ACE Surveillance: the next generation surveillance for long-term monitoring and activity summarization
|
|
|
- Toby Preston
- 5 years ago
- Views:
Transcription
1 ACE Surveillance: the next generation surveillance for long-term monitoring and activity summarization Dmitry O. Gorodnichy Institute for Information Technology (IIT-ITI) National Research Council of Canada (NRC-CNRC) Montreal Rd, M-50, Ottawa, Canada K1A 0R6 Abstract This paper introduces a new concept for the area of video surveillance called Critical Evidence Snapshot. We show that automatic extraction and annotation of Critical Evidence Snapshots, which are defined as video snapshots that provide a piece of information that is both useful and new, is the key to improving the utility and efficiency of video surveillance systems. An implementation of an ACE (Annotated Critical Evidence) Surveillance system made from off-the-shelf cameras and a desktop is described. The results obtained on several real-life surveillance assignments confirm our vision for ACE Surveillance as the next generation technology for collecting and managing surveillance data. 1 Motivation When shopping for a video surveillance system (Google: video surveillance ), of which there are many available on the market, one gets easily informed on advanced video surveillance features which various surveillance manufactures list to attract customers. These include the highest picture quality and resolution (5Mbps), most advance digital video compression technologies, complete control of Pan, Tilt and the powerful 44X Zoom, total remoteness, wireless internet connection, greater detail and clarity, multi-channel support of up-to 32 cameras, extra fast capture (of 240 frames per second), etc. The problem arises when you try to use such surveillance systems, with any of the above features, especially for a long-term assignment. You quickly realize that, whatever great quality or quantity of video data you capture, you may just not have enough space to record it nor enough time to browse it all in order to detect that only piece of information that is important to you. Simple motion detection (or more exactly, video-frame differencing-based change detection), which is a default technique used by many surveillance systems to initiate video capture, does not resolve the problem. More complex foreground detection techniques are also not sufficient for the purpose. This leads us to definition of what is considered to be the main bottleneck of the current surveillance technology. 1.1 Two main video surveillance problems Storage space consumption problem The first problem deals with the excessive amount of video data which is saved in a digital form to be analyzed later. This is the way commercial DVRs (Digital Video Recorders) work. They digitize dozens of hours of video from each camera on a hard-drive, which can then be viewed and analyzed by a human when needed. The need to browse through the recorded surveillance data usually arises post-factum after a criminal act has been committed. To get an idea of how much hard-drive space is usually consumed by a regular surveillance system, consider a typical monitoring assignment, such as in a banks or a grocery store, where 2 16 of cameras are used to monitor the premises. For this type of monitoring, 7 days of video recording is usually required; however, archival of up to 30 days of video is also common. Even with a compression rate of 10 Mb per 1 minute, it takes 10Mb 24h 60min/10 = 1.5 GB per day per camera or about Gb of hard-drive space for a 1
2 single assignment 1. The factor of ten is generously chosen to approximate the motion-detection-based video capturing. It is clearly seen that, while this amount of space is feasible to have by using dedicated DVR systems, it is not within a normal hard space used by an ordinary computer. Data management problem. London bombing video backtracking experience The problem however is not just the lack of hard-drive space, but not having enough time to go though all recorded data searching for what you need. Having too much stored data is just as bad as not having any data at all. If the amount of data is so large that it cannot be managed within reasonable amount of time and efforts, it is useless. After the London bombing, millions of hours of digitized video data from thousands of cameras were browsed by the Scotland Yard officers searching for the data which could lead to the identification of the bombers and their accomplices. Because of the extremely large number of search branching occurring every time a person disappears from a camera field of view, manual browsing of the recorded video data backtracking the suspect and everyone who resembled him was extremely time consuming and was not feasible to be performed within the desired time frame. This example shows the difficulty one faces if no solution is provided for automating the information extraction from video. Therefore, it is critical for a video surveillance system to store only that video data which is useful, i.e. the data containing new evidence. This is further illustrated with another example, which also happened in real life and which is used throughout the paper as a practical guide and benchmark for the surveillance systems we want to design. 2 Who stole my bike example The proper name for the surveillance task example described below should be What is happening while I am away, because it is not just about the very moment when a bike was stolen, but about the entire log of activities preceding the accident. Here is a description of the task Mb per 1 minute is convenient rule-of-thump compression rate that can be used to estimate space required to store a video. More exactly, one of the best compression rates for digital video is achieved by Divx v5 codec 9Mb per 1 minute of 640 x 464 digital video. Analog video requires about a quater of size needed for digital video, due to th fact that its resolution never acceeds 320 x 240. I used to keep my bike in a hidden slot between my car and the wall inside my car-port. My house is located in a cul-de-sac and the bike left in the car-port is not seen, unless you come close to the house and sneak around, passing near the house windows. This is why, I never locked my bike there, assuming that it was safe enough. One morning the bike was gone. Analyzing how this could happened, it was clear that someone was visiting my house prior to the incident firstly, to find that there was a good unlocked bike there and secondly, to find out the best time when nobody is around. But when did this visit happen and who was that? This was left unclear. I did not have any evidence which could have helped the police to identify the thief. This seemed ironic to me, since I do have a plenty of cameras in my house which could have been used to monitor the premises, and even more, I could have easily connected them to my desktop computer which has a variety of video capturing tools. The problem was that, without anticipating a theft, would you record days and possibly weeks of video data with only a slight chance that it might be used at some point in future? How much space on your computer and how much time would you spend daily to maintain such system, provided that is meant to run in a continuous day-by-day basis? Instead of answering these rhetoric questions and to make sure that next time I have a better idea on who and when is visiting my house while I am away, I have decided to use this scenario to develop and test a new type of video-recognition-based surveillance system that would automatically generate a summary of all activities visible by a camera over a period of time. With such a system, I should be able to let the system run for as many hours as I am away usually for about 9-12 hours, and then simply press the play button upon my return and view a short video report produced by the system. I know that the report should be short not more than five-ten minutes, because, as mentioned earlier, there is normally no much activity happening around my house. Criteria for the system The performance criteria required from the surveillance system are listed below. 1. It should be affordable, easily installed and operated i.e. run on a desktop computer with off-theshelf cameras: USB web-cameras, CCTV cameras or home-video hand-held cameras (analog or digital), either directly connected to a computer or connected via a wireless transmitter for viewing remote areas. 2
3 2. It should run real-time in a continuous mode (24/7, non-stop, everyday). 3. It should collect as much useful video evidence as possible. What type of evidence and how much of it to be collected is determined by the quality video data and the setup. For example, in a condition with bright illumination and close-range viewing (i.e. high resolution), the system can collect the information about the visitors faces, whereas in a monitoring assignment performed at night or at a distance, such information as number of passing cars and people would be collected. 4. It should be merciful with respect to the harddrive space. 5. It should be as much automated as possible: both in recognizing the pieces of evidence in live video and retrieving them from saved data off-line. 6. The collected video evidence, besides being useful, has also to be easily manageable, i.e. it should be succinct and non-redundant. The currently available surveillance technology does not meet these criteria. In this paper we present a new type of the video surveillance, called ACE Surveillance, that does. ACE Surveillance can be considered as another example of automated video-recognition-based surveillance, also known as Smart Video Surveillance, Intelligent Video Management, Intelligent Visual Surveillance ([12, 4, 3]). However, it not only attempts to identify in real-time the objects and actions in video, but also addresses the problems of the surveillance data compression and retrieval. These problems are tackled by introducing the concept of Critical Evidence Snapshot, which the ACE Surveillance system attempts to automatically extract from video. ACE Surveillance is most useful in security domains where premises are monitored over a long period of time and are rarely attended. The affordability of ACE Surveillance, both in terms of the video-equipment cost and the computer requirements, also makes it very suitable for home monitoring with ordinary off-the-shelf cameras and desktop computers. 3 New concepts: Critical Evidence Snapshot and ACE Surveillance Definition: Critical Evidence Snapshot (CES) is defined as a video snapshot that provides to a viewer a piece of information that is both useful and new. Definition: A surveillance system that deals with extraction and manipulation of Annotated Critical Evidence snapshots from a surveillance video is defined as ACE Surveillance. Normally, the evidence is an event that is captured by a video camera. What is important is that the number of events that moving objects (such as people, cars, pets) perform is limited. These events are listed below: 1. Appear. 2. Move: left, right, closer, further. 3. Stay on the same location (with a certain range). 4. Disappear. Another important observation that ACE Surveillance is based upon is that between the times when an object Appears and Disappears, there is no need to store all video frames from the surveillance video. Instead, what needs to be stored are the first snapshot when the object appeared, and the last snapshot before it disappeared, both of which must be timestamped to provide a time interval within which the object was visible. In addition to these two snapshots, a few other (but not many!) snapshots of the object may also be stored. These can be stored intentionally if a snapshot is qualified by the system as the one that either shows a better quality picture (or view) of the object or captures a new event performed by the object. They may also be stored unintentionally due to the shortcomings of a video recognition algorithm, when a snapshot is erroneously qualified as the one described above. However, even if such snapshots are stored unintentionally, they still are useful as long as there are not too many of them, since they guide a viewer s attention to the detected changes and the better quality snapshots. All of the extracted snapshots will make a pool of the extracted CES-es, of which some will be more useful, while some less. When combined together along with extra annotation, which describes them, they create a very useful and succinct representation of what has been observed by a camera. This is a key idea behind the ACE Surveillance. Regardless of how detailed the annotation of extracted snapshots is, the very fact that instead of storing 16 fps video it stores only selected number of frames, makes the output much more manageable and useful. 3.1 Annotations The annotations that can be provided with each extracted CES depend on the level of difficulty of a monitoring assignment and on the complexity of the object 3
