were 3 out of 10 could
10 250 recognize the contents of the corrupted speech. Likewise, a majority of the extracted speech waveform reveals that even if the watermarked image was attacked so that the waveform of the extracted speech was almost totally different, some people recognized the contents inside the extracted speech. Furthermore, we believe that the perceptibility will be greatly improved if the corrupted speech is examined by the copyright owner, since he/she will know exactly what he/she has placed in the embedded speech, and then make the identification of the content in the speech considerably easier. 6. CONCLUSIONS This paper has presented the idea of using raw speech as a watermark to enhance the robustness of the watermarking schemes. The major advantage is that it can easily be incorporated into the existing schemes for watermarking. In the proposed method, the embedded speech also carries a unique message in its content, thus serving as a direct means of ownership identification. The experimental results show that the proposed method is immune to various forms of attacks, since in most cases, speech intelligibility remained in the corrupted image. Although the method has not been fully explored, we have demonstrated in this paper that it meets all the requirements of an effective watermarking application. Acknowledgments: This work was supported by project NT-B-06-4C funded by the National Electronics and Computer Technology Center (NECTEC). References [I] S. Sakaguchi, T. Arai andy. Murahara, "The effect of polarity inversion of speech on human perception and data hiding as an application", Proceedings IEEE International Conference on Acoustics, Speech and Signal Processing, Vol. 2, pp , [2] M.D. Swanson, B. Zhu and A. H. Tewfik, "Data hiding for video-in-video", Proceedings International Conference on Image Processing, Vol. 2, pp , [3] D. Mukherjee, J. J. Chae, S. K. Mitra and B. S. Manjunath, "A source and channel-coding framework for vector-based data hiding in IEEE Transactions on Circuits and Systems for Video Technology, Vol. 10, No.4, June (4] G. B. Rhoads, "lndentification/authentication coding method and apparatus", Rep. WIPO WO , World Intellectual Property Organization, [5] R.G. Van Schyndel, A. Z. Tirkel and C. F. Osborne, "A digital International Conference on Image Processing, Vol. 2, pp , [6] W. Bender, D. Gruhl and N. Morimoto, "Techniques for data hiding", Proceedings SPIE, Vol. 2420, pp. 40, February [7] M. Kutter, F. Jordan and F. Bossen, "Digital Signature of color images using amplitude modulation", Journal of Electronic Imaging, Vol.7, pp , 1998.
11 251 [8] M. George, J. Y. Chouinard and N. Georganas, "Digital watermarking of images and video using direct sequence spread spectrum techniques", Proceedings IEEE Canadian Conference on Electrical and Computer Engineer, Shaw Conference Center, Edmonton, Alberta, Canada, May [9] F. Hartung and M. Kutter, "Multimedia watermarking techniques", Proceedings of IEEE, Vol. 87, No.7, pp , July [10] T. S. Rappaport, "Wireless communications principles and practice", Prentice Hall, [II] J. Bellamy, "Digital telephony", John Wiley & Sons, pp , [12] S. Haykin, "Communication systems", John Willy & Sons, INC, [13] J. Flanagan, M. Schroeder, B. Atal, R. Crochiere, N. Jayant and J. Tribolet, "Speech coding", IEEE Transactions Communications, pp , Aprill979. [14] M. H. Segal, "Speech intelligibility in the space shuttle mid-deck noise Environment: The Effect of Active Noise Reduction Technology", November [15] H. K. Dunn and S.D. White, "Statistical measurements on conversational speech", Journal of Acoustic Society of America, pp , January [16] CityU Image Processing Lab,
WATERMARKING USING DECIMAL SEQUENCES. Navneet Mandhani and Subhash Kak
 Cryptologia, volume 29, January 2005 WATERMARKING USING DECIMAL SEQUENCES Navneet Mandhani and Subhash Kak ADDRESS: Department of Electrical and Computer Engineering, Louisiana State University, Baton
Cryptologia, volume 29, January 2005 WATERMARKING USING DECIMAL SEQUENCES Navneet Mandhani and Subhash Kak ADDRESS: Department of Electrical and Computer Engineering, Louisiana State University, Baton
DELTA MODULATION AND DPCM CODING OF COLOR SIGNALS
 DELTA MODULATION AND DPCM CODING OF COLOR SIGNALS Item Type text; Proceedings Authors Habibi, A. Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
DELTA MODULATION AND DPCM CODING OF COLOR SIGNALS Item Type text; Proceedings Authors Habibi, A. Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
Research Article. ISSN (Print) *Corresponding author Shireen Fathima
 Scholars Journal of Engineering and Technology (SJET) Sch. J. Eng. Tech., 2014; 2(4C):613-620 Scholars Academic and Scientific Publisher (An International Publisher for Academic and Scientific Resources)
Scholars Journal of Engineering and Technology (SJET) Sch. J. Eng. Tech., 2014; 2(4C):613-620 Scholars Academic and Scientific Publisher (An International Publisher for Academic and Scientific Resources)
AN ARTISTIC TECHNIQUE FOR AUDIO-TO-VIDEO TRANSLATION ON A MUSIC PERCEPTION STUDY
 AN ARTISTIC TECHNIQUE FOR AUDIO-TO-VIDEO TRANSLATION ON A MUSIC PERCEPTION STUDY Eugene Mikyung Kim Department of Music Technology, Korea National University of Arts eugene@u.northwestern.edu ABSTRACT
AN ARTISTIC TECHNIQUE FOR AUDIO-TO-VIDEO TRANSLATION ON A MUSIC PERCEPTION STUDY Eugene Mikyung Kim Department of Music Technology, Korea National University of Arts eugene@u.northwestern.edu ABSTRACT
CONSTRUCTION OF LOW-DISTORTED MESSAGE-RICH VIDEOS FOR PERVASIVE COMMUNICATION
 2016 International Computer Symposium CONSTRUCTION OF LOW-DISTORTED MESSAGE-RICH VIDEOS FOR PERVASIVE COMMUNICATION 1 Zhen-Yu You ( ), 2 Yu-Shiuan Tsai ( ) and 3 Wen-Hsiang Tsai ( ) 1 Institute of Information
2016 International Computer Symposium CONSTRUCTION OF LOW-DISTORTED MESSAGE-RICH VIDEOS FOR PERVASIVE COMMUNICATION 1 Zhen-Yu You ( ), 2 Yu-Shiuan Tsai ( ) and 3 Wen-Hsiang Tsai ( ) 1 Institute of Information
Video compression principles. Color Space Conversion. Sub-sampling of Chrominance Information. Video: moving pictures and the terms frame and
 Video compression principles Video: moving pictures and the terms frame and picture. one approach to compressing a video source is to apply the JPEG algorithm to each frame independently. This approach
Video compression principles Video: moving pictures and the terms frame and picture. one approach to compressing a video source is to apply the JPEG algorithm to each frame independently. This approach
CERIAS Tech Report Preprocessing and Postprocessing Techniques for Encoding Predictive Error Frames in Rate Scalable Video Codecs by E
 CERIAS Tech Report 2001-118 Preprocessing and Postprocessing Techniques for Encoding Predictive Error Frames in Rate Scalable Video Codecs by E Asbun, P Salama, E Delp Center for Education and Research
CERIAS Tech Report 2001-118 Preprocessing and Postprocessing Techniques for Encoding Predictive Error Frames in Rate Scalable Video Codecs by E Asbun, P Salama, E Delp Center for Education and Research
ELEC 691X/498X Broadcast Signal Transmission Fall 2015
 ELEC 691X/498X Broadcast Signal Transmission Fall 2015 Instructor: Dr. Reza Soleymani, Office: EV 5.125, Telephone: 848 2424 ext.: 4103. Office Hours: Wednesday, Thursday, 14:00 15:00 Time: Tuesday, 2:45
ELEC 691X/498X Broadcast Signal Transmission Fall 2015 Instructor: Dr. Reza Soleymani, Office: EV 5.125, Telephone: 848 2424 ext.: 4103. Office Hours: Wednesday, Thursday, 14:00 15:00 Time: Tuesday, 2:45
DIGITAL COMMUNICATION
 10EC61 DIGITAL COMMUNICATION UNIT 3 OUTLINE Waveform coding techniques (continued), DPCM, DM, applications. Base-Band Shaping for Data Transmission Discrete PAM signals, power spectra of discrete PAM signals.
