Edited by M. E. Ghaver
|
|
|
- Angel Shaw
- 5 years ago
- Views:
Transcription
1 SOLVING CIPHER Edited by M. E. Ghaver SECRETS FOR T H E F I R S T T I M E H E R E, T H E S O L U T I O N O F A N U M B E R O F C R Y P T O GRAMS IS E X P L A I N E D - A L S O A TIP ABOUT T H E RADIO CONTEST CIPHER FTENTIMES a cryptogram may be so short that depending, of course, on the relative complexity of the cipher its solution becomes a difficult matter, if not altogether an impossibility. In such cases decipherment can often be materially simplified if a number of cryptograms in the same key are available. With one exception, noted below, all the methods so far discussed in this department have depended upon the analysis of a single cryptogram. In some instances single cryptogram methods may be used with a number of messages, the added effectiveness being due to the increased bulk of material. On the other hand, some of these multiple message methods are peculiarly adapted to a number of cryptograms, not being applicable to the resolution of a single example. A certain insight into multiple cryptogram methods has already been afforded readers of FLYNN'S WEEKLY in the issue of July 3, where a method was given applicable to the solution of a number of transposition cryptograms in the same key. In this article for the first time we will actually consider the solution of a number of cryptograms. The cipher selected for this purpose is one of the numerous variants of the famous Vigenere alphabetic square, being that given by John Wilkins afterward Bishop of Chester on pages 72 to 76, inclusive, of his " Mercury, or the Secret and Swift Messenger," an early work on cryptography published in London in 1641, This form of the cipher uses the same type of alphabet as its famous original, and is identical in its results, but holds one advantage, at least, over it, in that instead of requiring a ready-made table of the whole number of alphabets, it employs a special table, formed of just those alphabets selected by the key word. For example, if the key word TRY be agreed upon, the table will consist of three alphabets, one beginning with each letter of the key. The alphabets used by Wilkins consist of but twenty-four letters, / and V being omitted. For in the English alphabet of that time the letters / and / were used interchangeably, as were also U and V. Here, however, the full twenty-six letter alphabet is employed. (Message alphabet) A B C D E F G 11 I J K L M N 0 F Q R S T U V W X Y Z T T U V W X Y Z A B C D E F G H I J K L M N O P Q R S R R S T U V W X Y Z A B C D E F G H I J K L M N O P Q Y Y Z A B C D E F G H I J K L M N O P Q R S T U V W X (Cipher alphabets) 794
2 Now, to encipher any message, as the short example given at (b), write a letter of the key above each letter of the message, taking both in their order, and repeating the key as the length of the message may require, as shown at (a): (a) Key: TRYT RY TR YTRY (b) Message; MEET ME AT ONCE (c) Cipher: FVCM DC TK MGTC (d) Regrouped: FVCMD CTKMG TC The key letter above each text letter,iow indicates the alphabet in which it is to be enciphered. For example, the first letter of the message, M, is to be enciphered in the T alphabet, its substitute in that alphabet being F, which is accordingly placed below M in line (c). Similarly, the second letter, E, of the message becomes V in the R alphabet. The third letter, also an E, becomes C in the y alphabet; and so on. The cryptogram for MEET ME AT ONCE, with the key TRY, is thus FVCM DC TK MGTC, as shown at (c). As described by Wilkins, the normal word divisions are observed in the cryptogram. In the present day, however, the customary procedure would be to regroup the letters, preferably by fives, as shown at (d). In passing, it must be mentioned that Wilkins also suggests the use of mixed alphabets in this cipher instead of the straight A-to-Z arrangement, and the change of key letter with each word or line instead of with each letter. The resolution of mixed alphabets will he taken up later. (1) JOPTE CGENS (2) OSYIV CHXIV (3) LOETS MUTYE (4) YSBPX SNPMS ( ;) CLEGG DVSVK (6) TVYJJ SAHVV SOLVING CIPHER SECRETS 795 /J 20 NTFDF NUQFZ KHGII HQQMN MHRUY AZRVE To solve this, it is only necessary to write the alphabet all twenty-six letters if required after each cipher letter, taking care to preserve the columnar arrangement, the cryptogram itself constituting the first column. The letters forming any word of the message will then appear in a single column, under the key letter by which it was enciphered. (Key) Z Y X W V U T S R Q P... F G H l J K L M N O P Q... X Y Z.4 B C D /; F G H I... X V Z A B C D A ; F G H I... M N O P Q R S r U V W X... D E F G H I J K L A /... V W X Y Z A B C D A '... Y Z B C D E... R S V U V W X.,. H I J K L M N O P... G n I j K L M.V O... V W X Y Z A B C D... X Y Z A B C D ' F.,. Of course, if a whole line of the crypto gram is enciphered in the same alphabet, or if normal word divisions are observed, decipherment by the above method is still easier. Now that the reader is acquainted with the system, it is well to produce the cryptograms he is expected to decipher. To increase the interest, these cryptograms have been made the captured correspondence of a supposed hand of kidnapers. In these cryptograms, the key letter has been changed with each text letter; also, excepting that a twenty-six letter alphabet has been used, and normal word divisions have not been ohsdrved, the cipher is otherwise exactly like that described by Wilkins. Here ape our cryptograms, six of them, numbered for reference. PPGZD XPOFP VVKTFN DVVYR FAICI VFTFT -y so ss THBTM WXCCD JXPU. TFUCI SGTPH M. GPNLW. QIHIU OJPTH GTPH. PJIKl ELNKM KVVW. -SFRRR KVM. But both the other devices could easily he solved by " running down the alphabet." Suppose, for example, that the key letter he changed with each word, thus: (a) Key: TTTT RR YY TTTT (b) Message : MEET ME AT ONCE (c) Cipher: FXXM DV YR HGVX (d) Regrouped: FXXMD VYRHG VX Now, since this is supposed to be a series of cryptograms in unknown cipher, it cannot be assumed that they are in the same key. Possibly a number of different ciphers have been employed. Again they may be in the same system, hut with different keys. Consequently, before any two or more of the above cryptograms can he combined for solution, it is necessary to know that they are in identical ciphers.
3 796 FLYNN'S WEEKLY If the reader desires he can try each cryptogram individually by the transposition test given in the September 4 issue of FLYNN'S WEEKLY. These tests will eliminate the transposition cipher, and allow us to consider the possibility of substitution ciphers. In this latter class, the substitutes may consist of one, two, three, or more characters. The present cryptograms consist of 34, 31, 25, 34, 35, and 28 letters, respectively. Some of these numbers are not evenly divisible by 2, 3, 4... and consequently we can assume unless substitutes of mixed lengths have been used that at least some of the cryptograms are of the straight letter-for-letter substitution type. Messages enciphered in the same key will often have similar predominating characters or groups of characters. For instance, that cyptograms Nos. 5 and 6 both contain a large number of V's might be pointed out as significant. Predominant groups, however, will receive the bulk of attention here. And to save our readers a few hours of merely routine work, a complete table of all the recurrent groups in all six of the present cryptograms is herewith appended. (1) (2) (3) (4) (s) (6)_ PT SN 10 6 TF FP IS 19 TH XP 16 IV 4-9 CI GTPH HG DV 16 6 W VY 18 2 K M KV FT The above differs from the ordinary table of recurrent groups in that it lists the No. I JOPT ECGE NSNT FDFP No. 2 OSYI VCHX IVNU QFZX gram. Thus, the group PT occurs at the third letter of cryptogram No. i; at the twentieth letter of No. 2; and at the twenty^ eighth letter of No. 4. The reader may easily check them. Were there enough recurrent groups in each cryptogram, they could he tested by the Kasiski method in the usual manner, See FLYNN'S WEEKLY for August 7, Here all such groups happen to he accidentals, which are of no value by the above method. The Kasiski principle, however, is not limited in its application merely to a single cryptogram. It can be used just as well with any number of cryptograms, the recurrent groups of which can be treated exactly as if they occurred in a single specimen. To illustrate this, suppose that we examine the groups found in both No. i and No. 2. Groups (il (2) Intervals Factors PT TF FP IS XP It will he seen that the intervals figured here exactly as if the recurrent groups occurred at their respective numerical places in one and the same cryptogram, instead of two. The largest predominating factor is 4, which suggests a fixed period cipher using four alphabets. By this supposition PT and TF become accidental recurrent groups. At least, we may progress with that assumption. The supposed natural or periodic groups, FP and XP, however, might have resulted from using different keys of the same length, but with certain characters ~ in common. Just what fxirtions of these keys must here be identical, if they are not entirely so, can be found by transcribing the two cryptograms in groups of four, the supposed period. FP and XP are underlined to facilitate the examination PGZD THBT MWXC CDJX P U POFP TFUC ISGT PHM groups repeated in all six cryptograms, and By this arrangement the group FP will not merely those of each individual crypto- be found to occur at the third and fourth