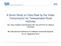
4 Figure 1. The ACE Surveillance client-server architecture. CES-es extracted by the clients are transmitted to the server along with their annotations. tracking and recognition algorithms used for the assignment. In the currently used ACE Surveillance system (see Section 5), we use time-stamps, optional object motion activity labels (such as Left, Right, Closer, Further), optional object identification number (if an object is recognized as the already seen one) and object counts (such as number of pedestrians and cars passing by the window) to create a text-based annotation of the CES. In many cases, such text-based CES annotation is already sufficient to know what was happening during the monitored time interval (in particular for cases when nothing unusual happened) without a need to browse the actual snapshots. This is illustrated in Figure 2.a. When the same activity is observed every day, then approximately the same text-based log made of CES annotations is expected. In addition to text-based annotations, graphical annotation of CES are displayed to facilitate their viewing. For example, the boxes circumscribing the moving objects and their trajectories, shown in Figures?? -??, help the viewer to focus attention on the detected objects and their motion trajectories and/or boundaries. 3.2 Specific interest: faces in video ACE Surveillance has a very good application for person identification from video. For forensic purposes, what is needed from a surveillance system is not a video or extensive number of snapshots somehow capturing a person, but a few snapshots that show a person in a best possible for the current setup view and resolution. From our previous work on face recognition in video [7], we know that a face becomes recognizable, both by a human and a computer for such tasks as classification and verification, when the image of his/her face has a resolution of at least 12 pixels between the eyes. Therefore the key idea for the ACE Surveillance is to keep tracking an object (while taking CES-es and their annotations) until it is close enough to the camera for a face detection and memorization techniques to be employed. It can be seen however by examining the quality of the video images from our surveillance tasks (Figures 2-6), that, while this idea definitely shows the right way to proceed in person identification from video, it does require a well lit environment or better quality video cameras so that high-quality video-snapshots can be taken when needed. One way of resolving the poor quality issue, is (as suggested in [8]) to use a pan-tilt digital photo-camera, the orientation of which is driven by the tracking results from the video camera and the trigger button of which is initiated by a detection of an appropriate CES from the video. 4
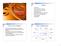
5 a) b) Figure 2. The entire 9-hour activity observed over night is summarized in 23 annotated CES-es: a) the text-based CES annotations, encoded in file names, and b) the thumbnail view of the extracted CES-es. In the file name ddhh-mm-ss c ox( annot)-oy( annot).jpg, dd-hh-mm-ss stand for date-hour-minute-second when CES was taken, C camera number, ox object #X is detected (If systems recognizes an object that it has already seen, it assigns # X corresponding to that object. Otherwise, a new # X is assigned). ( annot) object annotation which is one of the following: L, R, C, F (object moves Left, Right, Closer, or Further away), On / Off (illumination change caused by object, which usually indicates either appearing/disappering of the object or switching on/off the lights). 4 ACE Surveillance architecture The architecture of the ACE Surveillance system is driven by the goals of extracting and annotating the Critical Evidence Snapshots as presented below (See also Figure 1). It consists of CES client module, of which there can be several each connected to one or more videocameras, and CES managing module, which can operate on an another server-based computer, normally located in a security monitoring office. In the client-based CES registration module, video data are acquired and CES-es are extracted on-line from a video stream, annotated and prepared for transmission. In the server-based CES managing module, off-line post-processing, archival and retrieval of CESes happens. 4.1 CES client architecture CES clients capture video from one or more video sources, performs on-line video recognition of captured video data and then send video-frames along with the acquired CES and their annotation to the CES server. For each video frame of each video source, a CES client performs the following six tasks in real-time (as it captures the video): Task C1: Detection of new or moving object(s) in video. Task C2: Computation of the attributes of the detected object(s) Task C3: Recognition of object(s) as either new or already seen, based on its attributes. Task C4: Classifying a frame as either being a CES (i.e providing new information) or not. 5
6 Task C5: Extracting and creating CES annotations, such as: timestamps, augmentations, outlines, counters, contours. Task C6: a) If a video frame is CES, then it is sent to the CES server along with the annotations; b) It not, then resolution-reduced version of the frame is sent to the CES server. There is an abundant set of literature addressing the computer vision techniques that can be employed for each of the above described tasks (see the current workshop [10]). The most important of results of these, in our opinion, of which we use in our work, are the described below (see also our discussion in [11]). For task C1: A combination of change detection (based on last several frames only) [2], foreground detection (based on adaptive maintenance of the background model [16]), and motion pattern estimation (based on second-order change detection [6] or tracking the changed objects over several consecutive frames [13, 14]) allows one to achieve the best detection of only those objects that either move or appear/disappear and ignore all other changes observable in video, such as caused by wind blowing the tree branches or due to the wireless transmission. The presence of colour information is not critical for this task, which our experiments with black-n-white CCTV cameras confirm (see Section 5). Although, should colour be available, it should not be disregarded as it does improve change detection [1]. The techniques for isolating shadows from the object can be considered, but our experiments indicate that they are not critical. The reason is that the shadows follow the objects, and it is the object motion that determined whether a frame is a CES or not. For tasks C2 and C3: the attributes which allow us to track and identify an object as the already seen are: location and size, measured by the size of the detected motion blob (x,z,w,h) their derivatives (changes) in time: d(x,z,w,h)/dt colour: Pcolour(i,j) texture/edge: Ptexture(i,j), Surveillance video usually shows objects in poor resolution and quality. Because of that feature-based tracking or recognition, such as the one based on selecting pixel-based object features as in Lucas-Kanade or SIFT-based approaches, may not work. We argue that the best approaches for surveillance video are those based on accumulation of data over time such as (listed in order of their discriminating power), histogram-based, correlogram-based [17], and associative memory based [9]. Histograms count the number of occurrences of different object values. Correlograms take also into account their geometrical location with respect to each other. Associative memories also provides a more intelligent update of the object representation based both on the currently obtained piece of data and the past data. Using these approaches, the recognition of object(s) as either new or already seen is based on the computed object attributes and thresholds on allowed variations of objects size and location. For colour-based recognition, recognition-driven (rather than sensor-driven) colour space should be used, such as UCS, HSC, or non-linearly transformed YCrCb, possibly with reduced range of values to count for the low quality of data. For texture/edge-based recognition, Local Binary Patterns [15] and Binary Consensus Transform [5] appear most promising. For task C5: It has to be emphasized that the prime goal of the CES annotations is to provide a suggestion of what is observed, rather than to actually identify the activity or the object. This is one of the main lessons from the computer-vision: with so much variation in cameras quality, lighting conditions and motion types, it is very difficult for a computer to completely replace a human in an arbitrary recognition task.therefore the prime task of the computerized surveillance is in helping a human to perform such recognition, rather than doing it instead of a human This is the idea behind CES annotations; they serve as a guide to facilitate the retrieval of the required data in a mass of archived data sets. Out implementation of an ACE Surveillance system allows simultaneous monitoring of several locations using the same program on a single computer. A number of USB video-cameras (or video capture devices) can be connected to a computer. On a 2.4GHz Pentium IV computer, it takes about 60 msec to process a video frame from one camera, which allows processing up to four cameras in a close to real-time speed. Figures 2-4 show the moving object detection results, as well as CES and their annotations obtained from several reallife surveillance assignments. 4.2 CES server architecture The CES server receives video-frames and CES-es from all CES clients (using either a TCP-IP protocol or secure ftp) and prepares them for viewing on a security desk monitor using a web-scripting code. At any point in time, a security officer has the option of switching between the following two (or three) 6