10EC61 DIGITAL COMMUNICATION UNIT 3 OUTLINE Waveform coding techniques (continued), DPCM, DM, applications. Base-Band Shaping for Data Transmission Discrete PAM signals, power spectra of discrete PAM signals.
Channel models for high-capacity information hiding in images
 Channel models for high-capacity information hiding in images Johann A. Briffa a, Manohar Das b School of Engineering and Computer Science Oakland University, Rochester MI 48309 ABSTRACT We consider the
Channel models for high-capacity information hiding in images Johann A. Briffa a, Manohar Das b School of Engineering and Computer Science Oakland University, Rochester MI 48309 ABSTRACT We consider the
1 Introduction to PSQM
 A Technical White Paper on Sage s PSQM Test Renshou Dai August 7, 2000 1 Introduction to PSQM 1.1 What is PSQM test? PSQM stands for Perceptual Speech Quality Measure. It is an ITU-T P.861 [1] recommended
A Technical White Paper on Sage s PSQM Test Renshou Dai August 7, 2000 1 Introduction to PSQM 1.1 What is PSQM test? PSQM stands for Perceptual Speech Quality Measure. It is an ITU-T P.861 [1] recommended
Communication Lab. Assignment On. Bi-Phase Code and Integrate-and-Dump (DC 7) MSc Telecommunications and Computer Networks Engineering
 Faculty of Engineering, Science and the Built Environment Department of Electrical, Computer and Communications Engineering Communication Lab Assignment On Bi-Phase Code and Integrate-and-Dump (DC 7) MSc
Faculty of Engineering, Science and the Built Environment Department of Electrical, Computer and Communications Engineering Communication Lab Assignment On Bi-Phase Code and Integrate-and-Dump (DC 7) MSc
MULTI-STATE VIDEO CODING WITH SIDE INFORMATION. Sila Ekmekci Flierl, Thomas Sikora
 MULTI-STATE VIDEO CODING WITH SIDE INFORMATION Sila Ekmekci Flierl, Thomas Sikora Technical University Berlin Institute for Telecommunications D-10587 Berlin / Germany ABSTRACT Multi-State Video Coding
MULTI-STATE VIDEO CODING WITH SIDE INFORMATION Sila Ekmekci Flierl, Thomas Sikora Technical University Berlin Institute for Telecommunications D-10587 Berlin / Germany ABSTRACT Multi-State Video Coding
Module 8 VIDEO CODING STANDARDS. Version 2 ECE IIT, Kharagpur
 Module 8 VIDEO CODING STANDARDS Lesson 27 H.264 standard Lesson Objectives At the end of this lesson, the students should be able to: 1. State the broad objectives of the H.264 standard. 2. List the improved
Module 8 VIDEO CODING STANDARDS Lesson 27 H.264 standard Lesson Objectives At the end of this lesson, the students should be able to: 1. State the broad objectives of the H.264 standard. 2. List the improved
Robust Transmission of H.264/AVC Video Using 64-QAM and Unequal Error Protection
 Robust Transmission of H.264/AVC Video Using 64-QAM and Unequal Error Protection Ahmed B. Abdurrhman, Michael E. Woodward, and Vasileios Theodorakopoulos School of Informatics, Department of Computing,
Robust Transmission of H.264/AVC Video Using 64-QAM and Unequal Error Protection Ahmed B. Abdurrhman, Michael E. Woodward, and Vasileios Theodorakopoulos School of Informatics, Department of Computing,
Unequal Error Protection Codes for Wavelet Image Transmission over W-CDMA, AWGN and Rayleigh Fading Channels
 Unequal Error Protection Codes for Wavelet Image Transmission over W-CDMA, AWGN and Rayleigh Fading Channels MINH H. LE and RANJITH LIYANA-PATHIRANA School of Engineering and Industrial Design College
Unequal Error Protection Codes for Wavelet Image Transmission over W-CDMA, AWGN and Rayleigh Fading Channels MINH H. LE and RANJITH LIYANA-PATHIRANA School of Engineering and Industrial Design College
Region Adaptive Unsharp Masking based DCT Interpolation for Efficient Video Intra Frame Up-sampling
 International Conference on Electronic Design and Signal Processing (ICEDSP) 0 Region Adaptive Unsharp Masking based DCT Interpolation for Efficient Video Intra Frame Up-sampling Aditya Acharya Dept. of
International Conference on Electronic Design and Signal Processing (ICEDSP) 0 Region Adaptive Unsharp Masking based DCT Interpolation for Efficient Video Intra Frame Up-sampling Aditya Acharya Dept. of
Performance Improvement of AMBE 3600 bps Vocoder with Improved FEC
 Performance Improvement of AMBE 3600 bps Vocoder with Improved FEC Ali Ekşim and Hasan Yetik Center of Research for Advanced Technologies of Informatics and Information Security (TUBITAK-BILGEM) Turkey
Performance Improvement of AMBE 3600 bps Vocoder with Improved FEC Ali Ekşim and Hasan Yetik Center of Research for Advanced Technologies of Informatics and Information Security (TUBITAK-BILGEM) Turkey
Ch. 1: Audio/Image/Video Fundamentals Multimedia Systems. School of Electrical Engineering and Computer Science Oregon State University
 Ch. 1: Audio/Image/Video Fundamentals Multimedia Systems Prof. Ben Lee School of Electrical Engineering and Computer Science Oregon State University Outline Computer Representation of Audio Quantization
Ch. 1: Audio/Image/Video Fundamentals Multimedia Systems Prof. Ben Lee School of Electrical Engineering and Computer Science Oregon State University Outline Computer Representation of Audio Quantization
A Big Umbrella. Content Creation: produce the media, compress it to a format that is portable/ deliverable
 A Big Umbrella Content Creation: produce the media, compress it to a format that is portable/ deliverable Distribution: how the message arrives is often as important as what the message is Search: finding
A Big Umbrella Content Creation: produce the media, compress it to a format that is portable/ deliverable Distribution: how the message arrives is often as important as what the message is Search: finding