4 letters of the period; and XP at the fourth and first. Consequently, unless these groups are also purely accidental, it may be assumed, tentatively at any rate, that both these cryptograms are in four alphabet ciphers, whose first, third, and fourth alphabets, at least, are identical. Were these cryptograms longer, or with more groups in common, the results by this method might he more convincing. Nevertheless, sufficient have been shown especially since these cryptograms are from the same source, the kidnapers, you know to make it highly probable that both cryptograms have the same key. Just as the presence of identical recurrent groups at regular intervals in a number of cryptograms can thus he taken as evidence of a common key, so the absence of such groups may he considered as indicating different keys. Thus, No. I and No. 3 have only one group, TF, in common. This, occurring at the twelfth letter of No. i and the eighteenth letter of No. 2, gives an interval of 6, suggesting a period of 2, 3, or 6. We already have stronger evidence, however, that No. I has a period of 4. No. 3 would thus seem to he in a different key than No. i. What the length of its key is can be discovered by comparing it by the method already shown with other cryptograms of the series. Having thus explained how it is possible to find whether or not two or more cryptograms of this kind are in the same key, it' is left for the reader to determine for himself how many keys have been employed in the present instance, and what cryptograms have been enciphered in each. These points determined, such cryptograms as are in the same key can he combined for solution. For, as a general rule, SOLVING CIPHER SECRETS 797 WITH OUR There are some points about ciphers from our readers that we must take this opportunity to mention. First of all, do not he disappointed if the cipher you submit is not used at once. Many excellent ciphers are being held until the time when they can he presented to the greater the amount of material in any cipher, the less difficult is it to solve. For example, cryptogram No. i when its thirty-four Characters are divided among its four alphabets, has only eight or nine characters in each alphabet. And No. 2 has only seven or eight characters per alphabet. To resolve even a simple alphabet with so few characters is sometimes a difficult matter. If the similar alphabets of these cryptograms and any others in the same key are combined, however, larger frequency tables of the several alphabets will he available for analysis. To illustrate, the frequency table for alphabet No. i of cryptograms Nos. i and 2 would here consist of tlie first characters in every group of four; these being the letters /, E, N, F, and so on, of No. i, and 0, V, I, Q, and so on, of No. 2. Tables for the other alphabets would be similarly formed. The several alphabets so isolated can he resolved by any desired method: as, for instance, by assigning the value E,T, A... to one of the most used characters, as described in FLYNN'S WEEKLY for August 7, 1926; or by detecting the amount of displacement, or shifting, of "a known cipher alphabet, as shown in the issue of October 2. The actual work of sorting the present six cryptograms according to their keys, and of solving the different alphabets, should afford the reader an hour or so of fascinating entertainment. And don't forget, either, that these cryptograms, deciphered, will reveal the story of the kidnapers. Who will he the first to discover their plot? Send in your solutions; and look for the translations in next Solving Cipher Secrets. READERS the best advantage. Some ciphers will be printed along with special articles dealing with similar systems. Another matter of importance is that your ciphers or inquiries, to receive attention, must always he accompanied with your correct name and address. If you prefer,
5 798 FLYNN'S W E E K L Y your name will not be printed in the magazine. But unsigned, or anonymous, communications will not be considered. In this connection a number of interesting unsigned ciphers have been received. One of these was based on the wigwag alphabet. Another, from Southington, Connecticut, used false word divisions. These, and others like them, we are sure, would interest our readers. We regret that we cannot publish them. Finally, we have been in receipt of a number of insistent requests that we provide an adequate means of placing those interested in cryptography in contact with each other. After a careful consideration of all the ideas advanced as to how this could best be done, we believe that the most feasible plan, for the present at least, would he to list in these columns the names and addresses of those who desire to correspond on the subject of cryptography. How does this idea strike you? If you given the female cipher fans anything particularly adapted to their intuitions. Here is a cryptic message which was smuggled out of prison by a woman to let her friends know what to send her in aiding her to escape. Let's see what the ladies can make of it! MALCOLM DEAN MILLER, M.D. Akron, Ohio. CIPHER No. 7 (Malcplm Dean Miller, M.D.): Metol 9 grains Hydroquinone 38 grains Sodium sulphite, dry... 60s grains Sodium carbonate, dry 800 grains Water 20 ounces " Imogene " The next cipher, though easy, is, nevertheless, not without interest. Having guessed at a word of the message, try to discover the plan of the alphabet. It is to a famous statement of a celebrated author that Mr. Duree (Los Angeles, California) refers in his message. Our correspondent says this cipher is sometimes used by bootleggers hack in the effete East. CIPHER No. 8 (Mumon Duree): l is is would like to have your name on such a list, write us at once to that effect. Whether or not this plan is put into operation will depend upon the enthusiasm with Avhich it is received by our readers. Now that these affairs are all cleared away, we can place some readers' ciphers before you. And good ones they are, too! In No. 7 photographic fans will recognize the formula of a well known developer. Innocent enough, apparently, it has yet been bent to the purposes of cryptic communication. This is different from anything we have yet printed. Read Dr. Miller's letter, and try to find the meaning of the cipher: DEAR SIR : Although your department is most interesting, it has occurred to me that you have never Mr. Goldman, Cleveland, Ohio, originator of No. 9, saj's that his system can be learned in an hour's time. He has attempted to make an undecipherable system. Will it get by the enterprising readers of FLYNN'S WEEKLY? CIPHER No. 9 (B. Goldman) : EJ GEBUF XEPIQLEFIC GEBIQEC SQUZIJMEH SEP NEBILEF VO BEM VEMITEPIKUBAKIF DEPICEF,.WIS EJ TEFF SEGIBES ZEPIV GEBUF OVIS PEMIF PUFEQ PEM NEF BEMIC EJ XEJIKK GEBUF SEP SEQUZ BEHIBEJIM. The solutions to all the ciphers in this issue will he given in next Solving Cipher Secrets. Don't fail to see it. In the meantime, try your skill, and send us your solutions. ABOUT THE RADIO CONTEST CIPHER A complete explanation, with special method of solution, of Mr. C. A. Castle's Radio Cipher, which wa s No. 3 in the October 2 issue of FLYNI r's WEEKLY, will
6 SOLVING CIPHER SECRETS 799 be given in the next installment of this department. No method of solving this type of cipher has yet been published in these columns. In fact, to discover how his cipher could he solved was one of the reasons that prompted Mr. Castle to offer the seventyfive-dollar radio set. Now we really anticipate some solutions concerned, but they are the first six letters of the key. They are the key to tlie next six letters of the cipher, which in turn are the key to the following six. The message may be deciphered by using a table, or by writing the cipher under itself, six places to the right, subtracting the numerical values of the key from those of the letters of the cipher (adding 26 where necessary), and changing the resulting differences into letters of the message. To illustrate: F R J P A C K N 0 H Z F T D VV.., 6 is I I 14 IS i I I S 22 s E V E R Y C I P H.., Message: Every cipher formed on this plan carries its own key and is its own key. There is nothing to remember except the general principle and the numerical order of the letters of the alphabet. to Mr. Castle's cipher. And if the expected list of solvers actually materializes it will be printed in an early issue, naming the fortunate winner. Look for it. Here are the solutions to the remaining ciphers of the October 2 issue: Cipher No. i. Key: L B. Message: We expect to hold up the messenger Wednesday noon. Be ready to act as advised. Cipher No. 2. Key: 0 Z. Message: We leave to-night for San Francisco. Meet us at Jim's place, and bring the money with you. No. 4 (R. M. Packard) was an ingenious autokey cipher, using the straight x-to-26, A-to-Z alphabet. Mr. Packard's own explanation of his system is appended: This is a variation of the Gronsfeld cipher. No. 5 (Paul Napier), like Nos. i and 2, used the digraph table, without, however, including the dash or word space. Accordingly, his alphabets used but twentysix characters, the right-hand column and the bottom row of the table being disregarded. Mr. Napier's message is based on a statement in BuUivant's hook, mentioned in the preceding article. Its solution is presented herewith. Key: K S. Message: This cipher is based on a system of digraphs. It was used by a well known European country. As far as I know, it is still used. In Mr. Levine's, No. 6, we have a remarkably simple and efficacious method of combining two messages in the same cryptogram. This cipher is based on the following two alphabets: A B c D E F G H I J K L M I S I I N 0 P Q R s T U V w X Y Z 14 I S : , using letters for key and cipher, and extending your Gronsfeld table to the full alphabet, but differing from it by one letter in every place, and giving results equivalent to adding the numerical values of the letters of the key to those of the letters of the message, the numerical value of each letter being.its order in the alphabet. The whole cipher is the key. The first six letters are nulls as far as the message is To illustrate the method of encipherment, take the first letters of the two present messages, C (29) of the first message, COME HERE, and S (19) of the second message, STAY AW.AY. The substitute for these two letters is 24 5, one of which numbers (24) is half the sum of 29 and 19, and the other (5) the difference between this