7 viewing options. Task S1: Viewing live video from all cameras, which is shown as a flow of resolution-reduced video frames received from an CES client. Unlike CES frames, which are stored on a CES server hard-drive, regular (non-ces) frames are not stored and are deleted after being displayed. Task S2: Viewing Automatically obtained Critical Evidence Summarization (ACES) video for a particular camera or a time interval. ACES video is made of annotated resolution-reduced CES-es played in a sequence (as a movie) with possible augmentation (such as outlines/boxes around the detected objects) to guide the visual attention of the viewer. As ACES video is played, an officer has an option of seeing the actual (unmodified highresolution) version of every CES. In addition, for each video-camera, the last acquired time-stamped CES as well as the a text-encoded log of all CES annotations plotted on a time-line are also made visible to the officer so that s/he always has a clear picture on what is and was happening in each camera field of view. Task S3: Viewing CES-es, by associative similarity. This is another advantage offered by the ACE Surveillance it allows the viewing of the stored CES-es not only in the order they were captured (as done when viewing the summarization video), but also in the order of their similarity to each other or an query image. Histogrambased and associative-memory-based approaches are very suitable for such context-based snapshot ranking. 5 ACE Surveillance in action Below we present typical results obtained using the ACE Surveillance on several real-life monitoring assignments. The focus of this presentation is on the low quality of video data one has to deal with while monitoring several premises using surveillance cameras and the utility of the CES-based video summarization obtained by the ACE Surveillance on these data. Experiments were on conducted on two monitoring stations, called here Office station and Home station. For each monitoring assignment, the premises were surveyed over a long period of time (10 hours at least) Thus lighting conditions were changing from dusk to dark to sunlight and back to dark. Both indoor (through the door) and outdoor (though the window) viewpoints were tested. In order to test and to tune the system, these monitoring assignments use several off-the-shelf videocamera and capture boards: including digital low-cost and high-cost CMOS web-cams, black-n-white wireless CCTV surveillance camera with and analog output and 8mm hand-held cameras with zoom and highquality lenses connected directly and wireless (via a transmiter) to a computer. In case of a wireless video transmission, the receiver was located in the basement of the house, while the transmiter was located on the main floor of the house. This created extra noise due to wireless transmission, which, as our experiments show, does not change much the performance of the system. The Home station had two cameras connected, one viewing the entrance of the house with the carport at a close range, the other camera viewing the street on the back of the house at a distance. The Office station had also two cameras, one viewing the corridor in front of the office, which has an exit stairwell door, the other one viewing the street from the third floor on which the office is located. The samples of the annotated CES-es extracted from several runs on these assignments are shown in Figures 2-4. The entire set of CES-based summarization obtained by ACE Surveillance on these assignments, which includes the original CES extracted from video, their annotated thumbnail versions, and ACES (CES-based summarization) video, are made available at the project web-site. Besides, an example of a live ACE assignment can also be accessed through a password-protected CESserver site: php (password: vp4s-06 ). Below is the summary of the results. Figure 2 shows both the text annotation of the observed activities and the thumbnail CES-based summarization for an over-a-night monitoring (Hours of operation: 10 hours (22:00-8:00). Camera used: USB low-cost CMOS web-cam. Number of extracted CES: 23. ACES summarization video: 74Kb). The CES annotations automatically provided by the system are encoded in the file names. Figures 3a and 4a show the results obtained on the same premises as in Figure 2, but obtained on different days with a different cameras: (20 hours (22:10-18:09) of monitoring with a wireless black-n-white CCTV cam + Video2USB converter. Number of extracted CES: 177 and 222. ACES video: 900Kb). Figures 3b and 4c show the results obtained by a camera that overviews the road on the back of the house (20 hours of monitoring with a Creative USB web-cam, ACES video: 4Mb). Figures 3 and 4 also show the results obtained from 7
8 the Office station: i)over a night (monitoring the corridor: (19 hours (16:45-10:00) of monitoring with a USB web-cam. Number of extracted CES: 148, ACES video: 600Kb), ii) and over a weekend monitoring the street (from Friday night to Monday morning). Figures 3-4 show the annotated resolution-reduced CES-es extracted from video, where the annotation includes a timestamp (shown at top right of the video image) and highlighted boxes outlining the detected objects, the direction of their motion (blue box - the changing moving blob, red box - foreground history, green box - enclosing around the object). For a comparison with a typical motion-trigged surveillance, which is also often called automated by the manufactures, we conducted a similar monitoring assignment in which a camera surveyed a street (as in Figure 4.d) over 2 hours with a commercially available automated surveillance program from Honest Technology called VideoPatrol. The number of video frames which was captured by the program (regardless of what motion threshold was choses) significantly exceeded the number (by the factor of up to 100) of actual number of frames that contained any useful information, such a passing car or a pedestrian. Most frames were captured simply because there was some inter-frame difference detected by the system, such as due to wind or non-perfect camera quality. 6 Conclusion The paper defines a new type of automated surveillance, based on extracting and annotating pieces of Critical Evidence in live video-streams, termed the ACE Surveillance, which is shown to facilitate significantly the manageability of the surveillance video data, tackling both the data storage and the data retrieval problems. The work presented in this paper is in its early stages. However even the results obtained so far on several real-life monitoring tests support the validity of our vision of the ACE Surveillance as the next generation surveillance. In this sense, the name ACE Surveillance, which was originally coined as an acronym for Annotated Critical Evidence, can also signify Automated surveillance and imply an ace-like potential behind it. Acknowledgement The author acknowledges the help of Kris Woodbeck in the PHP coding of the CES-server for the described in the papers client-server architecture of the ACE surveillance system. References [1] J. Black and T. Ellis. Intelligent image surveillance and monitoring. In Measurement and Control, 35(8): ,, [2] E. Durucan and T. Ebrahimi. Change detection and background extraction by linear algebra. In IEEE Proc. on Video Communications and Processing for Third Generation Surveillance Systems, 89(10), pages , [3] M. V. Espina and S. Velastin. Intelligent distributed surveillance systems: A review. In IEE Proceedings - Vision, Image and Signal Processing, 152(2) IEE, April 2005, pp , [4] J. P. Freeman. Jp freeman ranks 3vr at top of intelligent video market [5] B. Froba and C. Kublbeck. Face tracking by means of continuous detection. In Proc. of CVPR Workshop on Face Processing in Video (FPIV 04), Washington DC, [6] D. Gorodnichy. Second order change detection, and its application to blink-controlled perceptual interfaces. In Proc. IASTED Conf. on Visualization, Imaging and Image Processing (VIIP 2003), pp , Benalmadena, Spain, Sept.8-10, [7] D. Gorodnichy. Video-based framework for recognizing people in video. In Second Workshop on Face Processing in Video (FPiV 05). Proceedings of Second Canadian Conference on Computer and Robot Vision (CRV 05), pp , Victoria, BC, Canada, ISBN NRC 48216, [8] D. Gorodnichy. Seeing faces in video by computers. Editorial for special issue on face processing in video sequences (nrc 48295). Image and Video Computing, 24(6): , [9] D. O. Gorodnichy. Associative neural networks as means for low-resolution video-based recognition. In International Joint Conference on Neural Networks (IJCNN 05), Montreal, Quebec, Canada, NRC 48217, [10] D. O. Gorodnichy and L. Yin. Introduction to the first international workshop on video processing for security (vp4s-06). In Proceedings of the Canadian conference Computer and Robot Vision (CRV 06), June 7-9, Quebec City, Canada. NRC , [11] D. O. Gorodnichy and A. Yogeswaran. Detection and tracking of pianist hands and fingers. In In Proc. of the Canadian conference Computer and Robot Vision (CRV 06), Quebec, Canada, June 7-9. NRC , [12] A. Hampapur, L. M. Brown, J. Connell, M. Lu, H. Merkl, S. Pankanti, A. W. Senior, C. fe Shu, and Y. li Tian. Multi-scale tracking for smart video surveillance. In IEEE Transactions on Signal Processing, Vol. 22, No. 2, [13] Y. li Tian and A. Hampapur. Robust salient motion detection with complex background for real-time 8
9 video surveillance. In IEEE Computer Society Workshop on Motion and Video Computing, Breckenridge, Colorado, [14] D. Magee. Tracking multiple vehicles using foreground, background and motion models. In In ECCV Workshop on Statistical Methods in Video Processing, pages 7-12, [15] T. Ojala, M. Pietaikinen, and T. Maenpaa. Multiresolution gray-scale and rotation invariant texture classification with local binary patterns. IEEE Trans. Pattern Anal. Mach. Intell., 24(7): , [16] K. Toyama, J. Krumm, B. Brumitt, and B. Meyers. Wallflower: Principles and practice of background maintenance. In International Conference on Computer Vision, Greece., [17] Q. Zhao and H. Tao. Object tracking using color correlogram. In 2nd Joint IEEE International Workshop on Visual Surveillance and Performance Evaluation of Tracking and Surveillance, Page(s): , Oct,
10 a) b) c) d) Figure 3. Examples of a 640x480 CES-es obtained from Home (a,b) and Office (c,d) surveillance stations: a) overnight monitoring of the car-port in front of the house (by wireless CCTV camera), and b) over-day monitoring of a street on the back of the house (by a USB webcam). c) overnight monitoring of the corner corridor and exit door in front of the office (by a USB2 webcam), and d) over-week-end monitoring of a street seen from the office window (by Sharp 8mm hand-held camera). The moving blob image and the foreground motion history images are shown on the bottom of each CES. The detected objects and their the direction/range of the motion are shown. Low quality of video images can be seen. 10
11 a) b). c) d) Figure 4. Examples of Annotated CES-es from several monitoring assignments: a) overnight monitoring of the carport in front of a house (with a black-and-white wireless CCTV camera on Home station), b) overnight monitoring of the corner corridor and exit door in front of the office (by a USB2 webcam on Office station), c) over-day monitoring of a street on the back of a house (with a USB webcam on Home station), d) over-week-end monitoring of a street from the office window (by Sharp 8mm hand-held camera on Office station). Timestamp is shown at top right of CES. Highlighted boxes indicate: blue box - the changing moving blob, red box - foreground history, green box enclosing around the object. 11
SCode V3.5.1 (SP-501 and MP-9200) Digital Video Network Surveillance System
 V3.5.1 (SP-501 and MP-9200) Digital Video Network Surveillance System Core Technologies Image Compression MPEG4. It supports high compression rate with good image quality and reduces the requirement of
V3.5.1 (SP-501 and MP-9200) Digital Video Network Surveillance System Core Technologies Image Compression MPEG4. It supports high compression rate with good image quality and reduces the requirement of
CI-218 / CI-303 / CI430
 CI-218 / CI-303 / CI430 Network Camera User Manual English AREC Inc. All Rights Reserved 2017. l www.arec.com All information contained in this document is Proprietary Table of Contents 1. Overview 1.1
CI-218 / CI-303 / CI430 Network Camera User Manual English AREC Inc. All Rights Reserved 2017. l www.arec.com All information contained in this document is Proprietary Table of Contents 1. Overview 1.1
SCode V3.5.1 (SP-601 and MP-6010) Digital Video Network Surveillance System
 V3.5.1 (SP-601 and MP-6010) Digital Video Network Surveillance System Core Technologies Image Compression MPEG4. It supports high compression rate with good image quality and reduces the requirement of
V3.5.1 (SP-601 and MP-6010) Digital Video Network Surveillance System Core Technologies Image Compression MPEG4. It supports high compression rate with good image quality and reduces the requirement of
D-Lab & D-Lab Control Plan. Measure. Analyse. User Manual
 D-Lab & D-Lab Control Plan. Measure. Analyse User Manual Valid for D-Lab Versions 2.0 and 2.1 September 2011 Contents Contents 1 Initial Steps... 6 1.1 Scope of Supply... 6 1.1.1 Optional Upgrades... 6
D-Lab & D-Lab Control Plan. Measure. Analyse User Manual Valid for D-Lab Versions 2.0 and 2.1 September 2011 Contents Contents 1 Initial Steps... 6 1.1 Scope of Supply... 6 1.1.1 Optional Upgrades... 6
Milestone Solution Partner IT Infrastructure Components Certification Report
 Milestone Solution Partner IT Infrastructure Components Certification Report Infortrend Technologies 5000 Series NVR 12-15-2015 Table of Contents Executive Summary:... 4 Introduction... 4 Certified Products...