Behavior Forensics for Scalable Multiuser Collusion: Fairness Versus Effectiveness H. Vicky Zhao, Member, IEEE, and K. J. Ray Liu, Fellow, IEEE
 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 1, NO. 3, SEPTEMBER 2006 311 Behavior Forensics for Scalable Multiuser Collusion: Fairness Versus Effectiveness H. Vicky Zhao, Member, IEEE,
IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 1, NO. 3, SEPTEMBER 2006 311 Behavior Forensics for Scalable Multiuser Collusion: Fairness Versus Effectiveness H. Vicky Zhao, Member, IEEE,
Research Topic. Error Concealment Techniques in H.264/AVC for Wireless Video Transmission in Mobile Networks
 Research Topic Error Concealment Techniques in H.264/AVC for Wireless Video Transmission in Mobile Networks July 22 nd 2008 Vineeth Shetty Kolkeri EE Graduate,UTA 1 Outline 2. Introduction 3. Error control
Research Topic Error Concealment Techniques in H.264/AVC for Wireless Video Transmission in Mobile Networks July 22 nd 2008 Vineeth Shetty Kolkeri EE Graduate,UTA 1 Outline 2. Introduction 3. Error control
Digital Video Telemetry System
 Digital Video Telemetry System Item Type text; Proceedings Authors Thom, Gary A.; Snyder, Edwin Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
Digital Video Telemetry System Item Type text; Proceedings Authors Thom, Gary A.; Snyder, Edwin Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
Steganographic Technique for Hiding Secret Audio in an Image
 Steganographic Technique for Hiding Secret Audio in an Image 1 Aiswarya T, 2 Mansi Shah, 3 Aishwarya Talekar, 4 Pallavi Raut 1,2,3 UG Student, 4 Assistant Professor, 1,2,3,4 St John of Engineering & Management,
Steganographic Technique for Hiding Secret Audio in an Image 1 Aiswarya T, 2 Mansi Shah, 3 Aishwarya Talekar, 4 Pallavi Raut 1,2,3 UG Student, 4 Assistant Professor, 1,2,3,4 St John of Engineering & Management,
PCM ENCODING PREPARATION... 2 PCM the PCM ENCODER module... 4
 PCM ENCODING PREPARATION... 2 PCM... 2 PCM encoding... 2 the PCM ENCODER module... 4 front panel features... 4 the TIMS PCM time frame... 5 pre-calculations... 5 EXPERIMENT... 5 patching up... 6 quantizing
PCM ENCODING PREPARATION... 2 PCM... 2 PCM encoding... 2 the PCM ENCODER module... 4 front panel features... 4 the TIMS PCM time frame... 5 pre-calculations... 5 EXPERIMENT... 5 patching up... 6 quantizing
University of Bristol - Explore Bristol Research. Peer reviewed version. Link to published version (if available): /ISCAS.2005.
 Wang, D., Canagarajah, CN., & Bull, DR. (2005). S frame design for multiple description video coding. In IEEE International Symposium on Circuits and Systems (ISCAS) Kobe, Japan (Vol. 3, pp. 19 - ). Institute
Wang, D., Canagarajah, CN., & Bull, DR. (2005). S frame design for multiple description video coding. In IEEE International Symposium on Circuits and Systems (ISCAS) Kobe, Japan (Vol. 3, pp. 19 - ). Institute
DATA hiding technologies have been widely studied in
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL 18, NO 6, JUNE 2008 769 A Novel Look-Up Table Design Method for Data Hiding With Reduced Distortion Xiao-Ping Zhang, Senior Member, IEEE,
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL 18, NO 6, JUNE 2008 769 A Novel Look-Up Table Design Method for Data Hiding With Reduced Distortion Xiao-Ping Zhang, Senior Member, IEEE,
CHAPTER 8 CONCLUSION AND FUTURE SCOPE
 124 CHAPTER 8 CONCLUSION AND FUTURE SCOPE Data hiding is becoming one of the most rapidly advancing techniques the field of research especially with increase in technological advancements in internet and
124 CHAPTER 8 CONCLUSION AND FUTURE SCOPE Data hiding is becoming one of the most rapidly advancing techniques the field of research especially with increase in technological advancements in internet and
Introduction to image compression
 Introduction to image compression 1997-2015 Josef Pelikán CGG MFF UK Praha pepca@cgg.mff.cuni.cz http://cgg.mff.cuni.cz/~pepca/ Compression 2015 Josef Pelikán, http://cgg.mff.cuni.cz/~pepca 1 / 12 Motivation
Introduction to image compression 1997-2015 Josef Pelikán CGG MFF UK Praha pepca@cgg.mff.cuni.cz http://cgg.mff.cuni.cz/~pepca/ Compression 2015 Josef Pelikán, http://cgg.mff.cuni.cz/~pepca 1 / 12 Motivation
INTRA-FRAME WAVELET VIDEO CODING
 INTRA-FRAME WAVELET VIDEO CODING Dr. T. Morris, Mr. D. Britch Department of Computation, UMIST, P. O. Box 88, Manchester, M60 1QD, United Kingdom E-mail: t.morris@co.umist.ac.uk dbritch@co.umist.ac.uk
INTRA-FRAME WAVELET VIDEO CODING Dr. T. Morris, Mr. D. Britch Department of Computation, UMIST, P. O. Box 88, Manchester, M60 1QD, United Kingdom E-mail: t.morris@co.umist.ac.uk dbritch@co.umist.ac.uk
Department of Communication Engineering Digital Communication Systems Lab CME 313-Lab
 German Jordanian University Department of Communication Engineering Digital Communication Systems Lab CME 313-Lab Experiment 3 Pulse Code Modulation Eng. Anas Alashqar Dr. Ala' Khalifeh 1 Experiment 2Experiment
German Jordanian University Department of Communication Engineering Digital Communication Systems Lab CME 313-Lab Experiment 3 Pulse Code Modulation Eng. Anas Alashqar Dr. Ala' Khalifeh 1 Experiment 2Experiment
52 IEEE TRANSACTIONS ON MULTIMEDIA, VOL. 7, NO. 1, FEBRUARY 2005
 52 IEEE TRANSACTIONS ON MULTIMEDIA, VOL. 7, NO. 1, FEBRUARY 2005 Spatially Localized Image-Dependent Watermarking for Statistical Invisibility and Collusion Resistance Karen Su, Student Member, IEEE, Deepa
52 IEEE TRANSACTIONS ON MULTIMEDIA, VOL. 7, NO. 1, FEBRUARY 2005 Spatially Localized Image-Dependent Watermarking for Statistical Invisibility and Collusion Resistance Karen Su, Student Member, IEEE, Deepa
Robust Transmission of H.264/AVC Video using 64-QAM and unequal error protection