7 800 FLYNN'S W E E K L Y 24 and either 29 or 19. Mr. Levine expresses this relation algebraically, thus: 2:-l-y = 2g x y=ig 2X = 48 3: =24 y = In deciphering, the numbers must be taken in pairs. To get the first message, COME HERE, add the numbers of each pair. The sums will indicate the letters in the 27-to- 52 alphabet. The second message, STAY AWAY, is deciphered by taking the differences between the numbers of each pair, these indicating letters in the i-to-26 alphabet. Cryptogram: ^2 10^2 20 ig Sums; 2g Message No. i: C O M E... Differences: ig 20 i 23 Message No. 2: S T A Y... A system of this kind offers the advantage of sending a real and a supposed message in the same cryptogram. Should the cryptogram be intercepted, suspicion might be diverted by explaining the supposed message. The real message might in this way escape detection. Incidentally, fractions could be avoided in this cipher by using only the even numbers from 2 to 104. Ingenious cipher fans will find a thousand and one occasions in which a cryptogram of this sort may be useful. Prying eyes are likely to accept the supposed message as the ultimate one and neglect further attempts to read it. Without having achieved an indecipherable cipher, its user may have accomplished similar ends. No. 7 was in the simple substitution alphabet given in the next column, having been formed on the key word, CRYPT, in accordance with the following method: In preparing an alphabet of this kind, first write down the selected key word. Then below it, in lines of the same length, place the remaining letters of the alphabet, forming a number of columns equal to the number of letters in the particular key word. Now, take the columns so formed downward, and from left to right, as shown in the subjoined cipher alphabet, where each s text letter is represented in cipher by the letter directly below it: C R Y P T A B D E F G H I J K L M N O Q S U V W X Z., Text: A B C D E F G H I J K L M Cipher: C A G L S Z R B H M U Y D Text: N O P Q R S T U V W X Y Z Cipher : I N V P E J O W T F K Q X Using this alphabet, our crypt becomes: Wicked iceman.pleads guilty; admits having stolen costly nickel-plated bucket while honest owners busily played casino near by. The word crypt is here adapted from puzzledom, where it is applied to the kind of cipher just given, and which we know as a normally spaced, literal, simple substitution cipher. Most crypts also employ an unusual wording of the message to make decipherment more difficult. In our own example, for instance, you will note that no short words, which are usually easy to identify, have been employed. Further, no word uses the same letter twice. Words of any and all lengths can be used in the same crypt. We have used all six-letter words for purely fanciful reasons. Our alphabet was based on a key word. Any other kind of literal alphabet is permissible in a crypt. A total of twenty-seven solutions make up our list of August 7 solvers. The most complete set of solutions was sent in by Mr. Winsor, who walked off with all but No. 3. The arrangement indicates the order in which solutions were submitted, and has no other signification. Philip Bosso, New York, N. Y. (i). Charles C. Fulton, Omaha, Nebraska (1-2). Richard A. Miller, Ridgway, Illinois (i ). Paul A. Napier, Louisville, Kentucky (1-7). Charles P. Winsor, Boston, Massachusetts ( ). M. Walker, Akron, Ohio ( ). Arthur Bellamy, Boston, Massachusetts ( ). A. P. Schmutz, Philadelphia, Pennsylvania (1-2-7). The September 4 solvers' list, if com-. piled in time, will be printed in next Solving Cipher Secrets. 10 F W
PART FOUR. Polyalphabetic Substitution Systems PERIODIC POLYALPHABETIC SUBSTITUTION SYSTEMS
 PART FOUR Polyalphabetic Substitution Systems PERIODIC POLYALPHABETIC SUBSTITUTION SYSTEMS CHAPTER 8 Section I Characteristics of Periodic Systems 8-1. Types of Polyalphabetic Systems All the substitution
PART FOUR Polyalphabetic Substitution Systems PERIODIC POLYALPHABETIC SUBSTITUTION SYSTEMS CHAPTER 8 Section I Characteristics of Periodic Systems 8-1. Types of Polyalphabetic Systems All the substitution
PART FIVE. Transposition Systems TYPES OF TRANSPOSITION SYSTEMS
 PART FIVE Transposition Systems TYPES OF TRANSPOSITION SYSTEMS CHAPTER 11 11-1. Nature of Transposition Transposition systems are fundamentally different from substitution systems. In substitution systems,
PART FIVE Transposition Systems TYPES OF TRANSPOSITION SYSTEMS CHAPTER 11 11-1. Nature of Transposition Transposition systems are fundamentally different from substitution systems. In substitution systems,
Institute of Southern Punjab, Multan
 Institute of Southern Punjab, Multan Network Security Substitution Techniques Lecture#4 Mazhar Hussain E-mail: mazhar.hussain@isp.edu.pk Lecture 4: Substitution Techniques Polybius Cipher Playfair Cipher
Institute of Southern Punjab, Multan Network Security Substitution Techniques Lecture#4 Mazhar Hussain E-mail: mazhar.hussain@isp.edu.pk Lecture 4: Substitution Techniques Polybius Cipher Playfair Cipher
Sherlock Holmes and the adventures of the dancing men
 Sherlock Holmes and the adventures of the dancing men Kseniya Garaschuk May 30, 2013 1 Overview Cryptography (from Greek for hidden, secret ) is the practice and study of hiding information. A cipher is
Sherlock Holmes and the adventures of the dancing men Kseniya Garaschuk May 30, 2013 1 Overview Cryptography (from Greek for hidden, secret ) is the practice and study of hiding information. A cipher is
Appendix Cryptograms
 Fall 2006 Chris Christensen MAT/CSC 483 Appendix Cryptograms Here is a more detailed discussion of the history and techniques for solution of aristocrats and patristocrats (the generic term for them is
Fall 2006 Chris Christensen MAT/CSC 483 Appendix Cryptograms Here is a more detailed discussion of the history and techniques for solution of aristocrats and patristocrats (the generic term for them is
The Tentatve List of Enigma and Other Machine Usages, formatted by Tony Sale. (c) July March l945 page 1
 30 March l945 page 1 TENTATIVE LIST OF ENIGMA AND OTHER MACHINE USAGES Contents 1. Naval Enigma. 2. German Army and Air Force Enigma (including a few other miscellaneous devices). 3. Commercial Type Machines.
30 March l945 page 1 TENTATIVE LIST OF ENIGMA AND OTHER MACHINE USAGES Contents 1. Naval Enigma. 2. German Army and Air Force Enigma (including a few other miscellaneous devices). 3. Commercial Type Machines.
Lesson 25: Solving Problems in Two Ways Rates and Algebra
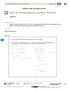 : Solving Problems in Two Ways Rates and Algebra Student Outcomes Students investigate a problem that can be solved by reasoning quantitatively and by creating equations in one variable. They compare the
: Solving Problems in Two Ways Rates and Algebra Student Outcomes Students investigate a problem that can be solved by reasoning quantitatively and by creating equations in one variable. They compare the
A reprint from American Scientist
 A reprint from American Scientist the magazine of Sigma Xi, The Scientific Research Society This reprint is provided for personal and noncommercial use. For any other use, please send a request to Permissions,
A reprint from American Scientist the magazine of Sigma Xi, The Scientific Research Society This reprint is provided for personal and noncommercial use. For any other use, please send a request to Permissions,
IF MONTY HALL FALLS OR CRAWLS
 UDK 51-05 Rosenthal, J. IF MONTY HALL FALLS OR CRAWLS CHRISTOPHER A. PYNES Western Illinois University ABSTRACT The Monty Hall problem is consistently misunderstood. Mathematician Jeffrey Rosenthal argues
UDK 51-05 Rosenthal, J. IF MONTY HALL FALLS OR CRAWLS CHRISTOPHER A. PYNES Western Illinois University ABSTRACT The Monty Hall problem is consistently misunderstood. Mathematician Jeffrey Rosenthal argues
Math: Fractions and Decimals 105
 Math: Fractions and Decimals 105 Many students face fractions with trepidation; they re too hard, I don t understand. If this is you, there is no better tool to bring yourself back up to speed than a tape
Math: Fractions and Decimals 105 Many students face fractions with trepidation; they re too hard, I don t understand. If this is you, there is no better tool to bring yourself back up to speed than a tape
FOR OFFICIAL USE ONLY
 *FM 34-40-2 FIELD MANUAL NO 34-40-2 HEADQUARTERS DEPARTMENT OF THE ARMY Washington, DC, 13 September 1990 FOR OFFICIAL USE ONLY i ii iii PREFACE This field manual is intended as a training text in basic
*FM 34-40-2 FIELD MANUAL NO 34-40-2 HEADQUARTERS DEPARTMENT OF THE ARMY Washington, DC, 13 September 1990 FOR OFFICIAL USE ONLY i ii iii PREFACE This field manual is intended as a training text in basic
Breaking the Enigma. Dmitri Gabbasov. June 2, 2015
 Breaking the Enigma Dmitri Gabbasov June 2, 2015 1 Introduction Enigma was an electro-mechanical machine that was used before and during the World War II by Germany to encrypt and decrypt secret messages.
Breaking the Enigma Dmitri Gabbasov June 2, 2015 1 Introduction Enigma was an electro-mechanical machine that was used before and during the World War II by Germany to encrypt and decrypt secret messages.
Student Performance Q&A: 2001 AP Music Theory Free-Response Questions
 Student Performance Q&A: 2001 AP Music Theory Free-Response Questions The following comments are provided by the Chief Faculty Consultant, Joel Phillips, regarding the 2001 free-response questions for
Student Performance Q&A: 2001 AP Music Theory Free-Response Questions The following comments are provided by the Chief Faculty Consultant, Joel Phillips, regarding the 2001 free-response questions for
Playfair Cipher. From the earliest forms of stenography to the most advanced forms of encryption, the
 Baldwin 1 Erin Baldwin Dr. Bruff FYWS Cryptology October 27, 2010 Playfair Cipher From the earliest forms of stenography to the most advanced forms of encryption, the field of cryptography has advanced
Baldwin 1 Erin Baldwin Dr. Bruff FYWS Cryptology October 27, 2010 Playfair Cipher From the earliest forms of stenography to the most advanced forms of encryption, the field of cryptography has advanced
Note: Please use the actual date you accessed this material in your citation.
 MIT OpenCourseWare http://ocw.mit.edu 18.06 Linear Algebra, Spring 2005 Please use the following citation format: Gilbert Strang, 18.06 Linear Algebra, Spring 2005. (Massachusetts Institute of Technology:
MIT OpenCourseWare http://ocw.mit.edu 18.06 Linear Algebra, Spring 2005 Please use the following citation format: Gilbert Strang, 18.06 Linear Algebra, Spring 2005. (Massachusetts Institute of Technology:
Lecture 8: Cracking the Codes based on Tony Sale s Codes & Ciphers Web Page. History of Computing. Today s Topics. History of Computing Cipher Systems
 Lecture 8: Cracking the Codes based on Tony Sale s Codes & Ciphers Web Page Today s Topics Cipher Systems Substitution Ciphers Cracking Caesar s Cipher Polyalphabetic Substitution The Enigma Machine Rotors,
Lecture 8: Cracking the Codes based on Tony Sale s Codes & Ciphers Web Page Today s Topics Cipher Systems Substitution Ciphers Cracking Caesar s Cipher Polyalphabetic Substitution The Enigma Machine Rotors,
Overview. Teacher s Manual and reproductions of student worksheets to support the following lesson objective:
 Overview Lesson Plan #1 Title: Ace it! Lesson Nine Attached Supporting Documents for Plan #1: Teacher s Manual and reproductions of student worksheets to support the following lesson objective: Find products
Overview Lesson Plan #1 Title: Ace it! Lesson Nine Attached Supporting Documents for Plan #1: Teacher s Manual and reproductions of student worksheets to support the following lesson objective: Find products
Key Concepts. General Rules
 numbers This handout explains general rules for using numbers in academic writing. Note: Although the most common applications are covered, reference your style manual for specific formatting instructions.
numbers This handout explains general rules for using numbers in academic writing. Note: Although the most common applications are covered, reference your style manual for specific formatting instructions.
Ciphers that Substitute Symbols
 Fall 2006 Chris Christensen MAT/CSC 483 Ciphers that Substitute Symbols I Δ ℵ Ω Δ ℵ Some historical simple substitution ciphers substitute symbols for plaintext letters. The ciphertext then looks less
Fall 2006 Chris Christensen MAT/CSC 483 Ciphers that Substitute Symbols I Δ ℵ Ω Δ ℵ Some historical simple substitution ciphers substitute symbols for plaintext letters. The ciphertext then looks less
LECTURE NOTES ON Classical Cryptographic Techniques ( Substitution Ciphers System)
 Department of Software The University of Babylon LECTURE NOTES ON Classical Cryptographic Techniques ( Substitution Ciphers System) By College of Information Technology, University of Babylon, Iraq Samaher@itnet.uobabylon.edu.iq
Department of Software The University of Babylon LECTURE NOTES ON Classical Cryptographic Techniques ( Substitution Ciphers System) By College of Information Technology, University of Babylon, Iraq Samaher@itnet.uobabylon.edu.iq
Math Released Item Grade 5. Whole Number and Fraction Part 0542-M02399
 Math Released Item 2017 Grade 5 Whole Number and Fraction Part 0542-M02399 Anchor Set A1 A10 With Annotations Prompt 0542-M02399 - Rubric Part A Score Description Student response includes the following
Math Released Item 2017 Grade 5 Whole Number and Fraction Part 0542-M02399 Anchor Set A1 A10 With Annotations Prompt 0542-M02399 - Rubric Part A Score Description Student response includes the following
Substitution cipher. Contents
 Substitution cipher In cryptography, a substitution cipher is a method of encryption by which units of plaintext are replaced with ciphertext according to a regular system; the "units" may be single letters
Substitution cipher In cryptography, a substitution cipher is a method of encryption by which units of plaintext are replaced with ciphertext according to a regular system; the "units" may be single letters
Immanuel Kant Critique of Pure Reason
 Immanuel Kant Critique of Pure Reason THE A PRIORI GROUNDS OF THE POSSIBILITY OF EXPERIENCE THAT a concept, although itself neither contained in the concept of possible experience nor consisting of elements
Immanuel Kant Critique of Pure Reason THE A PRIORI GROUNDS OF THE POSSIBILITY OF EXPERIENCE THAT a concept, although itself neither contained in the concept of possible experience nor consisting of elements
CPSC 121: Models of Computation. Module 1: Propositional Logic
 CPSC 121: Models of Computation Module 1: Propositional Logic Module 1: Propositional Logic By the start of the class, you should be able to: Translate back and forth between simple natural language statements
CPSC 121: Models of Computation Module 1: Propositional Logic Module 1: Propositional Logic By the start of the class, you should be able to: Translate back and forth between simple natural language statements
Unit Four Answer Keys
 Multiplication, Division & Fractions Unit Four Unit Four Answer Keys Session Blacklines A.., Unit Four Pre-Assessment Responses will vary. example example a b Sketches will vary. Example: a, Sketches will
Multiplication, Division & Fractions Unit Four Unit Four Answer Keys Session Blacklines A.., Unit Four Pre-Assessment Responses will vary. example example a b Sketches will vary. Example: a, Sketches will
Code-makers & Codebreakers. Substitution ciphers and frequency analysis
 Code-makers & Codebreakers Substitution ciphers and frequency analysis Introductiion to Substiitutiion Ciiphers Author: Will Mitchell william.mitchell@ic.ac.uk A substitution cipher replaces each letter
Code-makers & Codebreakers Substitution ciphers and frequency analysis Introductiion to Substiitutiion Ciiphers Author: Will Mitchell william.mitchell@ic.ac.uk A substitution cipher replaces each letter
The Historian and Archival Finding Aids
 Georgia Archive Volume 5 Number 1 Article 7 January 1977 The Historian and Archival Finding Aids Michael E. Stevens University of Wisconsin Madison Follow this and additional works at: https://digitalcommons.kennesaw.edu/georgia_archive
Georgia Archive Volume 5 Number 1 Article 7 January 1977 The Historian and Archival Finding Aids Michael E. Stevens University of Wisconsin Madison Follow this and additional works at: https://digitalcommons.kennesaw.edu/georgia_archive
Bite Size Brownies. Designed by: Jonathan Thompson George Mason University, COMPLETE Math
 Bite Size Brownies Designed by: Jonathan Thompson George Mason University, COMPLETE Math The Task Mr. Brown E. Pan recently opened a new business making brownies called The Brown E. Pan. On his first day
Bite Size Brownies Designed by: Jonathan Thompson George Mason University, COMPLETE Math The Task Mr. Brown E. Pan recently opened a new business making brownies called The Brown E. Pan. On his first day
Hangman. 2.1 How to Guard a Secret?
 2 Hangman At a trial a prisoner is sentenced to death by the judge. The verdict reads You will be executed next week, but the day on which you will be executed will be a surprise to you. The prisoner reasons
2 Hangman At a trial a prisoner is sentenced to death by the judge. The verdict reads You will be executed next week, but the day on which you will be executed will be a surprise to you. The prisoner reasons
452 AMERICAN ANTHROPOLOGIST [N. S., 21, 1919
 452 AMERICAN ANTHROPOLOGIST [N. S., 21, 1919 Nubuloi Songs. C. R. Moss and A. L. Kroeber. (University of California Publications in American Archaeology and Ethnology, vol. 15, no. 2, pp. 187-207, May
452 AMERICAN ANTHROPOLOGIST [N. S., 21, 1919 Nubuloi Songs. C. R. Moss and A. L. Kroeber. (University of California Publications in American Archaeology and Ethnology, vol. 15, no. 2, pp. 187-207, May
Student Performance Q&A:
 Student Performance Q&A: 2004 AP English Language & Composition Free-Response Questions The following comments on the 2004 free-response questions for AP English Language and Composition were written by
Student Performance Q&A: 2004 AP English Language & Composition Free-Response Questions The following comments on the 2004 free-response questions for AP English Language and Composition were written by
1- Do you see the small symbol on A? If this sign sits on a letter, the letter will be pronounced as /æ/ in dad.
 160 Lessons of Persian Week 1 Are you interested in Farsi? Here' 's the best step by step online class that starts with Farsi alphabet.have problems listening to the audio files? Download one of these:
160 Lessons of Persian Week 1 Are you interested in Farsi? Here' 's the best step by step online class that starts with Farsi alphabet.have problems listening to the audio files? Download one of these:
THINKING AT THE EDGE (TAE) STEPS
 12 THE FOLIO 2000-2004 THINKING AT THE EDGE (TAE) STEPS STEPS 1-5 : SPEAKING FROM THE FELT SENSE Step 1: Let a felt sense form Choose something you know and cannot yet say, that wants to be said. Have
12 THE FOLIO 2000-2004 THINKING AT THE EDGE (TAE) STEPS STEPS 1-5 : SPEAKING FROM THE FELT SENSE Step 1: Let a felt sense form Choose something you know and cannot yet say, that wants to be said. Have
Guidelines for Contributors to Critical Horizons
 Guidelines for Contributors to Critical Horizons Please follow these guidelines when you first submit your article for consideration by the journal Editors. If accepted, we will send you more detailed
Guidelines for Contributors to Critical Horizons Please follow these guidelines when you first submit your article for consideration by the journal Editors. If accepted, we will send you more detailed
A Bibliography of Bagpipe Music
 Roderick Cannon s A Bibliography of Bagpipe Music John Donald Publishers Ltd Edinburgh 1980 An update by Geoff Hore 2008 The writing in black font is from A Bibliography of Bagpipe Music. The update comments
Roderick Cannon s A Bibliography of Bagpipe Music John Donald Publishers Ltd Edinburgh 1980 An update by Geoff Hore 2008 The writing in black font is from A Bibliography of Bagpipe Music. The update comments
Blueline, Linefree, Accuracy Ratio, & Moving Absolute Mean Ratio Charts
 INTRODUCTION This instruction manual describes for users of the Excel Standard Celeration Template(s) the features of each page or worksheet in the template, allowing the user to set up and generate charts
INTRODUCTION This instruction manual describes for users of the Excel Standard Celeration Template(s) the features of each page or worksheet in the template, allowing the user to set up and generate charts
Sandwich. Reuben BLT. Egg salad. Roast beef
 3.2 Writing Expressions represents an unknown quantity? How can you write an expression that 1 ACTIVITY: Ordering Lunch Work with a partner. You use a $20 bill to buy lunch at a café. You order a sandwich
3.2 Writing Expressions represents an unknown quantity? How can you write an expression that 1 ACTIVITY: Ordering Lunch Work with a partner. You use a $20 bill to buy lunch at a café. You order a sandwich
Chapter 3 Digital Data
 Chapter 3 Digital Data So far, chapters 1 and 2 have dealt with audio and video signals, respectively. Both of these have dealt with analog waveforms. In this chapter, we will discuss digital signals in
Chapter 3 Digital Data So far, chapters 1 and 2 have dealt with audio and video signals, respectively. Both of these have dealt with analog waveforms. In this chapter, we will discuss digital signals in
MAT Practice (solutions) 1. Find an algebraic formula for a linear function that passes through the points ( 3, 7) and (6, 1).
 MAT 110 - Practice (solutions) 1. Find an algebraic formula for a linear function that passes through the points ( 3, 7) and (6, 1). Answer: y = 2 3 + 5 2. Let f(x) = 8x 120 (a) What is the y intercept
MAT 110 - Practice (solutions) 1. Find an algebraic formula for a linear function that passes through the points ( 3, 7) and (6, 1). Answer: y = 2 3 + 5 2. Let f(x) = 8x 120 (a) What is the y intercept
Student Name: Parent Signature:
 Entering 5 th Grade Summer Packet Student Name: Parent Signature: Dear Parents, This packet is intended to help students stay strong in the academic material we have covered this year. It is an optional
Entering 5 th Grade Summer Packet Student Name: Parent Signature: Dear Parents, This packet is intended to help students stay strong in the academic material we have covered this year. It is an optional
AP English Literature 1999 Scoring Guidelines
 AP English Literature 1999 Scoring Guidelines The materials included in these files are intended for non-commercial use by AP teachers for course and exam preparation; permission for any other use must
AP English Literature 1999 Scoring Guidelines The materials included in these files are intended for non-commercial use by AP teachers for course and exam preparation; permission for any other use must
Algebra I Module 2 Lessons 1 19
 Eureka Math 2015 2016 Algebra I Module 2 Lessons 1 19 Eureka Math, Published by the non-profit Great Minds. Copyright 2015 Great Minds. No part of this work may be reproduced, distributed, modified, sold,
Eureka Math 2015 2016 Algebra I Module 2 Lessons 1 19 Eureka Math, Published by the non-profit Great Minds. Copyright 2015 Great Minds. No part of this work may be reproduced, distributed, modified, sold,
Compare/ Contrast Essay
 Mrs. Dewey Compare/ Contrast Essay The how-to s Step Two Brainstorm how they re the same On this page, write everything you can that describes how the two things are similar or the same. Don t worry about
Mrs. Dewey Compare/ Contrast Essay The how-to s Step Two Brainstorm how they re the same On this page, write everything you can that describes how the two things are similar or the same. Don t worry about
Exploring the Enigma [The MATH Connection]
![Exploring the Enigma [The MATH Connection] Exploring the Enigma [The MATH Connection]](/thumbs/93/112298684.jpg) Exploring the Enigma [The MATH Connection] by Claire Ellis, from Issue 34 of PLUS Magazine As long ago as the Ancient Greeks, warring armies have encrypted their communications in an attempt to keep their
Exploring the Enigma [The MATH Connection] by Claire Ellis, from Issue 34 of PLUS Magazine As long ago as the Ancient Greeks, warring armies have encrypted their communications in an attempt to keep their
GCSE MARKING SCHEME AUTUMN 2017 GCSE MATHEMATICS NUMERACY UNIT 1 - INTERMEDIATE TIER 3310U30-1. WJEC CBAC Ltd.
 GCSE MARKING SCHEME AUTUMN 2017 GCSE MATHEMATICS NUMERACY UNIT 1 - INTERMEDIATE TIER 3310U30-1 INTRODUCTION This marking scheme was used by WJEC for the 2017 examination. It was finalised after detailed
GCSE MARKING SCHEME AUTUMN 2017 GCSE MATHEMATICS NUMERACY UNIT 1 - INTERMEDIATE TIER 3310U30-1 INTRODUCTION This marking scheme was used by WJEC for the 2017 examination. It was finalised after detailed
CROATIAN OPEN COMPETITION IN INFORMATICS. 6 th ROUND
 CROATIAN OPEN COMPETITION IN INFORMATICS 6 th ROUND COCI 2009/2010 Contest #6 - March 20, 2010 Task KAJAK 1 second / 2 MB / 0 points Mirko and Slavko are sports commentators on a local kayaking competition.
CROATIAN OPEN COMPETITION IN INFORMATICS 6 th ROUND COCI 2009/2010 Contest #6 - March 20, 2010 Task KAJAK 1 second / 2 MB / 0 points Mirko and Slavko are sports commentators on a local kayaking competition.
US_Math 4 1. Operations and Algebraic Thinking 4.OA 2. Number and Operations in Base Ten 4.NBT 3. Number and Operations - Fractions 4.
 US_Math 4 1. Operations and Algebraic Thinking 4.OA 1.1 Multiplication of Whole Numbers 4.OA 1.2 Division of Whole Numbers 4.OA 1.3 Factors and Multiples 4.OA 2. Number and Operations in Base Ten 4.NBT
US_Math 4 1. Operations and Algebraic Thinking 4.OA 1.1 Multiplication of Whole Numbers 4.OA 1.2 Division of Whole Numbers 4.OA 1.3 Factors and Multiples 4.OA 2. Number and Operations in Base Ten 4.NBT
CHAPTER V. Of Fugues in General.
 CHAPTER V 21 Of Fugues in General.! The Fugue is a kind of Composition where the following Part repeats some notes of the former by the same Intervals and by the same Species of whole or half Tones, and
CHAPTER V 21 Of Fugues in General.! The Fugue is a kind of Composition where the following Part repeats some notes of the former by the same Intervals and by the same Species of whole or half Tones, and
Kaytee s Contest Problem https://www.nctm.org/pows/
 Pre-Algebra PoW Packet Kaytee s Contest Problem 16004 https://www.nctm.org/pows/ Welcome! This packet contains a copy of the problem, the answer check, our solutions, some teaching suggestions, and samples
Pre-Algebra PoW Packet Kaytee s Contest Problem 16004 https://www.nctm.org/pows/ Welcome! This packet contains a copy of the problem, the answer check, our solutions, some teaching suggestions, and samples
The Bletchley Park 1944 Cryptographic Dictionary formatted by Tony Sale (c) 2001
 EDITORIAL NOTE It seems desirable to point out that this present edition of the Cryptographic Dictionary is not as complete or as useful, or even, perhaps, as accurate, as such a work of reference should
EDITORIAL NOTE It seems desirable to point out that this present edition of the Cryptographic Dictionary is not as complete or as useful, or even, perhaps, as accurate, as such a work of reference should
North Carolina Standard Course of Study - Mathematics
 A Correlation of To the North Carolina Standard Course of Study - Mathematics Grade 4 A Correlation of, Grade 4 Units Unit 1 - Arrays, Factors, and Multiplicative Comparison Unit 2 - Generating and Representing
A Correlation of To the North Carolina Standard Course of Study - Mathematics Grade 4 A Correlation of, Grade 4 Units Unit 1 - Arrays, Factors, and Multiplicative Comparison Unit 2 - Generating and Representing
Circle of Fifths - Introduction:
 Circle of Fifths - Introduction: I don t consider myself a musician, although I enjoy music, and I don t count myself as an organist, but thoroughly enjoy playing the organ, which I first took up 10 years
Circle of Fifths - Introduction: I don t consider myself a musician, although I enjoy music, and I don t count myself as an organist, but thoroughly enjoy playing the organ, which I first took up 10 years
MITOCW ocw f08-lec19_300k
 MITOCW ocw-18-085-f08-lec19_300k The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free.
MITOCW ocw-18-085-f08-lec19_300k The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free.
Broadcasting Decision CRTC
 Broadcasting Decision CRTC 2012-550 PDF version Route reference: 2012-224 Additional reference: 2012-224-1 Ottawa, 10 October 2012 Radio 710 AM Inc. Niagara Falls, Ontario Application 2011-0862-1, received
Broadcasting Decision CRTC 2012-550 PDF version Route reference: 2012-224 Additional reference: 2012-224-1 Ottawa, 10 October 2012 Radio 710 AM Inc. Niagara Falls, Ontario Application 2011-0862-1, received
The Code and the University Reference Librarian
 for our catalogs? The catalog in its simplest form is an author list of materials. But in order to make the knowledge contained in our books more readily accessible, we in America developed classed and
for our catalogs? The catalog in its simplest form is an author list of materials. But in order to make the knowledge contained in our books more readily accessible, we in America developed classed and
Authors crack the Bard's code
 The Australian Higher Education Supplement WED 19 JUL 2006, Page 028-029 theaustralian.com.au/highereducation Authors crack the Bard's code Bruce Leyland and James Goding assess the latest attempt, this
The Australian Higher Education Supplement WED 19 JUL 2006, Page 028-029 theaustralian.com.au/highereducation Authors crack the Bard's code Bruce Leyland and James Goding assess the latest attempt, this
Guide to the Delos Franklin Wilcox Papers
 University of Chicago Library Guide to the Delos Franklin Wilcox Papers 1907-1928 2006 University of Chicago Library Table of Contents Descriptive Summary Information on Use Access Citation Biographical
University of Chicago Library Guide to the Delos Franklin Wilcox Papers 1907-1928 2006 University of Chicago Library Table of Contents Descriptive Summary Information on Use Access Citation Biographical
This article was published in Cryptologia Volume XII Number 4 October 1988, pp
 This article was published in Cryptologia Volume XII Number 4 October 1988, pp. 241-246 Thanks to the Editors of Cryptologia for permission to reprint this copyright article on the Beale cipher. THE BEALE
This article was published in Cryptologia Volume XII Number 4 October 1988, pp. 241-246 Thanks to the Editors of Cryptologia for permission to reprint this copyright article on the Beale cipher. THE BEALE
Cardano Girolamo Cardano invented: Fleissner, after Austrian cryptologist (Eduard). Described by Jules Verne in the story Mathias Sandorf.
 Rotating Grille Cardano Girolamo Cardano invented: Fleissner, after Austrian cryptologist (Eduard). Described by Jules Verne in the story Mathias Sandorf. An even number of cells on each side of grille
Rotating Grille Cardano Girolamo Cardano invented: Fleissner, after Austrian cryptologist (Eduard). Described by Jules Verne in the story Mathias Sandorf. An even number of cells on each side of grille
Check back at the NCTM site for additional notes and tasks next week.
 Check back at the NCTM site for additional notes and tasks next week. PROOF ENOUGH FOR YOU? General Interest Session NCTM Annual Meeting and Exposition April 19, 2013 Ralph Pantozzi Kent Place School,
Check back at the NCTM site for additional notes and tasks next week. PROOF ENOUGH FOR YOU? General Interest Session NCTM Annual Meeting and Exposition April 19, 2013 Ralph Pantozzi Kent Place School,
Kaytee s Contest. Problem of the Week Teacher Packet. Answer Check
 Problem of the Week Teacher Packet Kaytee s Contest Farmer Kaytee brought one of her prize-winning cows to the state fair, along with its calf. In order to get people to stop and admire her cow, she thought
Problem of the Week Teacher Packet Kaytee s Contest Farmer Kaytee brought one of her prize-winning cows to the state fair, along with its calf. In order to get people to stop and admire her cow, she thought
AP Music Theory 2010 Scoring Guidelines
 AP Music Theory 2010 Scoring Guidelines The College Board The College Board is a not-for-profit membership association whose mission is to connect students to college success and opportunity. Founded in
AP Music Theory 2010 Scoring Guidelines The College Board The College Board is a not-for-profit membership association whose mission is to connect students to college success and opportunity. Founded in
CS408 Cryptography & Internet Security
 CS408 Cryptography & Internet Security Lecture 4: Rotor Machines Enigma Reza Curtmola Department of Computer Science / NJIT How to move from pencil and paper to more automatic ways of encrypting and decrypting?
CS408 Cryptography & Internet Security Lecture 4: Rotor Machines Enigma Reza Curtmola Department of Computer Science / NJIT How to move from pencil and paper to more automatic ways of encrypting and decrypting?
PDF hosted at the Radboud Repository of the Radboud University Nijmegen
 PDF hosted at the Radboud Repository of the Radboud University Nijmegen The following full text is a publisher's version. For additional information about this publication click this link. http://hdl.handle.net/2066/40258
PDF hosted at the Radboud Repository of the Radboud University Nijmegen The following full text is a publisher's version. For additional information about this publication click this link. http://hdl.handle.net/2066/40258
11. SUMMARY OF THE BASIC QUANTIFIER TRANSLATION PATTERNS SO FAR EXAMINED
 248 Hardegree, Symbolic Logic 11. SUMMARY OF THE BASIC QUANTIFIER TRANSLATION PATTERNS SO FAR EXAMINED Before continuing, it is a good idea to review the basic patterns of translation that we have examined
248 Hardegree, Symbolic Logic 11. SUMMARY OF THE BASIC QUANTIFIER TRANSLATION PATTERNS SO FAR EXAMINED Before continuing, it is a good idea to review the basic patterns of translation that we have examined
Looking Back: Rules and Regulations for School Libraries, 1910
 Western Kentucky University TopSCHOLAR DLSC Faculty Publications Library Special Collections Summer 2003 Looking Back: Rules and Regulations for School Libraries, 1910 Jonathan Jeffrey Western Kentucky
Western Kentucky University TopSCHOLAR DLSC Faculty Publications Library Special Collections Summer 2003 Looking Back: Rules and Regulations for School Libraries, 1910 Jonathan Jeffrey Western Kentucky
Cryptography. The Codebreakers: The Story of Secret Writing. by David Kahn A Bit of History. Seminal Text on Cryptography
 Cryptography A Bit of History 1 Seminal Text on Cryptography The Codebreakers: The Story of Secret Writing by David Kahn 1967 2 Early Cryptology - India Secret writing was well known and practiced in India
Cryptography A Bit of History 1 Seminal Text on Cryptography The Codebreakers: The Story of Secret Writing by David Kahn 1967 2 Early Cryptology - India Secret writing was well known and practiced in India
Resampling Statistics. Conventional Statistics. Resampling Statistics
 Resampling Statistics Introduction to Resampling Probability Modeling Resample add-in Bootstrapping values, vectors, matrices R boot package Conclusions Conventional Statistics Assumptions of conventional
Resampling Statistics Introduction to Resampling Probability Modeling Resample add-in Bootstrapping values, vectors, matrices R boot package Conclusions Conventional Statistics Assumptions of conventional
Euler s Art of Reckoning 1
 Euler s Art of Reckoning 1 Christian Siebeneicher 2 Abstract: The Art of Reckoning has always been part of human culture, but to my knowledge there have been only two eminent mathematicians who wrote a
Euler s Art of Reckoning 1 Christian Siebeneicher 2 Abstract: The Art of Reckoning has always been part of human culture, but to my knowledge there have been only two eminent mathematicians who wrote a
In these groups: Jot this down on one sheet of paper you ll turn in, please.
 AP Lit & Comp 4-9-15 1. Turn in RR for WH chapters 6-9 2. Laura s book presentation (Dani s next class) 3. Focus on WH chapters 1-9 4. Debrief timed writing look at specific tips and commonalities for
AP Lit & Comp 4-9-15 1. Turn in RR for WH chapters 6-9 2. Laura s book presentation (Dani s next class) 3. Focus on WH chapters 1-9 4. Debrief timed writing look at specific tips and commonalities for
Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at
 Biometrika Trust The Meaning of a Significance Level Author(s): G. A. Barnard Source: Biometrika, Vol. 34, No. 1/2 (Jan., 1947), pp. 179-182 Published by: Oxford University Press on behalf of Biometrika
Biometrika Trust The Meaning of a Significance Level Author(s): G. A. Barnard Source: Biometrika, Vol. 34, No. 1/2 (Jan., 1947), pp. 179-182 Published by: Oxford University Press on behalf of Biometrika
2.2. Multiplying and Dividing Powers. INVESTIGATE the Math
 . Multipling and Dividing Powers GOAL Develop and appl exponent principles to multipl and divide powers. INVESTIGATE the Math Amir thought there was a wa to simplif 1 6 1 9 1 without using a calculator.?
. Multipling and Dividing Powers GOAL Develop and appl exponent principles to multipl and divide powers. INVESTIGATE the Math Amir thought there was a wa to simplif 1 6 1 9 1 without using a calculator.?
INTERVALS Ted Greene
 1 INTERVALS The interval is to music as the atom is to matter the basic essence of the stuff. All music as we know it is composed of intervals, which in turn make up scales or melodies, which in turn make
1 INTERVALS The interval is to music as the atom is to matter the basic essence of the stuff. All music as we know it is composed of intervals, which in turn make up scales or melodies, which in turn make
The Library of Congress
 Resources from The Library of Congress Teaching with Primary Sources from The Library of Congress VDOE SOL Institutes Fall, 2016 Presented by TPSNVA Teaching with Primary Sources, Northern Virginia The
Resources from The Library of Congress Teaching with Primary Sources from The Library of Congress VDOE SOL Institutes Fall, 2016 Presented by TPSNVA Teaching with Primary Sources, Northern Virginia The
Human Hair Studies: II Scale Counts
 Journal of Criminal Law and Criminology Volume 31 Issue 5 January-February Article 11 Winter 1941 Human Hair Studies: II Scale Counts Lucy H. Gamble Paul L. Kirk Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc
Journal of Criminal Law and Criminology Volume 31 Issue 5 January-February Article 11 Winter 1941 Human Hair Studies: II Scale Counts Lucy H. Gamble Paul L. Kirk Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc
Cryptanalysis of LILI-128
 Cryptanalysis of LILI-128 Steve Babbage Vodafone Ltd, Newbury, UK 22 nd January 2001 Abstract: LILI-128 is a stream cipher that was submitted to NESSIE. Strangely, the designers do not really seem to have
Cryptanalysis of LILI-128 Steve Babbage Vodafone Ltd, Newbury, UK 22 nd January 2001 Abstract: LILI-128 is a stream cipher that was submitted to NESSIE. Strangely, the designers do not really seem to have
Key- The key k for my cipher is a single number from 1-26 which is shared between the sender and the reciever.
 Cryptography Assign. 1A Key- The key k for my cipher is a single number from 1-26 which is shared between the sender and the reciever. How to Encipher- Each letter is assigned a number beginning from k
Cryptography Assign. 1A Key- The key k for my cipher is a single number from 1-26 which is shared between the sender and the reciever. How to Encipher- Each letter is assigned a number beginning from k
2017 Summer Requirements for Students Entering 5 th Grade
 2017 Summer Requirements for Students Entering 5 th Grade The activities listed will provide your child with a review of the material they learned throughout the school year, and will promote a smooth
2017 Summer Requirements for Students Entering 5 th Grade The activities listed will provide your child with a review of the material they learned throughout the school year, and will promote a smooth
1C.5.1 Voltage Fluctuation and Flicker
 2 1 Ja n 1 4 2 1 J a n 1 4 Vo l.1 -Ge n e r a l;p a r tc-p o we r Qu a lity 1. Scope This document contains guidelines regarding maximum acceptable levels of voltage fluctuation and light flicker in the
2 1 Ja n 1 4 2 1 J a n 1 4 Vo l.1 -Ge n e r a l;p a r tc-p o we r Qu a lity 1. Scope This document contains guidelines regarding maximum acceptable levels of voltage fluctuation and light flicker in the
Setting Up the Warp System File: Warp Theater Set-up.doc 25 MAY 04
 Setting Up the Warp System File: Warp Theater Set-up.doc 25 MAY 04 Initial Assumptions: Theater geometry has been calculated and the screens have been marked with fiducial points that represent the limits
Setting Up the Warp System File: Warp Theater Set-up.doc 25 MAY 04 Initial Assumptions: Theater geometry has been calculated and the screens have been marked with fiducial points that represent the limits
21 st Century Math Projects
 Project Title : CSI Pre-Algebra: Operations & Expressions Standard Focus: Number Sense and Operations Time Range : 1-3 Days Supplies : Pencil and Paper Topics of Focus : - Order of Operations - Integer
Project Title : CSI Pre-Algebra: Operations & Expressions Standard Focus: Number Sense and Operations Time Range : 1-3 Days Supplies : Pencil and Paper Topics of Focus : - Order of Operations - Integer
MODFLOW - Grid Approach
 GMS 7.0 TUTORIALS MODFLOW - Grid Approach 1 Introduction Two approaches can be used to construct a MODFLOW simulation in GMS: the grid approach and the conceptual model approach. The grid approach involves
GMS 7.0 TUTORIALS MODFLOW - Grid Approach 1 Introduction Two approaches can be used to construct a MODFLOW simulation in GMS: the grid approach and the conceptual model approach. The grid approach involves
Cryptography in Criminal Investigations
 Journal of Criminal Law and Criminology Volume 26 Issue 6 March-April Article 10 Spring 1936 Cryptography in Criminal Investigations Don L. Kooken Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc
Journal of Criminal Law and Criminology Volume 26 Issue 6 March-April Article 10 Spring 1936 Cryptography in Criminal Investigations Don L. Kooken Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc
CLASSICAL CRYPTOGRAPHY COURSE BY LANAKI. July 01, 1996 COPYRIGHT 1996 ALL RIGHTS RESERVED LECTURE 15 STATISTICAL ATTACKS
 CLASSICAL CRYPTOGRAPHY COURSE BY LANAKI July 01, 1996 COPYRIGHT 1996 ALL RIGHTS RESERVED LECTURE 15 STATISTICAL ATTACKS SUMMARY Lecture 15 considers the role and influence that statistics and probability
CLASSICAL CRYPTOGRAPHY COURSE BY LANAKI July 01, 1996 COPYRIGHT 1996 ALL RIGHTS RESERVED LECTURE 15 STATISTICAL ATTACKS SUMMARY Lecture 15 considers the role and influence that statistics and probability
Circular Villages by Zoltan P. Dienes
 Circular Villages. 2003 by Zoltan P. Dienes (Some fun with the associative rule or bunching rule ). Note: An earlier version of this paper was published in the New Zealand Mathematics Magazine in two parts:
Circular Villages. 2003 by Zoltan P. Dienes (Some fun with the associative rule or bunching rule ). Note: An earlier version of this paper was published in the New Zealand Mathematics Magazine in two parts:
THE BAMS DAILY. 5th Issue
 THE BAMS DAILY 5th Issue 2 THE BAMS WEEKLY JOMEO'S DEATH Friar against the law? Yesterday evening, Romeo and Juliet were found dead in the churchyard of the capulets. e couple was lying on Juliets grave.