Milestone Solution Partner IT Infrastructure Components Certification Report Infortrend Technologies 5000 Series NVR 12-15-2015 Table of Contents Executive Summary:... 4 Introduction... 4 Certified Products...
CCTV BASICS YOUR GUIDE TO CCTV SECURITY SURVEILLANCE
 CAMERAS DVRS CABLES The best indoor and outdoor cameras to suit your application Resolution, frame rate, HDD space and must have features. Video and power cables to get you connected. CONTENTS Selecting
CAMERAS DVRS CABLES The best indoor and outdoor cameras to suit your application Resolution, frame rate, HDD space and must have features. Video and power cables to get you connected. CONTENTS Selecting
Part 1 Basic Operation
 This product is a designed for video surveillance video encode and record, it include H.264 video Compression, large HDD storage, network, embedded Linux operate system and other advanced electronic technology,
This product is a designed for video surveillance video encode and record, it include H.264 video Compression, large HDD storage, network, embedded Linux operate system and other advanced electronic technology,
S-Series Server Setup Quiz
 1. In the System Setup window, System Information displays additional information such as: (a) IP Address (b) Modems (c) Sound Card (d) Video Channels and Audio Channels 2. You can change the Recording
1. In the System Setup window, System Information displays additional information such as: (a) IP Address (b) Modems (c) Sound Card (d) Video Channels and Audio Channels 2. You can change the Recording
DVR-431 USB Wireless Receiver User Manual
 DVR-431 USB Wireless Receiver User Manual Thank you for using our wireless USB receiver, please read the following content carefully before using, it will help you make better use of this product. Introduction
DVR-431 USB Wireless Receiver User Manual Thank you for using our wireless USB receiver, please read the following content carefully before using, it will help you make better use of this product. Introduction
Indoor/Outdoor 8MP 4K H.265 WDR PoE IR Bullet Network Camera
 Indoor/Outdoor 8MP 4K H.265 WDR PoE IR Bullet Network Camera TV-IP318PI (v1.0r) 8MP 4K UHD video (3840 x 2160) at 20 fps Smart covert IR LEDs for night vision up to 30 meters (98 ft.) Outdoor IP67 weather
Indoor/Outdoor 8MP 4K H.265 WDR PoE IR Bullet Network Camera TV-IP318PI (v1.0r) 8MP 4K UHD video (3840 x 2160) at 20 fps Smart covert IR LEDs for night vision up to 30 meters (98 ft.) Outdoor IP67 weather
Smart Traffic Control System Using Image Processing
 Smart Traffic Control System Using Image Processing Prashant Jadhav 1, Pratiksha Kelkar 2, Kunal Patil 3, Snehal Thorat 4 1234Bachelor of IT, Department of IT, Theem College Of Engineering, Maharashtra,
Smart Traffic Control System Using Image Processing Prashant Jadhav 1, Pratiksha Kelkar 2, Kunal Patil 3, Snehal Thorat 4 1234Bachelor of IT, Department of IT, Theem College Of Engineering, Maharashtra,
B. The specified product shall be manufactured by a firm whose quality system is in compliance with the I.S./ISO 9001/EN 29001, QUALITY SYSTEM.
 VideoJet 8000 8-Channel, MPEG-2 Encoder ARCHITECTURAL AND ENGINEERING SPECIFICATION Section 282313 Closed Circuit Video Surveillance Systems PART 2 PRODUCTS 2.01 MANUFACTURER A. Bosch Security Systems
VideoJet 8000 8-Channel, MPEG-2 Encoder ARCHITECTURAL AND ENGINEERING SPECIFICATION Section 282313 Closed Circuit Video Surveillance Systems PART 2 PRODUCTS 2.01 MANUFACTURER A. Bosch Security Systems
TVD-5406 H.265 IP 3MPX Outdoor Dome Camera A&E Specifications
 TVD-5406 H.265 IP 3MPX Outdoor Dome Camera A&E Specifications A. The TVD-5406 IP 3MPX Dome camera shall capture, encode and transmit video over a network. B. TVD-5406 shall be as manufactured by Interlogix.
TVD-5406 H.265 IP 3MPX Outdoor Dome Camera A&E Specifications A. The TVD-5406 IP 3MPX Dome camera shall capture, encode and transmit video over a network. B. TVD-5406 shall be as manufactured by Interlogix.
THE ANGMERING SCHOOL CCTV POLICY. The Angmering School CCTV Code of Practice Version 1, 15/02/12, Created by Marc Ginnaw.
 THE ANGMERING SCHOOL CCTV POLICY 2012 Page 1 of 8 The Angmering School CCTV Code of Practice Introduction The purpose of this document is to define The Angmering School's CCTV policy, to determine responsibilities,
THE ANGMERING SCHOOL CCTV POLICY 2012 Page 1 of 8 The Angmering School CCTV Code of Practice Introduction The purpose of this document is to define The Angmering School's CCTV policy, to determine responsibilities,
For high performance video recording and visual alarm verification solution, TeleEye RX is your right choice!
 TeleEye RX carries a range of professional digital video recording servers, which is designed to operate on diverse network environment and fully utilize the existing network bandwidth with optimal performance.
TeleEye RX carries a range of professional digital video recording servers, which is designed to operate on diverse network environment and fully utilize the existing network bandwidth with optimal performance.
ViewCommander- NVR Version 3. User s Guide
 ViewCommander- NVR Version 3 User s Guide The information in this manual is subject to change without notice. Internet Video & Imaging, Inc. assumes no responsibility or liability for any errors, inaccuracies,
ViewCommander- NVR Version 3 User s Guide The information in this manual is subject to change without notice. Internet Video & Imaging, Inc. assumes no responsibility or liability for any errors, inaccuracies,
2-/4-Channel Cam Viewer E- series for Automatic License Plate Recognition CV7-LP
 2-/4-Channel Cam Viewer E- series for Automatic License Plate Recognition Copyright 2-/4-Channel Cam Viewer E-series for Automatic License Plate Recognition Copyright 2018 by PLANET Technology Corp. All
2-/4-Channel Cam Viewer E- series for Automatic License Plate Recognition Copyright 2-/4-Channel Cam Viewer E-series for Automatic License Plate Recognition Copyright 2018 by PLANET Technology Corp. All
Wireless Cloud Camera TV-IP751WC (v1.0r)
 TRENDnet s, model, takes the work out of viewing video over the internet. Previously to view video remotely, users needed to perform many complicated and time consuming steps: such as signing up for a
TRENDnet s, model, takes the work out of viewing video over the internet. Previously to view video remotely, users needed to perform many complicated and time consuming steps: such as signing up for a
Intelligent Monitoring Software IMZ-RS300. Series IMZ-RS301 IMZ-RS304 IMZ-RS309 IMZ-RS316 IMZ-RS332 IMZ-RS300C
 Intelligent Monitoring Software IMZ-RS300 Series IMZ-RS301 IMZ-RS304 IMZ-RS309 IMZ-RS316 IMZ-RS332 IMZ-RS300C Flexible IP Video Monitoring With the Added Functionality of Intelligent Motion Detection With
Intelligent Monitoring Software IMZ-RS300 Series IMZ-RS301 IMZ-RS304 IMZ-RS309 IMZ-RS316 IMZ-RS332 IMZ-RS300C Flexible IP Video Monitoring With the Added Functionality of Intelligent Motion Detection With
AXIS M30 Series AXIS M3015 AXIS M3016. User Manual
 AXIS M3015 AXIS M3016 User Manual Table of Contents About this manual.......................................... 3 Product overview........................................... 4 How to access the product....................................
AXIS M3015 AXIS M3016 User Manual Table of Contents About this manual.......................................... 3 Product overview........................................... 4 How to access the product....................................
Understanding Compression Technologies for HD and Megapixel Surveillance
 When the security industry began the transition from using VHS tapes to hard disks for video surveillance storage, the question of how to compress and store video became a top consideration for video surveillance
When the security industry began the transition from using VHS tapes to hard disks for video surveillance storage, the question of how to compress and store video became a top consideration for video surveillance
Promotion Package Pricing
 Promotion Package Pricing (For HDB flat, Condo, Small Office & Retail Shop less than 1200sqft) $1400 before GST for 4 camera package $1300 before GST for 3 camera package $1200 before GST for 2 camera
Promotion Package Pricing (For HDB flat, Condo, Small Office & Retail Shop less than 1200sqft) $1400 before GST for 4 camera package $1300 before GST for 3 camera package $1200 before GST for 2 camera
SECURITY RECORDING 101
 MODULE 2 SECURITY RECORDING 101 Page 1 BEGINNERS LEVEL MODULE 2. SECURITY RECORDING 101 Page 2 2.0 MODULE OUTLINE 2.1 Top DIY Recording Terms you need to know 2.2 DVR Features 2.3 DVR/NVR Technology Comparison
MODULE 2 SECURITY RECORDING 101 Page 1 BEGINNERS LEVEL MODULE 2. SECURITY RECORDING 101 Page 2 2.0 MODULE OUTLINE 2.1 Top DIY Recording Terms you need to know 2.2 DVR Features 2.3 DVR/NVR Technology Comparison
HD TVI TURBO HD DVR Hikvision DS 7216HGHI SH/A (16ch, H.264, HDMI, VGA)
 HD TVI TURBO HD DVR Hikvision DS 7216HGHI SH/A (16ch, 1080p@12fps, H.264, HDMI, VGA) Code: M75216 Front view Rear view The included remote control http://www.dipolnet.com/document print M75216.htm 1/5
HD TVI TURBO HD DVR Hikvision DS 7216HGHI SH/A (16ch, 1080p@12fps, H.264, HDMI, VGA) Code: M75216 Front view Rear view The included remote control http://www.dipolnet.com/document print M75216.htm 1/5
CMS MANUAL DIGITAL VIDEO RECORDER CMS. Operation Manual 3CTC-016-5EN8M. For the safe use of the product, please make sure to read Safety Precautions.