 Robust Transmission of H.264/AVC Video using 64-QAM and unequal error protection Ahmed B. Abdurrhman 1, Michael E. Woodward 1 and Vasileios Theodorakopoulos 2 1 School of Informatics, Department of Computing,
Robust Transmission of H.264/AVC Video using 64-QAM and unequal error protection Ahmed B. Abdurrhman 1, Michael E. Woodward 1 and Vasileios Theodorakopoulos 2 1 School of Informatics, Department of Computing,
Principles of Video Compression
 Principles of Video Compression Topics today Introduction Temporal Redundancy Reduction Coding for Video Conferencing (H.261, H.263) (CSIT 410) 2 Introduction Reduce video bit rates while maintaining an
Principles of Video Compression Topics today Introduction Temporal Redundancy Reduction Coding for Video Conferencing (H.261, H.263) (CSIT 410) 2 Introduction Reduce video bit rates while maintaining an
Colour Reproduction Performance of JPEG and JPEG2000 Codecs
 Colour Reproduction Performance of JPEG and JPEG000 Codecs A. Punchihewa, D. G. Bailey, and R. M. Hodgson Institute of Information Sciences & Technology, Massey University, Palmerston North, New Zealand
Colour Reproduction Performance of JPEG and JPEG000 Codecs A. Punchihewa, D. G. Bailey, and R. M. Hodgson Institute of Information Sciences & Technology, Massey University, Palmerston North, New Zealand
Analysis of Different Pseudo Noise Sequences
 Analysis of Different Pseudo Noise Sequences Alka Sawlikar, Manisha Sharma Abstract Pseudo noise (PN) sequences are widely used in digital communications and the theory involved has been treated extensively
Analysis of Different Pseudo Noise Sequences Alka Sawlikar, Manisha Sharma Abstract Pseudo noise (PN) sequences are widely used in digital communications and the theory involved has been treated extensively
Non-noticeable Information Embedding in Color Images: Marking and Detection
 Non-noticeable nformation Embedding in Color mages: Marking and Detection Josep Vidal, Elisa Sayrol, Silvia Cabanillas, Sonia Santamaria Dept. Teoria de la Sefial y Comunicaciones Universidad PolitCcnica
Non-noticeable nformation Embedding in Color mages: Marking and Detection Josep Vidal, Elisa Sayrol, Silvia Cabanillas, Sonia Santamaria Dept. Teoria de la Sefial y Comunicaciones Universidad PolitCcnica
Visual Communication at Limited Colour Display Capability
 Visual Communication at Limited Colour Display Capability Yan Lu, Wen Gao and Feng Wu Abstract: A novel scheme for visual communication by means of mobile devices with limited colour display capability
Visual Communication at Limited Colour Display Capability Yan Lu, Wen Gao and Feng Wu Abstract: A novel scheme for visual communication by means of mobile devices with limited colour display capability
A Novel Approach towards Video Compression for Mobile Internet using Transform Domain Technique
 A Novel Approach towards Video Compression for Mobile Internet using Transform Domain Technique Dhaval R. Bhojani Research Scholar, Shri JJT University, Jhunjunu, Rajasthan, India Ved Vyas Dwivedi, PhD.
A Novel Approach towards Video Compression for Mobile Internet using Transform Domain Technique Dhaval R. Bhojani Research Scholar, Shri JJT University, Jhunjunu, Rajasthan, India Ved Vyas Dwivedi, PhD.
ROBUST ADAPTIVE INTRA REFRESH FOR MULTIVIEW VIDEO
 ROBUST ADAPTIVE INTRA REFRESH FOR MULTIVIEW VIDEO Sagir Lawan1 and Abdul H. Sadka2 1and 2 Department of Electronic and Computer Engineering, Brunel University, London, UK ABSTRACT Transmission error propagation
ROBUST ADAPTIVE INTRA REFRESH FOR MULTIVIEW VIDEO Sagir Lawan1 and Abdul H. Sadka2 1and 2 Department of Electronic and Computer Engineering, Brunel University, London, UK ABSTRACT Transmission error propagation
ERROR CONCEALMENT TECHNIQUES IN H.264 VIDEO TRANSMISSION OVER WIRELESS NETWORKS
 Multimedia Processing Term project on ERROR CONCEALMENT TECHNIQUES IN H.264 VIDEO TRANSMISSION OVER WIRELESS NETWORKS Interim Report Spring 2016 Under Dr. K. R. Rao by Moiz Mustafa Zaveri (1001115920)
Multimedia Processing Term project on ERROR CONCEALMENT TECHNIQUES IN H.264 VIDEO TRANSMISSION OVER WIRELESS NETWORKS Interim Report Spring 2016 Under Dr. K. R. Rao by Moiz Mustafa Zaveri (1001115920)
COMP 249 Advanced Distributed Systems Multimedia Networking. Video Compression Standards
 COMP 9 Advanced Distributed Systems Multimedia Networking Video Compression Standards Kevin Jeffay Department of Computer Science University of North Carolina at Chapel Hill jeffay@cs.unc.edu September,
COMP 9 Advanced Distributed Systems Multimedia Networking Video Compression Standards Kevin Jeffay Department of Computer Science University of North Carolina at Chapel Hill jeffay@cs.unc.edu September,
Study of White Gaussian Noise with Varying Signal to Noise Ratio in Speech Signal using Wavelet
 American International Journal of Research in Science, Technology, Engineering & Mathematics Available online at http://www.iasir.net ISSN (Print): 2328-3491, ISSN (Online): 2328-3580, ISSN (CD-ROM): 2328-3629
American International Journal of Research in Science, Technology, Engineering & Mathematics Available online at http://www.iasir.net ISSN (Print): 2328-3491, ISSN (Online): 2328-3580, ISSN (CD-ROM): 2328-3629
TERRESTRIAL broadcasting of digital television (DTV)
 IEEE TRANSACTIONS ON BROADCASTING, VOL 51, NO 1, MARCH 2005 133 Fast Initialization of Equalizers for VSB-Based DTV Transceivers in Multipath Channel Jong-Moon Kim and Yong-Hwan Lee Abstract This paper
IEEE TRANSACTIONS ON BROADCASTING, VOL 51, NO 1, MARCH 2005 133 Fast Initialization of Equalizers for VSB-Based DTV Transceivers in Multipath Channel Jong-Moon Kim and Yong-Hwan Lee Abstract This paper
Digital Signal. Continuous. Continuous. amplitude. amplitude. Discrete-time Signal. Analog Signal. Discrete. Continuous. time. time.