THE BAMS DAILY 5th Issue 2 THE BAMS WEEKLY JOMEO'S DEATH Friar against the law? Yesterday evening, Romeo and Juliet were found dead in the churchyard of the capulets. e couple was lying on Juliets grave.
v. 8.0 GMS 8.0 Tutorial MODFLOW Grid Approach Build a MODFLOW model on a 3D grid Prerequisite Tutorials None Time minutes
 v. 8.0 GMS 8.0 Tutorial Build a MODFLOW model on a 3D grid Objectives The grid approach to MODFLOW pre-processing is described in this tutorial. In most cases, the conceptual model approach is more powerful
v. 8.0 GMS 8.0 Tutorial Build a MODFLOW model on a 3D grid Objectives The grid approach to MODFLOW pre-processing is described in this tutorial. In most cases, the conceptual model approach is more powerful
The Product of Two Negative Numbers 1
 1. The Story 1.1 Plus and minus as locations The Product of Two Negative Numbers 1 K. P. Mohanan 2 nd March 2009 When my daughter Ammu was seven years old, I introduced her to the concept of negative numbers
1. The Story 1.1 Plus and minus as locations The Product of Two Negative Numbers 1 K. P. Mohanan 2 nd March 2009 When my daughter Ammu was seven years old, I introduced her to the concept of negative numbers
Study Guide. Solutions to Selected Exercises. Foundations of Music and Musicianship with CD-ROM. 2nd Edition. David Damschroder
 Study Guide Solutions to Selected Exercises Foundations of Music and Musicianship with CD-ROM 2nd Edition by David Damschroder Solutions to Selected Exercises 1 CHAPTER 1 P1-4 Do exercises a-c. Remember
Study Guide Solutions to Selected Exercises Foundations of Music and Musicianship with CD-ROM 2nd Edition by David Damschroder Solutions to Selected Exercises 1 CHAPTER 1 P1-4 Do exercises a-c. Remember
CITATION METRICS WORKSHOP (WEB of SCIENCE)
 CITATION METRICS WORKSHOP (WEB of SCIENCE) BASIC LEVEL: Searching Indexed Works Only Prepared by Bibliometric Team, NUS Libraries, Apr 2018 Section Description Pages I Citation Searching of Indexed Works
CITATION METRICS WORKSHOP (WEB of SCIENCE) BASIC LEVEL: Searching Indexed Works Only Prepared by Bibliometric Team, NUS Libraries, Apr 2018 Section Description Pages I Citation Searching of Indexed Works
DIFFERENTIATE SOMETHING AT THE VERY BEGINNING THE COURSE I'LL ADD YOU QUESTIONS USING THEM. BUT PARTICULAR QUESTIONS AS YOU'LL SEE
 1 MATH 16A LECTURE. OCTOBER 28, 2008. PROFESSOR: SO LET ME START WITH SOMETHING I'M SURE YOU ALL WANT TO HEAR ABOUT WHICH IS THE MIDTERM. THE NEXT MIDTERM. IT'S COMING UP, NOT THIS WEEK BUT THE NEXT WEEK.
1 MATH 16A LECTURE. OCTOBER 28, 2008. PROFESSOR: SO LET ME START WITH SOMETHING I'M SURE YOU ALL WANT TO HEAR ABOUT WHICH IS THE MIDTERM. THE NEXT MIDTERM. IT'S COMING UP, NOT THIS WEEK BUT THE NEXT WEEK.
Philosophy 405: Knowledge, Truth and Mathematics Spring Russell Marcus Hamilton College
 Philosophy 405: Knowledge, Truth and Mathematics Spring 2014 Russell Marcus Hamilton College Class #4: Aristotle Sample Introductory Material from Marcus and McEvoy, An Historical Introduction to the Philosophy
Philosophy 405: Knowledge, Truth and Mathematics Spring 2014 Russell Marcus Hamilton College Class #4: Aristotle Sample Introductory Material from Marcus and McEvoy, An Historical Introduction to the Philosophy
MATH 195: Gödel, Escher, and Bach (Spring 2001) Notes and Study Questions for Tuesday, March 20
 MATH 195: Gödel, Escher, and Bach (Spring 2001) Notes and Study Questions for Tuesday, March 20 Reading: Chapter VII Typographical Number Theory (pp.204 213; to Translation Puzzles) We ll also talk a bit
MATH 195: Gödel, Escher, and Bach (Spring 2001) Notes and Study Questions for Tuesday, March 20 Reading: Chapter VII Typographical Number Theory (pp.204 213; to Translation Puzzles) We ll also talk a bit
ILDA Image Data Transfer Format
 INTERNATIONAL LASER DISPLAY ASSOCIATION Technical Committee Revision 006, April 2004 REVISED STANDARD EVALUATION COPY EXPIRES Oct 1 st, 2005 This document is intended to replace the existing versions of
INTERNATIONAL LASER DISPLAY ASSOCIATION Technical Committee Revision 006, April 2004 REVISED STANDARD EVALUATION COPY EXPIRES Oct 1 st, 2005 This document is intended to replace the existing versions of
AskDrCallahan Calculus 1 Teacher s Guide
 AskDrCallahan Calculus 1 Teacher s Guide 3rd Edition rev 080108 Dale Callahan, Ph.D., P.E. Lea Callahan, MSEE, P.E. Copyright 2008, AskDrCallahan, LLC v3-r080108 www.askdrcallahan.com 2 Welcome to AskDrCallahan
AskDrCallahan Calculus 1 Teacher s Guide 3rd Edition rev 080108 Dale Callahan, Ph.D., P.E. Lea Callahan, MSEE, P.E. Copyright 2008, AskDrCallahan, LLC v3-r080108 www.askdrcallahan.com 2 Welcome to AskDrCallahan
Notes on Digital Circuits
 PHYS 331: Junior Physics Laboratory I Notes on Digital Circuits Digital circuits are collections of devices that perform logical operations on two logical states, represented by voltage levels. Standard
PHYS 331: Junior Physics Laboratory I Notes on Digital Circuits Digital circuits are collections of devices that perform logical operations on two logical states, represented by voltage levels. Standard
The Web Cryptology Game CODEBREAKERS.EU edition 2015
 Lecture 2, in which we look at the main methods of concealing information. We will learn that what used to be an unbreakable cipher can today be compared to a child play. We will also see how this children
Lecture 2, in which we look at the main methods of concealing information. We will learn that what used to be an unbreakable cipher can today be compared to a child play. We will also see how this children
Cognitive Units, Connections and Mathematical Proof
 Cognitive Units, Connections and Mathematical Proof Tony Barnard Published in Proceedings of PME 21, Finland, (1997), vol. 2, pp. 41 48. David Tall Mathematics Department Mathematics Education Research
Cognitive Units, Connections and Mathematical Proof Tony Barnard Published in Proceedings of PME 21, Finland, (1997), vol. 2, pp. 41 48. David Tall Mathematics Department Mathematics Education Research
Student Performance Q&A:
 Student Performance Q&A: 2010 AP Music Theory Free-Response Questions The following comments on the 2010 free-response questions for AP Music Theory were written by the Chief Reader, Teresa Reed of the
Student Performance Q&A: 2010 AP Music Theory Free-Response Questions The following comments on the 2010 free-response questions for AP Music Theory were written by the Chief Reader, Teresa Reed of the
Ego State Analysis Quiz. Instructions: These pages contain a series of optional choice statements. Please make 2 choices for each statement.
 Ego State Analysis Quiz Instructions: These pages contain a series of optional choice statements. Please make 2 choices for each statement. Score a 2 for your first choice (the choice that BEST describes
Ego State Analysis Quiz Instructions: These pages contain a series of optional choice statements. Please make 2 choices for each statement. Score a 2 for your first choice (the choice that BEST describes