 DIGITAL VIDEO RECORDER CMS Operation Manual 3CTC-016-5EN8M For the safe use of the product, please make sure to read Safety Precautions. 1 Copyrights All the contents of this manual are protected under
DIGITAL VIDEO RECORDER CMS Operation Manual 3CTC-016-5EN8M For the safe use of the product, please make sure to read Safety Precautions. 1 Copyrights All the contents of this manual are protected under
O.E.M TVI Digital Video Recorder
 Professional security Products R O.E.M TVI Digital Video Recorder 4 Channel O.EM TVI-RED4CH The TVI-RED4CH CCTV recorder adopts high performance video processing chips and embedded Linux operating system.
Professional security Products R O.E.M TVI Digital Video Recorder 4 Channel O.EM TVI-RED4CH The TVI-RED4CH CCTV recorder adopts high performance video processing chips and embedded Linux operating system.
Striking Clarity, Unparalleled Flexibility, Precision Control
 Striking Clarity, Unparalleled Flexibility, Precision Control Product Brochures English 460XW 460C 460C 800 ieditor The - tents and processed camera inputs to provide the monitoring by supporting camera
Striking Clarity, Unparalleled Flexibility, Precision Control Product Brochures English 460XW 460C 460C 800 ieditor The - tents and processed camera inputs to provide the monitoring by supporting camera
IEEE Santa Clara ComSoc/CAS Weekend Workshop Event-based analog sensing
 IEEE Santa Clara ComSoc/CAS Weekend Workshop Event-based analog sensing Theodore Yu theodore.yu@ti.com Texas Instruments Kilby Labs, Silicon Valley Labs September 29, 2012 1 Living in an analog world The
IEEE Santa Clara ComSoc/CAS Weekend Workshop Event-based analog sensing Theodore Yu theodore.yu@ti.com Texas Instruments Kilby Labs, Silicon Valley Labs September 29, 2012 1 Living in an analog world The
AXIS M30 Network Camera Series. AXIS M3046-V Network Camera. AXIS M3045 V Network Camera. User Manual
 AXIS M3044-V Network Camera AXIS M3045 V Network Camera AXIS M3046-V Network Camera User Manual Table of Contents About this manual.......................................... 3 Solution overview...........................................
AXIS M3044-V Network Camera AXIS M3045 V Network Camera AXIS M3046-V Network Camera User Manual Table of Contents About this manual.......................................... 3 Solution overview...........................................
Processor time 9 Used memory 9. Lost video frames 11 Storage buffer 11 Received rate 11
 Processor time 9 Used memory 9 Lost video frames 11 Storage buffer 11 Received rate 11 2 3 After you ve completed the installation and configuration, run AXIS Installation Verifier from the main menu icon
Processor time 9 Used memory 9 Lost video frames 11 Storage buffer 11 Received rate 11 2 3 After you ve completed the installation and configuration, run AXIS Installation Verifier from the main menu icon
Reducing False Positives in Video Shot Detection
 Reducing False Positives in Video Shot Detection Nithya Manickam Computer Science & Engineering Department Indian Institute of Technology, Bombay Powai, India - 400076 mnitya@cse.iitb.ac.in Sharat Chandran
Reducing False Positives in Video Shot Detection Nithya Manickam Computer Science & Engineering Department Indian Institute of Technology, Bombay Powai, India - 400076 mnitya@cse.iitb.ac.in Sharat Chandran
Exhibits. Open House. NHK STRL Open House Entrance. Smart Production. Open House 2018 Exhibits
 2018 Exhibits NHK STRL 2018 Exhibits Entrance E1 NHK STRL3-Year R&D Plan (FY 2018-2020) The NHK STRL 3-Year R&D Plan for creating new broadcasting technologies and services with goals for 2020, and beyond
2018 Exhibits NHK STRL 2018 Exhibits Entrance E1 NHK STRL3-Year R&D Plan (FY 2018-2020) The NHK STRL 3-Year R&D Plan for creating new broadcasting technologies and services with goals for 2020, and beyond
PulseCounter Neutron & Gamma Spectrometry Software Manual
 PulseCounter Neutron & Gamma Spectrometry Software Manual MAXIMUS ENERGY CORPORATION Written by Dr. Max I. Fomitchev-Zamilov Web: maximus.energy TABLE OF CONTENTS 0. GENERAL INFORMATION 1. DEFAULT SCREEN
PulseCounter Neutron & Gamma Spectrometry Software Manual MAXIMUS ENERGY CORPORATION Written by Dr. Max I. Fomitchev-Zamilov Web: maximus.energy TABLE OF CONTENTS 0. GENERAL INFORMATION 1. DEFAULT SCREEN
HDMI / Video Wall over IP Receiver with PoE
 / Wall over IP Receiver with Key Features Network 1080P ultra high quality video transmitter Assigns video sources to any monitor of the video wall Up to 8 x 8 Screen Array supported Extends high definition
/ Wall over IP Receiver with Key Features Network 1080P ultra high quality video transmitter Assigns video sources to any monitor of the video wall Up to 8 x 8 Screen Array supported Extends high definition
Browsing News and Talk Video on a Consumer Electronics Platform Using Face Detection
 Browsing News and Talk Video on a Consumer Electronics Platform Using Face Detection Kadir A. Peker, Ajay Divakaran, Tom Lanning Mitsubishi Electric Research Laboratories, Cambridge, MA, USA {peker,ajayd,}@merl.com
Browsing News and Talk Video on a Consumer Electronics Platform Using Face Detection Kadir A. Peker, Ajay Divakaran, Tom Lanning Mitsubishi Electric Research Laboratories, Cambridge, MA, USA {peker,ajayd,}@merl.com
The modern and intelligent CCTV (written by Vlado Damjanovski, CEO - ViDi Labs,
 The modern and intelligent CCTV (written by Vlado Damjanovski, CEO - ViDi Labs, www.vidilabs.com) The digital (r)evolution of the last twenty years changed almost everything. Analogue vinyl records morphed
The modern and intelligent CCTV (written by Vlado Damjanovski, CEO - ViDi Labs, www.vidilabs.com) The digital (r)evolution of the last twenty years changed almost everything. Analogue vinyl records morphed
A Novel Study on Data Rate by the Video Transmission for Teleoperated Road Vehicles
 A Novel Study on Data Rate by the Video Transmission for Teleoperated Road Vehicles Tito Tang, Frederic Chucholowski, Min Yan and Prof. Dr. Markus Lienkamp 9th International Conference on Intelligent Unmanned
A Novel Study on Data Rate by the Video Transmission for Teleoperated Road Vehicles Tito Tang, Frederic Chucholowski, Min Yan and Prof. Dr. Markus Lienkamp 9th International Conference on Intelligent Unmanned
Digital Video Engineering Professional Certification Competencies
 Digital Video Engineering Professional Certification Competencies I. Engineering Management and Professionalism A. Demonstrate effective problem solving techniques B. Describe processes for ensuring realistic
Digital Video Engineering Professional Certification Competencies I. Engineering Management and Professionalism A. Demonstrate effective problem solving techniques B. Describe processes for ensuring realistic
The Diverse Multimedia & Surveillance System Via Dico2000 with PC DICO Operation Manual
 DICO 2000 Operation Manual Main Screen Overview IP Address & Communication Status Disk Status Screen Mode Warning Status Video Recording Status RUN Setup Search Exit SETUP The beginning ID and Password
DICO 2000 Operation Manual Main Screen Overview IP Address & Communication Status Disk Status Screen Mode Warning Status Video Recording Status RUN Setup Search Exit SETUP The beginning ID and Password
IMPROVING SIGNAL DETECTION IN SOFTWARE-BASED FACIAL EXPRESSION ANALYSIS
 WORKING PAPER SERIES IMPROVING SIGNAL DETECTION IN SOFTWARE-BASED FACIAL EXPRESSION ANALYSIS Matthias Unfried, Markus Iwanczok WORKING PAPER /// NO. 1 / 216 Copyright 216 by Matthias Unfried, Markus Iwanczok
WORKING PAPER SERIES IMPROVING SIGNAL DETECTION IN SOFTWARE-BASED FACIAL EXPRESSION ANALYSIS Matthias Unfried, Markus Iwanczok WORKING PAPER /// NO. 1 / 216 Copyright 216 by Matthias Unfried, Markus Iwanczok
VERINT EDGEVR 200 INTELLIGENT DIGITAL VIDEO RECORDER (Rev A)
 VERINT EDGEVR 200 INTELLIGENT DIGITAL VIDEO RECORDER (Rev A) TECHNICAL SPECIFICATIONS SECURITY SYSTEM DIVISION 28 ELECTRONIC SAFETY AND SECURITY LEVEL 1 28 20 00 ELECTRONIC SURVEILLANCE LEVEL 2 28 23 00
VERINT EDGEVR 200 INTELLIGENT DIGITAL VIDEO RECORDER (Rev A) TECHNICAL SPECIFICATIONS SECURITY SYSTEM DIVISION 28 ELECTRONIC SAFETY AND SECURITY LEVEL 1 28 20 00 ELECTRONIC SURVEILLANCE LEVEL 2 28 23 00
PYROPTIX TM IMAGE PROCESSING SOFTWARE
 Innovative Technologies for Maximum Efficiency PYROPTIX TM IMAGE PROCESSING SOFTWARE V1.0 SOFTWARE GUIDE 2017 Enertechnix Inc. PyrOptix Image Processing Software v1.0 Section Index 1. Software Overview...
Innovative Technologies for Maximum Efficiency PYROPTIX TM IMAGE PROCESSING SOFTWARE V1.0 SOFTWARE GUIDE 2017 Enertechnix Inc. PyrOptix Image Processing Software v1.0 Section Index 1. Software Overview...
DETEXI Basic Configuration
 DETEXI Network Video Management System 5.5 EXPAND YOUR CONCEPTS OF SECURITY DETEXI Basic Configuration SETUP A FUNCTIONING DETEXI NVR / CLIENT It is important to know how to properly setup the DETEXI software
DETEXI Network Video Management System 5.5 EXPAND YOUR CONCEPTS OF SECURITY DETEXI Basic Configuration SETUP A FUNCTIONING DETEXI NVR / CLIENT It is important to know how to properly setup the DETEXI software
Preface... Specification...14
 Contents for V680L Operating Manual Preface......3 Important safety tips...3 Accessories of product...4 Icons of product...5 Installation support...7 Description for operating steps... 8 Description for
Contents for V680L Operating Manual Preface......3 Important safety tips...3 Accessories of product...4 Icons of product...5 Installation support...7 Description for operating steps... 8 Description for
AXIS M30 Network Camera Series. AXIS M3046-V Network Camera. AXIS M3045 V Network Camera. User Manual
 AXIS M3044-V Network Camera AXIS M3045 V Network Camera AXIS M3046-V Network Camera User Manual Table of Contents About this manual.......................................... 3 System overview............................................
AXIS M3044-V Network Camera AXIS M3045 V Network Camera AXIS M3046-V Network Camera User Manual Table of Contents About this manual.......................................... 3 System overview............................................
2.4GHz Digital Wireless Peephole Viewer User Manual Contents
 2.4GHz Digital Wireless Peephole Viewer User Manual Contents 1. Introduction...2 2. Features...2 3. Packing list...3 4. Peephole...3 5. Indoor monitor...4 6. Installation instructions of peephole...5 7.
2.4GHz Digital Wireless Peephole Viewer User Manual Contents 1. Introduction...2 2. Features...2 3. Packing list...3 4. Peephole...3 5. Indoor monitor...4 6. Installation instructions of peephole...5 7.
RS Part No Instruction Manual Solid State DVR. (Single Chanel for Mobile) SSD01CA
 RS Part No. 696-1210 Instruction Manual Solid State DVR (Single Chanel for Mobile) RS PART NO.: 696-1210 MJPEG 1CH CAR DVR (Compact size 1ch Stand Alone DVR) Simple & Max Low cost but great guality MJPEG
RS Part No. 696-1210 Instruction Manual Solid State DVR (Single Chanel for Mobile) RS PART NO.: 696-1210 MJPEG 1CH CAR DVR (Compact size 1ch Stand Alone DVR) Simple & Max Low cost but great guality MJPEG
Smart Coding Technology
 WHITE PAPER Smart Coding Technology Panasonic Video surveillance systems Vol.2 Table of contents 1. Introduction... 1 2. Panasonic s Smart Coding Technology... 2 3. Technology to assign data only to subjects
WHITE PAPER Smart Coding Technology Panasonic Video surveillance systems Vol.2 Table of contents 1. Introduction... 1 2. Panasonic s Smart Coding Technology... 2 3. Technology to assign data only to subjects
ViewCommander-NVR. Version 6. User Guide
 ViewCommander-NVR Version 6 User Guide The information in this manual is subject to change without notice. Internet Video & Imaging, Inc. assumes no responsibility or liability for any errors, inaccuracies,
ViewCommander-NVR Version 6 User Guide The information in this manual is subject to change without notice. Internet Video & Imaging, Inc. assumes no responsibility or liability for any errors, inaccuracies,
Shot Transition Detection Scheme: Based on Correlation Tracking Check for MB-Based Video Sequences
 , pp.120-124 http://dx.doi.org/10.14257/astl.2017.146.21 Shot Transition Detection Scheme: Based on Correlation Tracking Check for MB-Based Video Sequences Mona A. M. Fouad 1 and Ahmed Mokhtar A. Mansour
, pp.120-124 http://dx.doi.org/10.14257/astl.2017.146.21 Shot Transition Detection Scheme: Based on Correlation Tracking Check for MB-Based Video Sequences Mona A. M. Fouad 1 and Ahmed Mokhtar A. Mansour
HSR-1 Digital Surveillance Recorder Preliminary
 HSR-1 Digital Surveillance Recorder Hybrid Technology - An Essential Requirement for High-Performance Digital Video Recording & Archiving Preliminary How do you rate your security Can it record as long
HSR-1 Digital Surveillance Recorder Hybrid Technology - An Essential Requirement for High-Performance Digital Video Recording & Archiving Preliminary How do you rate your security Can it record as long
G ARD SECURITY SYSTEM Product Listing 2007
 G ARD SECURITY SYSTEM Product Listing 2007 G ARD L2000 WIRELESS ALARM SYSTEM Totally Wireless Wireless Telephone G'ARD L-2000 Wireless Alarm System uses the state of art microprocessor for data processing.
G ARD SECURITY SYSTEM Product Listing 2007 G ARD L2000 WIRELESS ALARM SYSTEM Totally Wireless Wireless Telephone G'ARD L-2000 Wireless Alarm System uses the state of art microprocessor for data processing.
APPLICATIONS OF A SEMI-AUTOMATIC MELODY EXTRACTION INTERFACE FOR INDIAN MUSIC
 APPLICATIONS OF A SEMI-AUTOMATIC MELODY EXTRACTION INTERFACE FOR INDIAN MUSIC Vishweshwara Rao, Sachin Pant, Madhumita Bhaskar and Preeti Rao Department of Electrical Engineering, IIT Bombay {vishu, sachinp,
APPLICATIONS OF A SEMI-AUTOMATIC MELODY EXTRACTION INTERFACE FOR INDIAN MUSIC Vishweshwara Rao, Sachin Pant, Madhumita Bhaskar and Preeti Rao Department of Electrical Engineering, IIT Bombay {vishu, sachinp,
Optiflex Interactive Video System
 Optiflex Interactive Video System Optiflex Interactive Video System 1 Before You Start...............2 On-site Video Surveillance.......6 Touchscreen Interface Viewing...10 Secure Remote Look-in........16
Optiflex Interactive Video System Optiflex Interactive Video System 1 Before You Start...............2 On-site Video Surveillance.......6 Touchscreen Interface Viewing...10 Secure Remote Look-in........16
Technical Note. Manufacturer: Elan g! DVR 7.0 OVERVIEW SUPPORTED FEATURES
 Technical Note Manufacturer: Elan g! DVR 7.0 Minimum Core Module Version: Version 7.0, 6.7 Document Revision Date: 09/16/2014 OVERVIEW Important: This document refers to Version 7.0/6.7 DVR. Please see
Technical Note Manufacturer: Elan g! DVR 7.0 Minimum Core Module Version: Version 7.0, 6.7 Document Revision Date: 09/16/2014 OVERVIEW Important: This document refers to Version 7.0/6.7 DVR. Please see
Development of a wearable communication recorder triggered by voice for opportunistic communication
 Development of a wearable communication recorder triggered by voice for opportunistic communication Tomoo Inoue * and Yuriko Kourai * * Graduate School of Library, Information, and Media Studies, University
Development of a wearable communication recorder triggered by voice for opportunistic communication Tomoo Inoue * and Yuriko Kourai * * Graduate School of Library, Information, and Media Studies, University
Project Summary EPRI Program 1: Power Quality
 Project Summary EPRI Program 1: Power Quality April 2015 PQ Monitoring Evolving from Single-Site Investigations. to Wide-Area PQ Monitoring Applications DME w/pq 2 Equating to large amounts of PQ data
Project Summary EPRI Program 1: Power Quality April 2015 PQ Monitoring Evolving from Single-Site Investigations. to Wide-Area PQ Monitoring Applications DME w/pq 2 Equating to large amounts of PQ data
Mars hybrid Digital Video Recorders
 Mars hybrid Digital Video Recorders Our Planet range of IP cameras are automatically configured by this DVR. No IP address change, no protocol setting, no password required, don t even need to be in the
Mars hybrid Digital Video Recorders Our Planet range of IP cameras are automatically configured by this DVR. No IP address change, no protocol setting, no password required, don t even need to be in the
VIDEO ALARM VERIFICATION UNIT VIVER
 VIDEO ALARM VERIFICATION UNIT VIVER viver_en 09/08 The VIVER module provides remote video alarm verification, based on image sequences transmitted from cameras installed in the protected facility. The
VIDEO ALARM VERIFICATION UNIT VIVER viver_en 09/08 The VIVER module provides remote video alarm verification, based on image sequences transmitted from cameras installed in the protected facility. The
Datasheet. 720P HD IR IP Camera
 Datasheet 720P HD IR IP Camera Dec 2012 Features Adopt TMS320DM368 video processor, with embedded Linux operation system which is stable and low power consumption. Adopt H.264, MPEG-4 compressing algorithm,
Datasheet 720P HD IR IP Camera Dec 2012 Features Adopt TMS320DM368 video processor, with embedded Linux operation system which is stable and low power consumption. Adopt H.264, MPEG-4 compressing algorithm,
invr User s Guide Rev 1.4 (Aug. 2004)
 Contents Contents... 2 1. Program Installation... 4 2. Overview... 4 3. Top Level Menu... 4 3.1 Display Window... 9 3.1.1 Channel Status Indicator Area... 9 3.1.2. Quick Control Menu... 10 4. Detailed
Contents Contents... 2 1. Program Installation... 4 2. Overview... 4 3. Top Level Menu... 4 3.1 Display Window... 9 3.1.1 Channel Status Indicator Area... 9 3.1.2. Quick Control Menu... 10 4. Detailed
SISTORE CX highest quality IP video with recording and analysis
 CCTV SISTORE CX highest quality IP video with recording and analysis Building Technologies SISTORE CX intelligent digital video codec SISTORE CX is an intelligent digital video Codec capable of performing
CCTV SISTORE CX highest quality IP video with recording and analysis Building Technologies SISTORE CX intelligent digital video codec SISTORE CX is an intelligent digital video Codec capable of performing
FEATURES MPEG4/MJPEG DVR
 FEATURES MPEG4/MJPEG DVR Technology Compression format providing crystal clear images with real time performance. Multiplex Allow live display, record, playback, backup and network operation at the same
FEATURES MPEG4/MJPEG DVR Technology Compression format providing crystal clear images with real time performance. Multiplex Allow live display, record, playback, backup and network operation at the same
Milestone Leverages Intel Processors with Intel Quick Sync Video to Create Breakthrough Capabilities for Video Surveillance and Monitoring
 white paper Milestone Leverages Intel Processors with Intel Quick Sync Video to Create Breakthrough Capabilities for Video Surveillance and Monitoring Executive Summary Milestone Systems, the world s leading
white paper Milestone Leverages Intel Processors with Intel Quick Sync Video to Create Breakthrough Capabilities for Video Surveillance and Monitoring Executive Summary Milestone Systems, the world s leading
HCS-4100/20 Series Application Software
 HCS-4100/20 Series Application Software HCS-4100/20 application software is comprehensive, reliable and user-friendly. But it is also an easy care software system which helps the operator to manage the
HCS-4100/20 Series Application Software HCS-4100/20 application software is comprehensive, reliable and user-friendly. But it is also an easy care software system which helps the operator to manage the
1CHDVRD1 USER MANUAL. These instructions apply to unit model 1CHDVRD1 only. Please read carefully before use.
 These instructions apply to unit model 1CHDVRD1 only. Please read carefully before use. 1CHDVRD1 USER MANUAL Description Description... 03 Features... 03 Notes... 03 Packing List... 04 Technical Specifications...
These instructions apply to unit model 1CHDVRD1 only. Please read carefully before use. 1CHDVRD1 USER MANUAL Description Description... 03 Features... 03 Notes... 03 Packing List... 04 Technical Specifications...
UniVision Engineering Limited Modpark Parking System Technical Description. Automatic Vehicle Access Control by Video Identification/
 Automatic Vehicle Access Control by Video Identification/ Order Code: VISPA10 Introduction ASYTEC offers a vehicle access control system integrated into a car park management system, VISPA10. The system
Automatic Vehicle Access Control by Video Identification/ Order Code: VISPA10 Introduction ASYTEC offers a vehicle access control system integrated into a car park management system, VISPA10. The system
... A Pseudo-Statistical Approach to Commercial Boundary Detection. Prasanna V Rangarajan Dept of Electrical Engineering Columbia University
 A Pseudo-Statistical Approach to Commercial Boundary Detection........ Prasanna V Rangarajan Dept of Electrical Engineering Columbia University pvr2001@columbia.edu 1. Introduction Searching and browsing
A Pseudo-Statistical Approach to Commercial Boundary Detection........ Prasanna V Rangarajan Dept of Electrical Engineering Columbia University pvr2001@columbia.edu 1. Introduction Searching and browsing
Casambi App User Guide
 Casambi App User Guide Version 1.5.4 2.1.2017 Casambi Technologies Oy Table of contents 1 of 28 Table of contents 1 Smart & Connected 2 Using the Casambi App 3 First time use 3 Taking luminaires into use:
Casambi App User Guide Version 1.5.4 2.1.2017 Casambi Technologies Oy Table of contents 1 of 28 Table of contents 1 Smart & Connected 2 Using the Casambi App 3 First time use 3 Taking luminaires into use:
NEW APPROACHES IN TRAFFIC SURVEILLANCE USING VIDEO DETECTION
 - 93 - ABSTRACT NEW APPROACHES IN TRAFFIC SURVEILLANCE USING VIDEO DETECTION Janner C. ArtiBrain, Research- and Development Corporation Vienna, Austria ArtiBrain has installed numerous incident detection
- 93 - ABSTRACT NEW APPROACHES IN TRAFFIC SURVEILLANCE USING VIDEO DETECTION Janner C. ArtiBrain, Research- and Development Corporation Vienna, Austria ArtiBrain has installed numerous incident detection
VNP 100 application note: At home Production Workflow, REMI
 VNP 100 application note: At home Production Workflow, REMI Introduction The At home Production Workflow model improves the efficiency of the production workflow for changing remote event locations by
VNP 100 application note: At home Production Workflow, REMI Introduction The At home Production Workflow model improves the efficiency of the production workflow for changing remote event locations by
Mobile IP Camera C6010E
 Mobile IP Camera C6010E Streamax Technology Co., Ltd. Thanks for Using Streamax Mobile IP Camera This manual aims at providing reference for Mobile IP Camera installation and use. Here you can find all
Mobile IP Camera C6010E Streamax Technology Co., Ltd. Thanks for Using Streamax Mobile IP Camera This manual aims at providing reference for Mobile IP Camera installation and use. Here you can find all
Guide to Network Video Applications AXIS 2120
 Guide to Network Video Applications AXIS 2120 About this brochure This brochure contains several real world examples showing how Axis network video products are currently being implemented around the world
Guide to Network Video Applications AXIS 2120 About this brochure This brochure contains several real world examples showing how Axis network video products are currently being implemented around the world
Date of Test: 20th 24th October 2015
 APPENDIX 15/03 TEST RESULTS FOR AVER EVC130P Manufacturer: Model: AVer EVC130p Software Version: 00.01.08.62 Optional Features and Modifications: None Date of Test: 20th 24th October 2015 HD Camera CODEC
APPENDIX 15/03 TEST RESULTS FOR AVER EVC130P Manufacturer: Model: AVer EVC130p Software Version: 00.01.08.62 Optional Features and Modifications: None Date of Test: 20th 24th October 2015 HD Camera CODEC
Digital Video Telemetry System
 Digital Video Telemetry System Item Type text; Proceedings Authors Thom, Gary A.; Snyder, Edwin Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
Digital Video Telemetry System Item Type text; Proceedings Authors Thom, Gary A.; Snyder, Edwin Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
Network Disk Recorder WJ-ND200
 Network Disk Recorder WJ-ND200 Network Disk Recorder Operating Instructions Model No. WJ-ND200 ERROR MIRROR TIMER HDD1 REC LINK /ACT OPERATE HDD2 ALARM SUSPEND ALARM BUZZER STOP Before attempting to connect
Network Disk Recorder WJ-ND200 Network Disk Recorder Operating Instructions Model No. WJ-ND200 ERROR MIRROR TIMER HDD1 REC LINK /ACT OPERATE HDD2 ALARM SUSPEND ALARM BUZZER STOP Before attempting to connect
Image Contrast Enhancement (ICE) The Defining Feature. Author: J Schell, Product Manager DRS Technologies, Network and Imaging Systems Group
 WHITE PAPER Image Contrast Enhancement (ICE) The Defining Feature Author: J Schell, Product Manager DRS Technologies, Network and Imaging Systems Group Image Contrast Enhancement (ICE): The Defining Feature
WHITE PAPER Image Contrast Enhancement (ICE) The Defining Feature Author: J Schell, Product Manager DRS Technologies, Network and Imaging Systems Group Image Contrast Enhancement (ICE): The Defining Feature
Interactive Virtual Laboratory for Distance Education in Nuclear Engineering. Abstract
 Interactive Virtual Laboratory for Distance Education in Nuclear Engineering Prashant Jain, James Stubbins and Rizwan Uddin Department of Nuclear, Plasma and Radiological Engineering University of Illinois
Interactive Virtual Laboratory for Distance Education in Nuclear Engineering Prashant Jain, James Stubbins and Rizwan Uddin Department of Nuclear, Plasma and Radiological Engineering University of Illinois
what s in the Box? Camera transmitter with power cable 3M sticker 2 RVS SYSTEMS
 TM 1 what s in the Box? Camera transmitter with power cable 3M sticker 2 RVS SYSTEMS table of Contents introduction...4 features...5 Specifications...6-7 installation...8-9 Operations...10-15 Disclaimer...16
TM 1 what s in the Box? Camera transmitter with power cable 3M sticker 2 RVS SYSTEMS table of Contents introduction...4 features...5 Specifications...6-7 installation...8-9 Operations...10-15 Disclaimer...16
How-to Note: Quickstart: ITM9000 [This note applies to ITM9000 (handheld tester)] Contents. Overview. Materials Included
![How-to Note: Quickstart: ITM9000 [This note applies to ITM9000 (handheld tester)] Contents. Overview. Materials Included How-to Note: Quickstart: ITM9000 [This note applies to ITM9000 (handheld tester)] Contents. Overview. Materials Included](/thumbs/93/112907906.jpg) How-to Note: Quickstart: ITM9000 [This note applies to ITM9000 (handheld tester)] Contents Overview... 1 Materials Included... 1 Getting Started... 2 Main Operations... 4 Reference / Additional Notes...
How-to Note: Quickstart: ITM9000 [This note applies to ITM9000 (handheld tester)] Contents Overview... 1 Materials Included... 1 Getting Started... 2 Main Operations... 4 Reference / Additional Notes...
2-/4-Channel Cam Viewer E-series for Automatic License Plate Recognition CV7-LP
 2-/4-Channel Cam Viewer E-series for Automatic License Plate Recognition Copyright Copyright 2015 by PLANET Technology Corp. All rights reserved. No part of this publication may be reproduced, transmitted,
2-/4-Channel Cam Viewer E-series for Automatic License Plate Recognition Copyright Copyright 2015 by PLANET Technology Corp. All rights reserved. No part of this publication may be reproduced, transmitted,
EAN-Performance and Latency
 EAN-Performance and Latency PN: EAN-Performance-and-Latency 6/4/2018 SightLine Applications, Inc. Contact: Web: sightlineapplications.com Sales: sales@sightlineapplications.com Support: support@sightlineapplications.com
EAN-Performance and Latency PN: EAN-Performance-and-Latency 6/4/2018 SightLine Applications, Inc. Contact: Web: sightlineapplications.com Sales: sales@sightlineapplications.com Support: support@sightlineapplications.com
Outline. Why do we classify? Audio Classification
 Outline Introduction Music Information Retrieval Classification Process Steps Pitch Histograms Multiple Pitch Detection Algorithm Musical Genre Classification Implementation Future Work Why do we classify
Outline Introduction Music Information Retrieval Classification Process Steps Pitch Histograms Multiple Pitch Detection Algorithm Musical Genre Classification Implementation Future Work Why do we classify
A Design Approach of Automatic Visitor Counting System Using Video Camera
 IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-issn: 2278-1676,p-ISSN: 2320-3331, Volume 10, Issue 2 Ver. I (Mar Apr. 2015), PP 62-67 www.iosrjournals.org A Design Approach of Automatic
IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-issn: 2278-1676,p-ISSN: 2320-3331, Volume 10, Issue 2 Ver. I (Mar Apr. 2015), PP 62-67 www.iosrjournals.org A Design Approach of Automatic
Day & Night 1080P HD IR IP Camera
 Day & Night 1080P HD IR IP Camera Features Full HD 2 megapixel CMOS image sensor True H.264 AVC/MPEG-4 part 10 real-time video compression H.264 and Motion JPEG multi-profile video streaming 3D noise reduction
Day & Night 1080P HD IR IP Camera Features Full HD 2 megapixel CMOS image sensor True H.264 AVC/MPEG-4 part 10 real-time video compression H.264 and Motion JPEG multi-profile video streaming 3D noise reduction
1080P HD Vandal Resistant Dome IP Camera
 1080P HD Vandal Resistant Dome IP Camera Features Full HD 2 megapixel CMOS image sensor True H.264 AVC/MPEG-4 part 10 real-time video compression H.264 and Motion JPEG multi-profile video streaming Meets
1080P HD Vandal Resistant Dome IP Camera Features Full HD 2 megapixel CMOS image sensor True H.264 AVC/MPEG-4 part 10 real-time video compression H.264 and Motion JPEG multi-profile video streaming Meets
Day & Night 1080P HD Vari-Focal Dome IR IP Camera
 Day & Night 1080P HD Vari-Focal Dome IR IP Camera Features Full HD 2 megapixel CMOS image sensor True H.264 AVC/MPEG-4 part 10 real-time video compression H.264 and Motion JPEG multi-profile video streaming
Day & Night 1080P HD Vari-Focal Dome IR IP Camera Features Full HD 2 megapixel CMOS image sensor True H.264 AVC/MPEG-4 part 10 real-time video compression H.264 and Motion JPEG multi-profile video streaming
Speech and Speaker Recognition for the Command of an Industrial Robot
 Speech and Speaker Recognition for the Command of an Industrial Robot CLAUDIA MOISA*, HELGA SILAGHI*, ANDREI SILAGHI** *Dept. of Electric Drives and Automation University of Oradea University Street, nr.
Speech and Speaker Recognition for the Command of an Industrial Robot CLAUDIA MOISA*, HELGA SILAGHI*, ANDREI SILAGHI** *Dept. of Electric Drives and Automation University of Oradea University Street, nr.
Intelligent Farm Surveillance System for Animal Detection in Image Processing using combined GMM and Optical Flow method
 Intelligent Farm Surveillance System for Animal Detection in Image Processing using combined GMM and Optical Flow method 1 Akash K. Mehta, 2 Shital Solanki 1 M.E. Scholar, 2 Assistant Professor 1 Information
Intelligent Farm Surveillance System for Animal Detection in Image Processing using combined GMM and Optical Flow method 1 Akash K. Mehta, 2 Shital Solanki 1 M.E. Scholar, 2 Assistant Professor 1 Information
Using the VideoEdge IP Encoder with Intellex IP
 This application note explains the tradeoffs inherent in using IP video and provides guidance on optimal configuration of the VideoEdge IP encoder with Intellex IP. The VideoEdge IP Encoder is a high performance
This application note explains the tradeoffs inherent in using IP video and provides guidance on optimal configuration of the VideoEdge IP encoder with Intellex IP. The VideoEdge IP Encoder is a high performance
AXIS P14 Network Camera Series AXIS P1448-LE Network Camera. User Manual
 AXIS P1445-LE Network Camera AXIS P1447-LE Network Camera AXIS P1448-LE Network Camera User Manual About this manual About this manual This User Manual provides information on the product regarding: Access
AXIS P1445-LE Network Camera AXIS P1447-LE Network Camera AXIS P1448-LE Network Camera User Manual About this manual About this manual This User Manual provides information on the product regarding: Access
2.4GHz Digital Wireless Video Door Phone User Manual
 2.4GHz Digital Wireless Video Door Phone User Manual Thank you for purchasing our product. For better taking advantage of the prior functions please carefully read user manual for correct installation
2.4GHz Digital Wireless Video Door Phone User Manual Thank you for purchasing our product. For better taking advantage of the prior functions please carefully read user manual for correct installation
OPERATING INSTRUCTIONS TOM-0431IP
 OPERATING INSTRUCTIONS TOM-0431IP Table of Contents FCC Information -------------------------------------------------------------------- 2 Safety and Environmental Precautions ------------------------------------------------
OPERATING INSTRUCTIONS TOM-0431IP Table of Contents FCC Information -------------------------------------------------------------------- 2 Safety and Environmental Precautions ------------------------------------------------
Magic U Series 4CH Octa-brid DVR System, 4K Output, 2 HDD slots, esata, 4CH Audio
 Magic U DVR detects Analog 960H HD-TVI A-HD EX-SDI HD-SDI cameras automatically Records up to 4 IP cameras REAL-TIME Live Programmable Multi-CH HD Spot Out 4K Video output Touch Interface iphone Android
Magic U DVR detects Analog 960H HD-TVI A-HD EX-SDI HD-SDI cameras automatically Records up to 4 IP cameras REAL-TIME Live Programmable Multi-CH HD Spot Out 4K Video output Touch Interface iphone Android
Understanding IP Video for
 Brought to You by Presented by Part 2 of 4 MAY 2007 www.securitysales.com A1 Part 2of 4 Clear Eye for the IP Video Guy By Bob Wimmer Principal Video Security Consultants cctvbob@aol.com AT A GLANCE Image
Brought to You by Presented by Part 2 of 4 MAY 2007 www.securitysales.com A1 Part 2of 4 Clear Eye for the IP Video Guy By Bob Wimmer Principal Video Security Consultants cctvbob@aol.com AT A GLANCE Image
EyeFace SDK v Technical Sheet
 EyeFace SDK v4.5.0 Technical Sheet Copyright 2015, All rights reserved. All attempts have been made to make the information in this document complete and accurate. Eyedea Recognition, Ltd. is not responsible
EyeFace SDK v4.5.0 Technical Sheet Copyright 2015, All rights reserved. All attempts have been made to make the information in this document complete and accurate. Eyedea Recognition, Ltd. is not responsible
AXIS 2420 Network Camera
 NETWORK CAMERAS SALES GUIDE AXIS 2420 NETWORK CAMERA AXIS 2420 Network Camera Latest update: June 5, 2001 Rev: 1.1 TABLE OF CONTENTS 1 PRODUCT SUMMARY...4 2 AXIS IP SURVEILLANCE FLAGSHIP PRODUCT...4 2.1
NETWORK CAMERAS SALES GUIDE AXIS 2420 NETWORK CAMERA AXIS 2420 Network Camera Latest update: June 5, 2001 Rev: 1.1 TABLE OF CONTENTS 1 PRODUCT SUMMARY...4 2 AXIS IP SURVEILLANCE FLAGSHIP PRODUCT...4 2.1
1ms Column Parallel Vision System and It's Application of High Speed Target Tracking
 Proceedings of the 2(X)0 IEEE International Conference on Robotics & Automation San Francisco, CA April 2000 1ms Column Parallel Vision System and It's Application of High Speed Target Tracking Y. Nakabo,
Proceedings of the 2(X)0 IEEE International Conference on Robotics & Automation San Francisco, CA April 2000 1ms Column Parallel Vision System and It's Application of High Speed Target Tracking Y. Nakabo,
Network Camera Operating Manual
 Network Camera Operating Manual Model No. WV-NW484S Before attempting to connect or operate this product, please read these instructions carefully and save this manual for future use. Preface About these
Network Camera Operating Manual Model No. WV-NW484S Before attempting to connect or operate this product, please read these instructions carefully and save this manual for future use. Preface About these
Basic Pattern Recognition with NI Vision
 Basic Pattern Recognition with NI Vision Author: Bob Sherbert Keywords: National Instruments, vision, LabVIEW, fiducial, pattern recognition This tutorial aims to instruct the reader on the method used
Basic Pattern Recognition with NI Vision Author: Bob Sherbert Keywords: National Instruments, vision, LabVIEW, fiducial, pattern recognition This tutorial aims to instruct the reader on the method used