 Discrete amplitude Continuous amplitude Continuous amplitude Digital Signal Analog Signal Discrete-time Signal Continuous time Discrete time Digital Signal Discrete time 1 Digital Signal contd. Analog
Discrete amplitude Continuous amplitude Continuous amplitude Digital Signal Analog Signal Discrete-time Signal Continuous time Discrete time Digital Signal Discrete time 1 Digital Signal contd. Analog
Skip Length and Inter-Starvation Distance as a Combined Metric to Assess the Quality of Transmitted Video
 Skip Length and Inter-Starvation Distance as a Combined Metric to Assess the Quality of Transmitted Video Mohamed Hassan, Taha Landolsi, Husameldin Mukhtar, and Tamer Shanableh College of Engineering American
Skip Length and Inter-Starvation Distance as a Combined Metric to Assess the Quality of Transmitted Video Mohamed Hassan, Taha Landolsi, Husameldin Mukhtar, and Tamer Shanableh College of Engineering American
AUDIOVISUAL COMMUNICATION
 AUDIOVISUAL COMMUNICATION Laboratory Session: Recommendation ITU-T H.261 Fernando Pereira The objective of this lab session about Recommendation ITU-T H.261 is to get the students familiar with many aspects
AUDIOVISUAL COMMUNICATION Laboratory Session: Recommendation ITU-T H.261 Fernando Pereira The objective of this lab session about Recommendation ITU-T H.261 is to get the students familiar with many aspects
WYNER-ZIV VIDEO CODING WITH LOW ENCODER COMPLEXITY
 WYNER-ZIV VIDEO CODING WITH LOW ENCODER COMPLEXITY (Invited Paper) Anne Aaron and Bernd Girod Information Systems Laboratory Stanford University, Stanford, CA 94305 {amaaron,bgirod}@stanford.edu Abstract
WYNER-ZIV VIDEO CODING WITH LOW ENCODER COMPLEXITY (Invited Paper) Anne Aaron and Bernd Girod Information Systems Laboratory Stanford University, Stanford, CA 94305 {amaaron,bgirod}@stanford.edu Abstract
Spatial Error Concealment Technique for Losslessly Compressed Images Using Data Hiding in Error-Prone Channels
 168 JOURNAL OF COMMUNICATIONS AND NETWORKS, VOL. 12, NO. 2, APRIL 2010 Spatial Error Concealment Technique for Losslessly Compressed Images Using Data Hiding in Error-Prone Channels Kyung-Su Kim, Hae-Yeoun
168 JOURNAL OF COMMUNICATIONS AND NETWORKS, VOL. 12, NO. 2, APRIL 2010 Spatial Error Concealment Technique for Losslessly Compressed Images Using Data Hiding in Error-Prone Channels Kyung-Su Kim, Hae-Yeoun
CAP240 First semester 1430/1431. Sheet 4
 King Saud University College of Computer and Information Sciences Department of Information Technology CAP240 First semester 1430/1431 Sheet 4 Multiple choice Questions 1-Unipolar, bipolar, and polar encoding
King Saud University College of Computer and Information Sciences Department of Information Technology CAP240 First semester 1430/1431 Sheet 4 Multiple choice Questions 1-Unipolar, bipolar, and polar encoding
Color Image Compression Using Colorization Based On Coding Technique
 Color Image Compression Using Colorization Based On Coding Technique D.P.Kawade 1, Prof. S.N.Rawat 2 1,2 Department of Electronics and Telecommunication, Bhivarabai Sawant Institute of Technology and Research
Color Image Compression Using Colorization Based On Coding Technique D.P.Kawade 1, Prof. S.N.Rawat 2 1,2 Department of Electronics and Telecommunication, Bhivarabai Sawant Institute of Technology and Research
MPEG has been established as an international standard
 1100 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 9, NO. 7, OCTOBER 1999 Fast Extraction of Spatially Reduced Image Sequences from MPEG-2 Compressed Video Junehwa Song, Member,
1100 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 9, NO. 7, OCTOBER 1999 Fast Extraction of Spatially Reduced Image Sequences from MPEG-2 Compressed Video Junehwa Song, Member,
Chapter 10 Basic Video Compression Techniques
 Chapter 10 Basic Video Compression Techniques 10.1 Introduction to Video compression 10.2 Video Compression with Motion Compensation 10.3 Video compression standard H.261 10.4 Video compression standard
Chapter 10 Basic Video Compression Techniques 10.1 Introduction to Video compression 10.2 Video Compression with Motion Compensation 10.3 Video compression standard H.261 10.4 Video compression standard
Speech and Speaker Recognition for the Command of an Industrial Robot
 Speech and Speaker Recognition for the Command of an Industrial Robot CLAUDIA MOISA*, HELGA SILAGHI*, ANDREI SILAGHI** *Dept. of Electric Drives and Automation University of Oradea University Street, nr.
Speech and Speaker Recognition for the Command of an Industrial Robot CLAUDIA MOISA*, HELGA SILAGHI*, ANDREI SILAGHI** *Dept. of Electric Drives and Automation University of Oradea University Street, nr.
Video coding standards
 Video coding standards Video signals represent sequences of images or frames which can be transmitted with a rate from 5 to 60 frames per second (fps), that provides the illusion of motion in the displayed
Video coding standards Video signals represent sequences of images or frames which can be transmitted with a rate from 5 to 60 frames per second (fps), that provides the illusion of motion in the displayed
Motion Video Compression
 7 Motion Video Compression 7.1 Motion video Motion video contains massive amounts of redundant information. This is because each image has redundant information and also because there are very few changes
7 Motion Video Compression 7.1 Motion video Motion video contains massive amounts of redundant information. This is because each image has redundant information and also because there are very few changes
Paulo V. K. Borges. Flat 1, 50A, Cephas Av. London, UK, E1 4AR (+44) PRESENTATION
 Paulo V. K. Borges Flat 1, 50A, Cephas Av. London, UK, E1 4AR (+44) 07942084331 vini@ieee.org PRESENTATION Electronic engineer working as researcher at University of London. Doctorate in digital image/video
Paulo V. K. Borges Flat 1, 50A, Cephas Av. London, UK, E1 4AR (+44) 07942084331 vini@ieee.org PRESENTATION Electronic engineer working as researcher at University of London. Doctorate in digital image/video
An Overview of Video Coding Algorithms
 An Overview of Video Coding Algorithms Prof. Ja-Ling Wu Department of Computer Science and Information Engineering National Taiwan University Video coding can be viewed as image compression with a temporal
An Overview of Video Coding Algorithms Prof. Ja-Ling Wu Department of Computer Science and Information Engineering National Taiwan University Video coding can be viewed as image compression with a temporal
ENCODING OF PREDICTIVE ERROR FRAMES IN RATE SCALABLE VIDEO CODECS USING WAVELET SHRINKAGE. Eduardo Asbun, Paul Salama, and Edward J.
 ENCODING OF PREDICTIVE ERROR FRAMES IN RATE SCALABLE VIDEO CODECS USING WAVELET SHRINKAGE Eduardo Asbun, Paul Salama, and Edward J. Delp Video and Image Processing Laboratory (VIPER) School of Electrical
ENCODING OF PREDICTIVE ERROR FRAMES IN RATE SCALABLE VIDEO CODECS USING WAVELET SHRINKAGE Eduardo Asbun, Paul Salama, and Edward J. Delp Video and Image Processing Laboratory (VIPER) School of Electrical
INTERNATIONAL TELECOMMUNICATION UNION GENERAL ASPECTS OF DIGITAL TRANSMISSION SYSTEMS PULSE CODE MODULATION (PCM) OF VOICE FREQUENCIES
 INTERNATIONAL TELECOMMUNICATION UNION ITU-T G TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU GENERAL ASPECTS OF DIGITAL TRANSMISSION SYSTEMS TERMINAL EQUIPMENTS PULSE CODE MODULATION (PCM) OF VOICE FREQUENCIES
INTERNATIONAL TELECOMMUNICATION UNION ITU-T G TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU GENERAL ASPECTS OF DIGITAL TRANSMISSION SYSTEMS TERMINAL EQUIPMENTS PULSE CODE MODULATION (PCM) OF VOICE FREQUENCIES
A Study of Encoding and Decoding Techniques for Syndrome-Based Video Coding
 MITSUBISHI ELECTRIC RESEARCH LABORATORIES http://www.merl.com A Study of Encoding and Decoding Techniques for Syndrome-Based Video Coding Min Wu, Anthony Vetro, Jonathan Yedidia, Huifang Sun, Chang Wen
MITSUBISHI ELECTRIC RESEARCH LABORATORIES http://www.merl.com A Study of Encoding and Decoding Techniques for Syndrome-Based Video Coding Min Wu, Anthony Vetro, Jonathan Yedidia, Huifang Sun, Chang Wen
AN UNEQUAL ERROR PROTECTION SCHEME FOR MULTIPLE INPUT MULTIPLE OUTPUT SYSTEMS. M. Farooq Sabir, Robert W. Heath and Alan C. Bovik
 AN UNEQUAL ERROR PROTECTION SCHEME FOR MULTIPLE INPUT MULTIPLE OUTPUT SYSTEMS M. Farooq Sabir, Robert W. Heath and Alan C. Bovik Dept. of Electrical and Comp. Engg., The University of Texas at Austin,
AN UNEQUAL ERROR PROTECTION SCHEME FOR MULTIPLE INPUT MULTIPLE OUTPUT SYSTEMS M. Farooq Sabir, Robert W. Heath and Alan C. Bovik Dept. of Electrical and Comp. Engg., The University of Texas at Austin,
BASE-LINE WANDER & LINE CODING
 BASE-LINE WANDER & LINE CODING PREPARATION... 28 what is base-line wander?... 28 to do before the lab... 29 what we will do... 29 EXPERIMENT... 30 overview... 30 observing base-line wander... 30 waveform
BASE-LINE WANDER & LINE CODING PREPARATION... 28 what is base-line wander?... 28 to do before the lab... 29 what we will do... 29 EXPERIMENT... 30 overview... 30 observing base-line wander... 30 waveform
Introduction to Data Conversion and Processing
 Introduction to Data Conversion and Processing The proliferation of digital computing and signal processing in electronic systems is often described as "the world is becoming more digital every day." Compared
Introduction to Data Conversion and Processing The proliferation of digital computing and signal processing in electronic systems is often described as "the world is becoming more digital every day." Compared
Towards More Efficient DSP Implementations: An Analysis into the Sources of Error in DSP Design
 Towards More Efficient DSP Implementations: An Analysis into the Sources of Error in DSP Design Tinotenda Zwavashe 1, Rudo Duri 2, Mainford Mutandavari 3 M Tech Student, Department of ECE, Jawaharlal Nehru
Towards More Efficient DSP Implementations: An Analysis into the Sources of Error in DSP Design Tinotenda Zwavashe 1, Rudo Duri 2, Mainford Mutandavari 3 M Tech Student, Department of ECE, Jawaharlal Nehru
Example: compressing black and white images 2 Say we are trying to compress an image of black and white pixels: CSC310 Information Theory.
 CSC310 Information Theory Lecture 1: Basics of Information Theory September 11, 2006 Sam Roweis Example: compressing black and white images 2 Say we are trying to compress an image of black and white pixels:
CSC310 Information Theory Lecture 1: Basics of Information Theory September 11, 2006 Sam Roweis Example: compressing black and white images 2 Say we are trying to compress an image of black and white pixels:
Compressed-Sensing-Enabled Video Streaming for Wireless Multimedia Sensor Networks Abstract:
 Compressed-Sensing-Enabled Video Streaming for Wireless Multimedia Sensor Networks Abstract: This article1 presents the design of a networked system for joint compression, rate control and error correction
Compressed-Sensing-Enabled Video Streaming for Wireless Multimedia Sensor Networks Abstract: This article1 presents the design of a networked system for joint compression, rate control and error correction
Guidance For Scrambling Data Signals For EMC Compliance
 Guidance For Scrambling Data Signals For EMC Compliance David Norte, PhD. Abstract s can be used to help mitigate the radiated emissions from inherently periodic data signals. A previous paper [1] described
Guidance For Scrambling Data Signals For EMC Compliance David Norte, PhD. Abstract s can be used to help mitigate the radiated emissions from inherently periodic data signals. A previous paper [1] described
DICOM medical image watermarking of ECG signals using EZW algorithm. A. Kannammal* and S. Subha Rani
 126 Int. J. Medical Engineering and Informatics, Vol. 5, No. 2, 2013 DICOM medical image watermarking of ECG signals using EZW algorithm A. Kannammal* and S. Subha Rani ECE Department, PSG College of Technology,
126 Int. J. Medical Engineering and Informatics, Vol. 5, No. 2, 2013 DICOM medical image watermarking of ECG signals using EZW algorithm A. Kannammal* and S. Subha Rani ECE Department, PSG College of Technology,
A QUERY BY EXAMPLE MUSIC RETRIEVAL ALGORITHM
 A QUER B EAMPLE MUSIC RETRIEVAL ALGORITHM H. HARB AND L. CHEN Maths-Info department, Ecole Centrale de Lyon. 36, av. Guy de Collongue, 69134, Ecully, France, EUROPE E-mail: {hadi.harb, liming.chen}@ec-lyon.fr
A QUER B EAMPLE MUSIC RETRIEVAL ALGORITHM H. HARB AND L. CHEN Maths-Info department, Ecole Centrale de Lyon. 36, av. Guy de Collongue, 69134, Ecully, France, EUROPE E-mail: {hadi.harb, liming.chen}@ec-lyon.fr
The H.263+ Video Coding Standard: Complexity and Performance
 The H.263+ Video Coding Standard: Complexity and Performance Berna Erol (bernae@ee.ubc.ca), Michael Gallant (mikeg@ee.ubc.ca), Guy C t (guyc@ee.ubc.ca), and Faouzi Kossentini (faouzi@ee.ubc.ca) Department
The H.263+ Video Coding Standard: Complexity and Performance Berna Erol (bernae@ee.ubc.ca), Michael Gallant (mikeg@ee.ubc.ca), Guy C t (guyc@ee.ubc.ca), and Faouzi Kossentini (faouzi@ee.ubc.ca) Department
Chapter 2. Advanced Telecommunications and Signal Processing Program. E. Galarza, Raynard O. Hinds, Eric C. Reed, Lon E. Sun-
 Chapter 2. Advanced Telecommunications and Signal Processing Program Academic and Research Staff Professor Jae S. Lim Visiting Scientists and Research Affiliates M. Carlos Kennedy Graduate Students John
Chapter 2. Advanced Telecommunications and Signal Processing Program Academic and Research Staff Professor Jae S. Lim Visiting Scientists and Research Affiliates M. Carlos Kennedy Graduate Students John
A Color Gamut Mapping Scheme for Backward Compatible UHD Video Distribution
 A Color Gamut Mapping Scheme for Backward Compatible UHD Video Distribution Maryam Azimi, Timothée-Florian Bronner, and Panos Nasiopoulos Electrical and Computer Engineering Department University of British
A Color Gamut Mapping Scheme for Backward Compatible UHD Video Distribution Maryam Azimi, Timothée-Florian Bronner, and Panos Nasiopoulos Electrical and Computer Engineering Department University of British
Distributed Video Coding Using LDPC Codes for Wireless Video
 Wireless Sensor Network, 2009, 1, 334-339 doi:10.4236/wsn.2009.14041 Published Online November 2009 (http://www.scirp.org/journal/wsn). Distributed Video Coding Using LDPC Codes for Wireless Video Abstract
Wireless Sensor Network, 2009, 1, 334-339 doi:10.4236/wsn.2009.14041 Published Online November 2009 (http://www.scirp.org/journal/wsn). Distributed Video Coding Using LDPC Codes for Wireless Video Abstract
ATSC Standard: Video Watermark Emission (A/335)
 ATSC Standard: Video Watermark Emission (A/335) Doc. A/335:2016 20 September 2016 Advanced Television Systems Committee 1776 K Street, N.W. Washington, D.C. 20006 202-872-9160 i The Advanced Television
ATSC Standard: Video Watermark Emission (A/335) Doc. A/335:2016 20 September 2016 Advanced Television Systems Committee 1776 K Street, N.W. Washington, D.C. 20006 202-872-9160 i The Advanced Television
Optimization of Multi-Channel BCH Error Decoding for Common Cases. Russell Dill Master's Thesis Defense April 20, 2015
 Optimization of Multi-Channel BCH Error Decoding for Common Cases Russell Dill Master's Thesis Defense April 20, 2015 Bose-Chaudhuri-Hocquenghem (BCH) BCH is an Error Correcting Code (ECC) and is used
Optimization of Multi-Channel BCH Error Decoding for Common Cases Russell Dill Master's Thesis Defense April 20, 2015 Bose-Chaudhuri-Hocquenghem (BCH) BCH is an Error Correcting Code (ECC) and is used
WE CONSIDER an enhancement technique for degraded
 1140 IEEE SIGNAL PROCESSING LETTERS, VOL. 21, NO. 9, SEPTEMBER 2014 Example-based Enhancement of Degraded Video Edson M. Hung, Member, IEEE, Diogo C. Garcia, Member, IEEE, and Ricardo L. de Queiroz, Senior
1140 IEEE SIGNAL PROCESSING LETTERS, VOL. 21, NO. 9, SEPTEMBER 2014 Example-based Enhancement of Degraded Video Edson M. Hung, Member, IEEE, Diogo C. Garcia, Member, IEEE, and Ricardo L. de Queiroz, Senior
Measurement of overtone frequencies of a toy piano and perception of its pitch
 Measurement of overtone frequencies of a toy piano and perception of its pitch PACS: 43.75.Mn ABSTRACT Akira Nishimura Department of Media and Cultural Studies, Tokyo University of Information Sciences,
Measurement of overtone frequencies of a toy piano and perception of its pitch PACS: 43.75.Mn ABSTRACT Akira Nishimura Department of Media and Cultural Studies, Tokyo University of Information Sciences,
Figure 2: Original and PAM modulated image. Figure 4: Original image.
 Figure 2: Original and PAM modulated image. Figure 4: Original image. An image can be represented as a 1D signal by replacing all the rows as one row. This gives us our image as a 1D signal. Suppose x(t)
Figure 2: Original and PAM modulated image. Figure 4: Original image. An image can be represented as a 1D signal by replacing all the rows as one row. This gives us our image as a 1D signal. Suppose x(t)
Professor Laurence S. Dooley. School of Computing and Communications Milton Keynes, UK
 Professor Laurence S. Dooley School of Computing and Communications Milton Keynes, UK The Song of the Talking Wire 1904 Henry Farny painting Communications It s an analogue world Our world is continuous
Professor Laurence S. Dooley School of Computing and Communications Milton Keynes, UK The Song of the Talking Wire 1904 Henry Farny painting Communications It s an analogue world Our world is continuous
Department of Electrical & Electronic Engineering Imperial College of Science, Technology and Medicine. Project: Real-Time Speech Enhancement
 Department of Electrical & Electronic Engineering Imperial College of Science, Technology and Medicine Project: Real-Time Speech Enhancement Introduction Telephones are increasingly being used in noisy
Department of Electrical & Electronic Engineering Imperial College of Science, Technology and Medicine Project: Real-Time Speech Enhancement Introduction Telephones are increasingly being used in noisy
International Journal of Engineering Research-Online A Peer Reviewed International Journal
 RESEARCH ARTICLE ISSN: 2321-7758 VLSI IMPLEMENTATION OF SERIES INTEGRATOR COMPOSITE FILTERS FOR SIGNAL PROCESSING MURALI KRISHNA BATHULA Research scholar, ECE Department, UCEK, JNTU Kakinada ABSTRACT The
RESEARCH ARTICLE ISSN: 2321-7758 VLSI IMPLEMENTATION OF SERIES INTEGRATOR COMPOSITE FILTERS FOR SIGNAL PROCESSING MURALI KRISHNA BATHULA Research scholar, ECE Department, UCEK, JNTU Kakinada ABSTRACT The
Extraction Methods of Watermarks from Linearly-Distorted Images to Maximize Signal-to-Noise Ratio. Brandon Migdal. Advisors: Carl Salvaggio
 Extraction Methods of Watermarks from Linearly-Distorted Images to Maximize Signal-to-Noise Ratio By Brandon Migdal Advisors: Carl Salvaggio Chris Honsinger A senior project submitted in partial fulfillment
Extraction Methods of Watermarks from Linearly-Distorted Images to Maximize Signal-to-Noise Ratio By Brandon Migdal Advisors: Carl Salvaggio Chris Honsinger A senior project submitted in partial fulfillment
Design of Fault Coverage Test Pattern Generator Using LFSR
 Design of Fault Coverage Test Pattern Generator Using LFSR B.Saritha M.Tech Student, Department of ECE, Dhruva Institue of Engineering & Technology. Abstract: A new fault coverage test pattern generator
Design of Fault Coverage Test Pattern Generator Using LFSR B.Saritha M.Tech Student, Department of ECE, Dhruva Institue of Engineering & Technology. Abstract: A new fault coverage test pattern generator
DWT Based-Video Compression Using (4SS) Matching Algorithm
 DWT Based-Video Compression Using (4SS) Matching Algorithm Marwa Kamel Hussien Dr. Hameed Abdul-Kareem Younis Assist. Lecturer Assist. Professor Lava_85K@yahoo.com Hameedalkinani2004@yahoo.com Department
DWT Based-Video Compression Using (4SS) Matching Algorithm Marwa Kamel Hussien Dr. Hameed Abdul-Kareem Younis Assist. Lecturer Assist. Professor Lava_85K@yahoo.com Hameedalkinani2004@yahoo.com Department
NUMEROUS elaborate attempts have been made in the
 IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 46, NO. 12, DECEMBER 1998 1555 Error Protection for Progressive Image Transmission Over Memoryless and Fading Channels P. Greg Sherwood and Kenneth Zeger, Senior
IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 46, NO. 12, DECEMBER 1998 1555 Error Protection for Progressive Image Transmission Over Memoryless and Fading Channels P. Greg Sherwood and Kenneth Zeger, Senior
Investigation of Digital Signal Processing of High-speed DACs Signals for Settling Time Testing
 Universal Journal of Electrical and Electronic Engineering 4(2): 67-72, 2016 DOI: 10.13189/ujeee.2016.040204 http://www.hrpub.org Investigation of Digital Signal Processing of High-speed DACs Signals for
Universal Journal of Electrical and Electronic Engineering 4(2): 67-72, 2016 DOI: 10.13189/ujeee.2016.040204 http://www.hrpub.org Investigation of Digital Signal Processing of High-speed DACs Signals for
A Layered Approach for Watermarking In Images Based On Huffman Coding
 A Layered Approach for Watermarking In Images Based On Huffman Coding D. Lalitha Bhaskari 1 P. S. Avadhani 1 M. Viswanath 2 1 Department of Computer Science & Systems Engineering, Andhra University, 2
A Layered Approach for Watermarking In Images Based On Huffman Coding D. Lalitha Bhaskari 1 P. S. Avadhani 1 M. Viswanath 2 1 Department of Computer Science & Systems Engineering, Andhra University, 2
1. INTRODUCTION. Index Terms Video Transcoding, Video Streaming, Frame skipping, Interpolation frame, Decoder, Encoder.
 Video Streaming Based on Frame Skipping and Interpolation Techniques Fadlallah Ali Fadlallah Department of Computer Science Sudan University of Science and Technology Khartoum-SUDAN fadali@sustech.edu
Video Streaming Based on Frame Skipping and Interpolation Techniques Fadlallah Ali Fadlallah Department of Computer Science Sudan University of Science and Technology Khartoum-SUDAN fadali@sustech.edu
Experiment 13 Sampling and reconstruction
 Experiment 13 Sampling and reconstruction Preliminary discussion So far, the experiments in this manual have concentrated on communications systems that transmit analog signals. However, digital transmission
Experiment 13 Sampling and reconstruction Preliminary discussion So far, the experiments in this manual have concentrated on communications systems that transmit analog signals. However, digital transmission
Automatic Commercial Monitoring for TV Broadcasting Using Audio Fingerprinting
 Automatic Commercial Monitoring for TV Broadcasting Using Audio Fingerprinting Dalwon Jang 1, Seungjae Lee 2, Jun Seok Lee 2, Minho Jin 1, Jin S. Seo 2, Sunil Lee 1 and Chang D. Yoo 1 1 Korea Advanced
Automatic Commercial Monitoring for TV Broadcasting Using Audio Fingerprinting Dalwon Jang 1, Seungjae Lee 2, Jun Seok Lee 2, Minho Jin 1, Jin S. Seo 2, Sunil Lee 1 and Chang D. Yoo 1 1 Korea Advanced
Various Applications of Digital Signal Processing (DSP)
 Various Applications of Digital Signal Processing (DSP) Neha Kapoor, Yash Kumar, Mona Sharma Student,ECE,DCE,Gurgaon, India EMAIL: neha04263@gmail.com, yashguptaip@gmail.com, monasharma1194@gmail.com ABSTRACT:-
Various Applications of Digital Signal Processing (DSP) Neha Kapoor, Yash Kumar, Mona Sharma Student,ECE,DCE,Gurgaon, India EMAIL: neha04263@gmail.com, yashguptaip@gmail.com, monasharma1194@gmail.com ABSTRACT:-
COSC3213W04 Exercise Set 2 - Solutions
 COSC313W04 Exercise Set - Solutions Encoding 1. Encode the bit-pattern 1010000101 using the following digital encoding schemes. Be sure to write down any assumptions you need to make: a. NRZ-I Need to
COSC313W04 Exercise Set - Solutions Encoding 1. Encode the bit-pattern 1010000101 using the following digital encoding schemes. Be sure to write down any assumptions you need to make: a. NRZ-I Need to
Selective Intra Prediction Mode Decision for H.264/AVC Encoders
 Selective Intra Prediction Mode Decision for H.264/AVC Encoders Jun Sung Park, and Hyo Jung Song Abstract H.264/AVC offers a considerably higher improvement in coding efficiency compared to other compression
Selective Intra Prediction Mode Decision for H.264/AVC Encoders Jun Sung Park, and Hyo Jung Song Abstract H.264/AVC offers a considerably higher improvement in coding efficiency compared to other compression
Simulation analysis of the transmission gaps influence on the decoding processes in the NS-DM system
 Proceedings of the 11th WSEAS International Conference on CIRCUITS, Agios Nikolaos, Crete Island, Greece, July 23-25, 2007 82 Simulation analysis of the transmission gaps influence on the decoding processes
Proceedings of the 11th WSEAS International Conference on CIRCUITS, Agios Nikolaos, Crete Island, Greece, July 23-25, 2007 82 Simulation analysis of the transmission gaps influence on the decoding processes
PAPER Wireless Multi-view Video Streaming with Subcarrier Allocation
 IEICE TRANS. COMMUN., VOL.Exx??, NO.xx XXXX 200x 1 AER Wireless Multi-view Video Streaming with Subcarrier Allocation Takuya FUJIHASHI a), Shiho KODERA b), Nonmembers, Shunsuke SARUWATARI c), and Takashi
IEICE TRANS. COMMUN., VOL.Exx??, NO.xx XXXX 200x 1 AER Wireless Multi-view Video Streaming with Subcarrier Allocation Takuya FUJIHASHI a), Shiho KODERA b), Nonmembers, Shunsuke SARUWATARI c), and Takashi
Robust 3-D Video System Based on Modified Prediction Coding and Adaptive Selection Mode Error Concealment Algorithm
 International Journal of Signal Processing Systems Vol. 2, No. 2, December 2014 Robust 3-D Video System Based on Modified Prediction Coding and Adaptive Selection Mode Error Concealment Algorithm Walid
International Journal of Signal Processing Systems Vol. 2, No. 2, December 2014 Robust 3-D Video System Based on Modified Prediction Coding and Adaptive Selection Mode Error Concealment Algorithm Walid
Digital Representation
 Chapter three c0003 Digital Representation CHAPTER OUTLINE Antialiasing...12 Sampling...12 Quantization...13 Binary Values...13 A-D... 14 D-A...15 Bit Reduction...15 Lossless Packing...16 Lower f s and
Chapter three c0003 Digital Representation CHAPTER OUTLINE Antialiasing...12 Sampling...12 Quantization...13 Binary Values...13 A-D... 14 D-A...15 Bit Reduction...15 Lossless Packing...16 Lower f s and
Keywords- Cryptography, Frame, Least Significant Bit, Pseudo Random Equations, Text, Video Image, Video Steganography.
 International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 164 High Security Video Steganography Putti DeepthiChandan, Dr. M. Narayana Abstract- Video Steganography is a technique
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 164 High Security Video Steganography Putti DeepthiChandan, Dr. M. Narayana Abstract- Video Steganography is a technique
ECE 5765 Modern Communication Fall 2005, UMD Experiment 10: PRBS Messages, Eye Patterns & Noise Simulation using PRBS
 ECE 5765 Modern Communication Fall 2005, UMD Experiment 10: PRBS Messages, Eye Patterns & Noise Simulation using PRBS modules basic: SEQUENCE GENERATOR, TUNEABLE LPF, ADDER, BUFFER AMPLIFIER extra basic:
ECE 5765 Modern Communication Fall 2005, UMD Experiment 10: PRBS Messages, Eye Patterns & Noise Simulation using PRBS modules basic: SEQUENCE GENERATOR, TUNEABLE LPF, ADDER, BUFFER AMPLIFIER extra basic:
