Subchains: A Technique to Scale Bitcoin and Improve the User Experience
|
|
|
- David Bryant
- 6 years ago
- Views:
Transcription
1 RESEARCH ARTICLE Subchains: A Technique to Scale Bitcoin and Improve the User Experience Peter R. Rizun * Abstract. Orphan risk for large blocks limits Bitcoin s transactional capacity while the lack of secure instant transactions restricts its usability. Progress on either front would help spur adoption. This paper considers a technique for using fractional-difficulty blocks (weak blocks) to build subchains bridging adjacent pairs of real blocks. Subchains reduce orphan risk by propagating blocks layer-by-layer over the entire block interval, rather than all at once when the proof-of-work is solved. Each new layer of transactions helps to secure the transactions included in lower layers, even though none of the transactions have been confirmed in a real block. Miners are incentivized to cooperate building subchains in order to process more transactions per second (thereby claiming more fee revenue) without incurring additional orphan risk. The use of subchains also diverts fee revenue towards network hash power rather than dripping it out of the system to pay for orphaned blocks. By nesting subchains, weak block verification times approaching the theoretical limits imposed by speed-of-light constraints would become possible with future technology improvements. As subchains are built on top of the existing Bitcoin protocol, their implementation does not require any changes to Bitcoin s consensus rules. 1. Introduction Bitcoin s performance as a payment network is hardly impressive. In 2015, it processed an average of 1.4 transactions per second while merchants waited on average eight minutes to receive initial verification from a miner that a transaction would likely be included in the permanent Blockchain ledger. 1, 2 In contrast, the Visa network processed over 2,000 transactions per second, 3 and with chip-and-pin technology merchants received authorization and PINverification in under a second. 4 Unlike Visa, Bitcoin s transactional capacity is limited in part due to miners hesitation to produce blocks containing large volumes of new transactions. 5 Such blocks propagate across the network slowly, 6, 11 increasing the chances that the block is orphaned and the miner s reward is lost. 7 Also unlike Visa, the initial verification of a transaction by a miner is delayed because blocks are propagated on average only every ten minutes, 8 rather than at a rate dynamically tuned to the bandwidth and latency of the network. In this paper, we present a scaling technique called subchains to build blocks layer-by-layer at a small fraction of Bitcoin s ten-minute block time thereby reducing both orphaning risk and the wait-time for the first verification of a transaction by a miner. Throughout this paper, we make certain simplifying assumptions. In particular, we assume that: (Asm. 1) Information propagates from the miner who solves a block to the other miners according to the simplified model τ = τ 0 + zq, where τ is the propagation time, Q is the number of bytes propagated, and z and τ 0 are empirical constants. 6, 9, 10, 11 (Block validation time is assumed to be included in the propagation time.) P. R. Rizun, Ph.D. (peter.rizun@gmail.com) is Chief Scientist for Bitcoin Unlimited and resides in Vancouver, Canada. *1BWZe6XkGLcf6DWC3TFXiEtZmcyAoNq5BW
2 (Asm. 2) The market for block space is one of perfect competition. 12 (Asm. 3) The protocol-enforced block size limit if such a limit exists is greater than the free-market equilibrium block size. That is, the block size is constrained by natural supply and demand, rather than by a production quota. (Asm. 4) The network consists of default-compliant miners who reliably follow the agreed-upon protocol and petty-compliant miners who will deviate from the protocol to facilitate double-spend attacks if such behavior is profitable. 13 The total hash power controlled by petty-compliant miners is χ 50%. This paper makes the following contributions: Contribution 1: Description of the subchain technique. In Section 3, we describe the subchain technique, 14 which is a practical application of weak blocks 15, 16, 17, 18 that provides incentives for miners to cooperate for the mutual benefit of the network. Its implementation requires neither a hard nor soft fork but it does require participation from a significant fraction of the network hash power in order to be useful. In Section 9, we illustrate how subchains can be nested, creating a fractal-like blockchain structure where transactions are processed almost continuously. Contribution 2: Reduced orphan risk. A significant advantage of the subchain technique is revealed in Section 4, when we show how the technique considerably reduces orphan risk for a given sized block. The reduced orphan risk is due to the fact that the block is built layer-bylayer over the ten-minute block interval, rather than propagated all at once the moment the proof-of-work is solved. Using subchains, miners can cooperate to process more transactions per second for a given level of orphan risk. Contribution 3: Existence of a fee market. We move onto the economics of the transaction fee market in Section 5. We show that although a miner can include all of the subchain s transactions in his block candidate and thus all of the subchain s fees without incurring additional orphan risk, he still incurs extra orphan risk for new transactions included in his block candidate. This property drives a fee market and economically restricts the rate of subchain growth. Contribution 4: Proof-of-work security from fee revenue. Certain investigators have argued that fees that result from orphan risk cannot contribute to network security. 19 With a simple diagram, we prove this line of reasoning false in Section 6 by showing that the fees already included in the subchain contribute directly to network security in the same way that the block reward does. Only the fees in the new transactions added on top of the subchain go to cover the orphan risk for those transactions. The total fees in a typical block are thus much larger than the block s total orphan risk. Contribution 5: Security for unconfirmed transactions. In Section 7 we review the doublespend security offered by unconfirmed transactions under standard block propagation rules, and explain why a lower bound on that security is zero. We then show that double-spending a transaction verified in a subchain has an objectively-measurable cost commensurate with the total fees that have accumulated in the subchain above the transaction an attacker is attempting to double-spend. 2. List of Symbols For the remainder of this manuscript, the following symbols have the specified meanings. C expected cost due to orphan risk t time F fees X subchain factor (weak blocks 39
3 expected per strong block) P orphan probability of an orphan race z propagation impedance Q block size or block space in bytes χ hash power controlled by petty-compliant miners ΔQ size of Δ-block τ propagation time T block interval (10 min target) τ 0 network latency ΔT Δ-block (weak block) interval Δτ propagation time minus latency 3. Weak Blocks and Subchains To append a new block to the Blockchain, a miner must find a valid proof-of-work. This entails finding a nonce that when hashed together with the previous block s hash and the root hash for the block s transactions, results in an integer less than the network difficulty target. 20 We define a weak block as a block that satisfies the weaker requirement hash(previous hash, nonce, root hash) < weak target, where the weak target is larger than the difficulty target. More plainly, a weak block is a block with enough proof-of-work to be hard to find, but not enough to be a real block. By sharing these weak blocks, miners can cooperate to build subchains (Fig. 1). Fig. 1. Miners cooperate to build subchains in order to process more transactions and claim more fees without incurring additional orphaning risk. This illustration visualizes ¼- difficulty idealized subchains; due to the luck associated with finding a valid proof-ofwork, in reality some strong blocks would contain more than four weak blocks and some would contain less. Upon accepting a (strong) block, miners begin working on creating the next block in the chain by using the hash of the accepted block as the previous hash (Fig. 2a). When a miner finds a proof-of-work that satisfies the weak target, he broadcasts the weak block to the network. After verifying the weak block, each miner modifies the coinbase reward, appends additional transactions to the block if desired, computes the new root hash, and then continues scanning for a valid nonce (Fig. 2b). We will refer to the new information as the miner s Δ- block (Fig. 2f). If again a miner finds a proof-of-work that satisfies the weak target, he broadcasts the new weak block by sending only his Δ-block and the hash of the previous weak block. In this manner, miners can cooperate to build the subchain by transmitting only the new information and a hash that references the subchain s tip. When a miner finds a proof-of-work that meets the strong target (Fig. 2d), he broadcasts it in the same manner he would for a weak block (i.e., by sending only his Δ-block and the hash of the previous weak block). Nodes recognize this as a valid (strong) block, retain the nonce 40
4 and coinbase transaction, and close the subchain. The process of constructing a subchain on top of this latest block begins anew (Fig. 2e). Fig. 2. Miners build subchains layer by layer (a c), where each new layer corresponds to the solution of a weak block. In (b d), the subchain (light gray) is common across the network, but the Δ-block is unique to the particular miner. To propagate blocks (weak or strong), miners need only send their Δ-block and a hash that references to the subchain s tip (f), thereby reducing the number of bytes transmitted the moment the proof-of-work is solved. When a nonce that satisfies the strong target is found, the subchain is closed thereby becoming a strong block (d), and miners begin working on a new subchain (e). If more than a single subchain exists, compliant miners build off the longest subchain. In cases where two subchains of equal length exist, miners work on the one they knew about first, switching to the other if it becomes longer. For conflicting (double-spent) transactions, the transaction verified in a subchain has priority over one only admitted into mempool. Note that this behavior represents a departure from the Satoshi protocol where miners will only replace transactions in mempool if a conflicting transaction is included in a strong block (subchains extend this behavior to weak blocks too). This departure is necessary so that miners, under normal conditions, converge upon a single subchain. For the remainder of this paper, mempool is redefined as the set of transactions that have been neither confirmed in a strong block nor verified in a weak block. 4. Reduced Orphan Risk A block is orphaned whenever two miners find competing solutions for the next block. The probability of this event depends on how quickly news of a new block spreads across the network. If a block takes time τ to propagate, the probability that the network finds another block during the propagation interval 0 < t < τ is given by 41
5 τ P orphan = 1 t T e Tdt 0 = 1 e τ T, (1) where 1 t T e T is of course the probability distribution for the arrival time of a valid proof-ofwork. 21, 22, 23 Subchains reduce a block s propagation time (τ) because only the most recentlyadded transactions need to be propagated, thereby reducing the probability of orphaning. Assuming that miners produce equal-sized Δ-blocks with an average period of T, each Δ- block is scaled down by the subchain factor, T ΔT, such that Q = Q. The propagation time ΔT T (cf. Asm. 1) is thus τ = z Q + τ 0, from which it follows that P orphan = 1 e τ 0 T e zqδt T 2. This equation is plotted in Fig. 3 for various subchain factors and using recent estimates for 6, 9, 11, 24 the network propagation constants (z = 17 s/mb and τ 0 = 10 s). Fig. 3. Subchains help scale Bitcoin by reducing orphan risk for larger block sizes. This chart is based on recent estimates for the network propagation constants (z = 17 s/mb and τ 0 = 10 s). 6, 9, 11 For example, a subchain with a target weak block time of 38 s would permit approximately sixteen times more transactions per second at the same level of orphaning risk as without the subchain. The minimum subchain verification time is limited, however, due to network latency (shaded region). A subchain with T = X would permit approximately X times more transactions per second at ΔT the same level of orphaning risk as without the subchain. The minimum useful subchain verification time is limited, however, because the network cannot come to consensus regarding the subchain faster than the network s latency (which, regardless of technology advancements, is limited by the product of the network diameter and the speed of light to approximately 0.1 s)
6 5. Existence of a Fee Market LEDGER VOL 1 (2016) With conventional block propagation, a miner must balance the additional fee revenue he earns by making his block bigger, with the decreased orphan risk he enjoys by making his block smaller. 26 The free-market equilibrium block size is the point where a smaller block would result in a smaller expected profit due to too many fees left in mempool, while a larger block would also result in a smaller expected profit due to too high an orphan risk. The author describes this equilibrium in detail in his paper on Bitcoin s transaction fee market. 5 This equilibrium changes in one important way in a scenario where subchains are the default mechanism to build and propagate blocks: a miner can now include all of the subchain s transactions in his block candidate and thus all of its fees without affecting the block s orphan risk. The reason this is possible is because the miner can now reference the entirety of the subchain with a single hash; the propagation time for that hash does not depend on the size of the subchain that the hash references. The fees in each propagated Δ-block thus add to the subchain s pot, increasing the effective block reward (as indicated by the black points in Fig. 4a at Q 1, Q 2 and Q 3 ) but without increasing the expected cost of mining the block. Fig. 4. (a and b) The total fees in a subchain increase each time a Δ-block gets added, effectively growing the pot. Since a miner incurs no orphaning risk by including the contents of the subchain in his block candidate, he is incentivized to build his Δ-block on top of the highest-fee subchain. However, a miner incurs normal orphaning risk for any new transactions he chooses to add. Because of this, he will only include new transactions that pay more in fees per byte than the marginal cost of producing the extra block space to hold those transactions. The block of maximum profit is thus the point where the marginal cost curve (d C /dq) intersects the marginal fee curve (df/dq). 43
7 1 P orphan ( Q) 1 P orphan (0) A miner does, however, still incur orphan risk for the new transactions included in his Δ- block. The larger he makes his Δ-block, the slower it would propagate across the network, and in the case where he finds a strong block the greater the risk he incurs of having his block orphaned and losing the block reward. The expected cost, C, associated with the risk of producing new block space is depicted in Fig. 4a as a function of block size. By assuming only that block space obeys the law of supply, 27 it follows that this curve is superlinear in Q. 28 (The concavity can also be deduced using technical arguments 29 : let c be the value of a valid proof of work and let P orphan (Q) represent the probability that a block transmitted using Q bytes is orphaned. By including Q bytes of new transactions in his Δ-block, a miner is worse c c off by an amount C = compared to including no new transactions. Using Eq. (1) for the orphaning probability and using the substitution (τ τ 0 ) z Q from Assum. 1 gives C = ce τ 0 z Q T (e T 1) a superlinear function of Q as expected.) The other curve in Fig. 4a represents the maximum fees, F, available from transactions in mempool for a block of size Q. It follows, by definition, that this curve is sublinear. 30 The miner s expected profit is greatest at the block size that maximizes the difference between these two curves, which from elementary calculus occurs at the point where the two curves have equal slopes (i.e., when d C /dq = df/dq), or, translated into the language of economics, at the 5, 31, 32 point where the marginal expected cost is equal to the marginal fee revenue (cf. Fig. 4b). Each miner will dynamically adjust his block candidate as new transactions enter mempool, to continually maximize his expected profit. The existence of this equilibrium indicates that a transaction fee market based on orphaning risk exists. Miners are naturally incentivized to share each -block they find, as doing so reduces the orphan risk for their candidate block. 6. Proof-of-Work Security From Fee Revenue It is simple to show that fees contribute to proof-of-work security if the network uses the subchain technique (even in the absence of a block size limit). Fig. 5 is a modification of Fig. 4a that considers all of the miner s revenues and costs, including the block reward and electricity for hashing. In a competitive market, the profits for marginal miners will trend to zero. To reconcile this fact with Fig. 5, the total production costs for block space must increase such that the two points marked in purple move closer together. That is, if industry profits were large, miners would tend to deploy more hash power to compete for this profit, thereby shifting the entire production cost curve upwards, increasing hashing costs (due to a rise in network difficulty) and decreasing profits. As shown in Fig. 5, the fee revenue is significantly greater than the orphan risk; this fee revenue captured Δ-block-by-Δ-block in the subchain acts no differently than an increase in the block reward would: it serves to increase the network hash rate. We have now shown that fees contribute to proof-of-work security when using the subchain technique. One subtlety to note is that a miner with revenues and costs as depicted in Fig. 5 would not start to mine until the subchain contained sufficient fees to make the expectation value of his profit positive. 33 Presently, fees are such a small fraction of the block reward that most miners are profitable regardless of fees. However, when total fees are no longer small compared to the block reward, we would expect the instantaneous hash rate to increase every time a new Δ- block (and its fees) is added, as miners with marginally higher electricity costs turn on their machines. Further discussion of this phenomenon is beyond the scope of this paper. 44
8 Fig. 5. If excess mining profits are available due to high fees, miners will deploy more hash power to compete for that profit. This causes network difficulty to increase, shifting the curve marked expected total cost upwards and reducing industry profits. Fees thus contribute directly to proof of work security by making it more difficult to mine a block. 7. Improved Security for Unconfirmed Transactions Double-spending today Consider a scenario where a scammer (a dishonest customer) purchases a cup of coffee from a merchant, pays with a bitcoin transaction, and then later tries to double-spend that transaction to reverse his payment. After broadcasting his transaction (and assuming he pays a sufficient fee), nodes relay it across the network, miners incorporate it into their block candidates, it registers with the merchant s listening node, and the merchant hands the cup of coffee to the scammer. Shortly after leaving the merchant s shop with coffee in hand, the scammer then broadcasts the double-spend transaction shown in red in Fig. 6. He attaches a bribe in the form of a higher transaction fee trying to entice miners to replace the legitimate transaction with the red transaction, so that the payment to the merchant is never confirmed in a block. 45
9 Fig. 6. When offered a bribe to help facilitate a double-spend attack on an unconfirmed transaction, miners can behave in two different ways. Default-compliant miners accept only the first-seen version of a transaction and thus reject the bribe, as specified by the protocol. Petty-compliant miners recognizing the profit potential of swapping the two transactions disobey the protocol and accept the bribe. The double-spend succeeds with a probability equal to the fraction of the hash power controlled by petty-compliant miners. Because the Bitcoin protocol specifies that a miner must accept only the first-seen version of a transaction into his mempool, a default-compliant miner would not accept the bribe. On the other hand, a petty-compliant miner recognizing the profit potential of swapping the two transactions would. Assuming that petty-compliant miners control a fraction χ of the hash power, this double-spend attack thus succeeds with probability χ (i.e., the probability that a petty-compliant miner finds the next block). Since this petty-compliant behavior remains profitable for even infinitesimally small bribes, it is sometimes said that the lower bound on the security of unconfirmed transactions in Bitcoin is zero. Double-spending with subchains To illustrate how subchains improve the security of unconfirmed transactions, we imagine the same double-spend attempt unfolding in a future where miners build blocks using the subchain technique. In this new scenario, when the scammer has left the merchant s shop and broadcasts the double-spend transaction, assume the original green transaction is already verified in a weak block, with additional weak blocks stacked above it, as shown in Fig. 7. Petty-compliant miners can no longer simply swap the red transaction with the green transaction because doing so would break the subchain. To accept the bribe, each petty-compliant miner must now build his block candidate from a layer in the subchain prior to the inclusion of the legitimate (green) transaction. This requirement imposes a real cost on the petty-compliant miner. By following the default strategy, the miner could have included all of the fees in the subchain for zero cost; but by building off an earlier layer in the subchain instead, he either forfeits the fees in the transactions verified in the higher layers or he accepts the added orphaning risk of re-propagating those transactions in the event that he solves the next strong block. To entice this petty-compliant behavior, it follows that the scammer must offer a significant bribe, as explained next. 46
10 Fig. 7. If default-compliant miners build blocks using the subchain protocol, a pettycompliant miner can no longer swap the green transaction for the red double-spent version without breaking the subchain. To accept the bribe, he must build a block candidate referencing an earlier layer in the subchain. This adds a measurable cost to the double-spend attack. In a perfectly competitive market, miners include in their block candidates any transaction that pays a fee per byte greater than the expected cost of including the transaction (i.e., greater than the transaction s marginal orphaning risk). Although we will not be rigorous here, it follows that the fee on a typical transaction in the subchain will thus be only slightly greater than the expected cost of including that transaction. The cost that the miner bears by mining from an earlier layer in the subchain thus depends on the total fees in the higher layers that he leaves behind, and so the scammer must offer a bribe commensurate with the total fees. The fees in each new weak block found further increase the transaction s security. Despite the increased cost of attempting this double-spend attack, its probability of success remains unchanged and equal to the fraction of the hash power that engages in petty-compliant behavior. Fig. 8. The cost of the attack depends on the fees above the transaction to be double-spent. As the subchain grows, the miner attempting the attack misses out on being able to claim more and more fees in the pre-propagated transactions, and thus he demands a larger and larger bribe in order to continue the attack. 8. Nested Subchains Miners must agree on the target number of weak blocks per strong block in order for the subchain technique to work. There appears to be a tradeoff in choosing that target: targeting too few weak blocks would lead to higher orphan risk and slower subchain verifications while targeting too many may result in weak blocks found so quickly that convergence upon a single subchain fails. A possible solution to avoid this tradeoff is to use nested subchains (Fig. 9). 47
11 Fig. 9. In a regular subchain, targeting too few weak blocks per strong block would lead to higher orphan risk and slower subchain verifications while targeting too many may result in weak blocks found so quickly that convergence upon a single subchain fails. Subchains can be nested to avoid this tradeoff. This image shows idealized trinary nesting of Δ-blocks. A nested subchain is simply a subchain within a subchain. When a miner finds a block that satisfies the subchain difficulty, the deeper subchain is closed and a new subchain at the deeper level begins. Miners build from the longest subchain at a given nesting depth but ignore longer subchains at deeper nestings. As miner connectivity improves, the subchain verification times can be reduced by adding deeper levels of nesting, fundamentally limited only by the time is takes light to travel across the network. 9. Related Work Bitcoin s 10-minute block time has long been a frustration for users, spurring developers to create new cryptocurrencies with faster block times. For example, Litecoin has a block time of 2.5 minute while Dogecoin has a block time of 1 minute. Although subchains decrease network orphan rates, reducing the inter-block time has the opposite effect of increasing them. For example, while Bitcoin s orphan rate is approximately 1%, Litecoin s and Dogecoin s orphan rates (as measured by ProHashing) are 6% and 11%, respectively. 34 Although a finite orphan rate is helpful in driving a fee market, a very large orphan rate has the negative effect of disproportionately benefiting mining pools that control a large fraction of the network hash power. 35 This limits the extent to which faster block times could be used to speed up transaction verification (even if such a change were politically feasible). In the wake of Bitcoin hitting its 1 MB block size limit in the summer of 2015, engineers and researchers began working on the problem of scalability in earnest. A simple but highly effective improvement to block propagation was implemented by Peter Tschipper in the Bitcoin Unlimited client. Known as Xtreme Thin Blocks, 36 this Bloom-filter based technique allowed blocks to be transmitted with 24 times fewer bytes and over 5.6 times faster than using conventional block propagation. 37 It can be used together with subchains for the propagation Δ-blocks, providing better scalability than either technique applied on its own. More radical scalability proposals that would involve changes to Bitcoin s consensus rules have also received substantial interest. Bitcoin-NG separates Bitcoin s conventional blocks into leader blocks containing the proof-of-work followed by micro-blocks containing the transactions. 38 Because the transactions are sent after the proof-of-work, orphan risk is not only reduced, it is eliminated entirely. Another related scalability proposal is known as braids. 39 Rather than referencing only a single block as a parent (as required by the Bitcoin protocol and orphaning any competing 48
12 parents), the braid technique allows a miner to reference any number of parents, also potentially eliminating orphans. It is not however clear that eliminating orphan risk is a net positive. As described in Section 5, it is the small amount of remaining orphan risk that would help drive a transaction fee market if miners were to adopt the subchain protocol. What the transaction fee market would look like if Bitcoin-NG or braids were implemented is not clear. 10. Conclusion We presented a technique called subchains designed to improve the security of unconfirmed transactions and increase the number of transactions per second the Bitcoin network can process. Subchains are formed as a series of weak blocks, with the next weak block building a new layer of transactions upon the previous weak block. Miners transmit blocks (both weak and strong) by sending only the latest layer of transactions along with a hash that references the previous layers. The bulk of this paper was dedicated to exploring four important properties that would emerge if the subchain technique were widely deployed by the network s hash power. These properties were: (Prop. 1) Reduced orphan risk for a given block size. (Prop. 2) Continued existence of a transaction fee market. (Prop. 3) Increased proof-of-work security from fee revenue. (Prop. 4) Improved double-spend security for unconfirmed transactions. Although these are obviously desirable properties, it is important to note that they may fail to emerge if the assumptions listed in Section 1 are not realistic. For example, to show how subchains reduce orphan risk (Section 4), we assumed a simple linear model for the propagation time of block information between miners. In reality, propagation times have a stochastic element and also certain miners will be better connected to the network hash power than others. 40, 41 Despite these weaknesses, the model used captures the critical fact that communicating more information generally takes longer, and so we believe the results developed in Section 4 will apply, at least qualitatively, to a wide range of practical scenarios. In Section 5 and 6, we assumed the market for block space was perfectly competitive when analyzing how large a rational miner would make his -block. In practice, however, miners often use the default mining settings and thus leave profit opportunities on the table. In the future, we believe miners will spend more time optimizing these settings in order to increase their profit margins, as the mining industry becomes more competitive. The perfectcompetition assumption will thus become increasingly accurate. We also assumed that the protocol-enforced block size limit (if one exists) was greater than the free-market equilibrium block sizes produced by miners. This was the regime that Bitcoin was operating under from January 2009 until mid If the network continues operating in a saturated-block regime as it does today, the marginal orphan risk for a given transaction could be significantly less than that transaction s fee, and so the benefit to miners of cooperating to build subchains would be reduced. The double-spend resistance of unconfirmed transactions would likewise suffer. Our examination of double-spend security in Section 7 assumed that the majority of the hash power was default-compliant. If instead, the majority of the hash power were pettycompliant willingly facilitating double-spend attacks when bribed then we expect that the 49
13 increased security for unconfirmed transactions delivered by the subchain technique would be lost (along with much of the technique s other benefits). Other real-world effects were also overlooked in this paper. For example, subchains would produce a side effect on the replace-by-fee (RBF) logic incorporated into some Bitcoin clients (e.g., Bitcoin Core). RBF is essentially a tool to make it easier for users to bribe miners to swap the first-seen version of a transaction with a double-spent version. However, rather than facilitating fraud, RBF s stated aim is to provide a means for users to unstick transactions stuck due to too low a fee. RBF will work unchanged with the proposed subchain technique for transactions that have not yet been included in the longest subchain; however, RBF will no longer work (or will require a much greater bribe ) for transactions that have been included. This is not a problem, however, because in this latter case, the transaction is very likely to be included in the next block anyways, so the user has little reason to bump the transaction s fee. Finally, although miners would benefit by using the subchain technique if other miners also used it, during the bootstrapping phase before the protocol is widely deployed, supporting both standard block propagation and the subchain technique may impose a net cost on forward-thinking miners. How we would move from the current block propagation regime to the more efficient subchain regime is not clear. That said, the author believes that networkwide support for subchains would add significant transactional capacity and improve the user experience, helping to further advance the adoption of Bitcoin. Acknowledgement The author gratefully acknowledges the kind review and suggestions of Gavin Andresen, awemany and the three anonymous reviewers. He also acknowledges Gregory Maxwell for motivating him to investigate fee market dynamics in scenarios where information is prepropagated, and he thanks the many thoughtful and intelligent individuals at the Bitcoin Forum (bitco.in) for hours of pleasant and productive discussion. Notes and References 1 Total Number of Transactions chart. Blockchain.info (13 December 2015) 2 Median Transaction Confirmation Time (With Fee Only) chart. Blockchain.info (13 December 2015) 3 Scalability. Bitcoin Wiki (13 December 2015) 4 Murdoch, S. J., Drimer, S., Anderson, R., Bond, M. Chip and PIN is Broken IEEE Symposium on Security and Privacy, Oakland, California (16 May 2010) 5 Rizun, P. R. A Transaction Fee Market Exists Without a Block Size Limit. No Publisher (2015) 6 Stone, G. A. An Examination of Bitcoin Network Throughput Via Analysis of Single Transaction Blocks. No Publisher (2015) 7 Rizun, P. R. The marginal cost of adding another transaction to a block is nonzero: empirical evidence that bigger blocks are more likely to be orphaned. Reddit (16 July 2016) _another_transaction/ 50
14 8 Barski, C., and Wilmer, C. Bitcoin for the Befuddled. San Francisco: No Starch Press (2014) 9 Bitcoin Network Capacity Analysis Part 6: Data Propagation. Tradeblock Blog (23 June 2015) data-propagation 10 Decker C., Wattenhofer R. Information Propagation in the Bitcoin Network. 13th IEEE International Conference on Peer-to-Peer Computing, Trento, Italy, September Croman, K., et al. On Scaling Decentralized Blockchains. Financial Cryptography and Data Security Perfect competition. Wikipedia Carlsten, M., Kalodner, H., Weinberg, S. M., Narayanan, A. On the Instability of Bitcoin Without the Block Reward. ACM CCS Pseudonymous ( rocks ). Comment in Gold Collapsing. Bitcoin UP. Bitcoin Forum. (12 November 2015) 99#post Andresen, G. [Bitcoin-development] Weak block thoughts Bitcoin-development (23 September 2015) September/ html 16 Pseudonymous ( TierNolan ). Decoupling transactions and POW. Bitcointalk (18 April 2013) 17 Andresen, G., Comment in Faster blocks vs bigger blocks. Bitcointalk (3 July 2014) 18 Rosenbaum, K., Russell, R. IBLT and Weak Block Propagation Performance. Scaling Bitcoin Hong Kong (6 December 2015) 19 Maxwell, G. [Bitcoin-development] Block Size Increase. Bitoin-development 7 May 2015 (accessed 13 December 2015) May/ html 20 BitFury Group. Proof of Stake versus Proof of Work. No Publisher (13 September 2015) 21 Andresen, G. Back-of-the-envelope calculations for marginal cost of transactions. No Publisher (2013) 22 Here we have made the assumption that the network hash rate is constant over the time scale at which new blocks are found. This assumption will likely no longer hold when fees are significant compared to the block reward, however, the underlying intuition regarding subchains effect on block races will be unchanged. 23 If large miners are present, this equation overstates the orphan rate, due to the fact that a miner does not have to propagate his solved blocks to himself. 24 The actual latency and propagation impedance are both likely smaller as the methodology used by Stone includes other effects such as the time to construct a new block candidate from mempool, and the methodology used by Tradeblock and Croman et al. measured propagation to nodes rather than to hash power. 25 Pseudonymous ( awemany ). Comment in Block Space as a Commodity. Bitcoin Forum (26 September 2015) 51
15 transaction-fee-market-exists-without-a-block-size-limit.58/page-4#post Houy, N. The Bitcoin Mining Game. SSRN (11 March 2014) Law of supply. Wikipedia The derivative of this curve is a monotonically increasing function of Q via the law of supply, thus this curve is necessarily superlinear in Q. 29 For more details, see Section 5 and Section 7 in the paper cited in endnote For more details, see Section 4 in the paper cited in endnote Pinna, D. On the Nature of Miner Advantages in Uncapped Block Size Fee Markets. No Publisher (2015) Advantages-in-Uncapped-Block-Size-Fee-Markets 32 BitFury Group. Incentive Mechanisms for Securing the Bitcoin Blockchain. No Publisher (2015) 33 Carlsten, M., Kalodner, H., Narayanan, A. Mind the Gap: Security Implications of the Evolution of Bitcoin Mining. Scaling Bitcoin Montreal (12 September 2015) 34 The orphan rates for Litecoin and Dogecoin represent those experienced by the ProHashing pool and not the overall network orphan rates Todd, P. Block Publication Incentives for Miners. No Publisher (29 June 2016) Tschipper, P., BUIP010: Xtreme Thinblocks. Bitcoin Forum (1 January 2016) Clifford, A., Rizun, P. R., Suisani, A., Stone, G. A., Tschipper, P. Towards Massic On-chain Scaling: Block Propagation Results With Xthin. Part 5 of 5: Massive on-chain scaling begins with block sizes up to 20 MB. Medium (13 Jun 2016) Eyal, I., Gencer, A. E., Sirer, E. G., van Renesse, R. Bitcoin-NG: A Scalable Blockchain Protocol. arxiv (7 October 2015) McElrath, B. Brading the Blockchain. Presentation at Scaling Bitcoin Hong Kong (7 December 2015). e_chain_1_mcelrath.pdf 40 Clifford, A., Rizun, P. R., Suisani, A., Stone, G. A., Tschipper, P. Towards Massic On-chain Scaling: Block Propagation Results With Xthin. Part 3 of 5: Xthin blocks are less affected by the Great Firewall of China than standard blocks. Medium (4 Jun 2016). massive-on-chain-scaling-block-propagation-results-with-xthin- 792a752c14c2 41 Simply being a larger miner makes one better connected to the network hash power as one s connection with one s own hash power is usually very fast. 52
Figure 9.1: A clock signal.
 Chapter 9 Flip-Flops 9.1 The clock Synchronous circuits depend on a special signal called the clock. In practice, the clock is generated by rectifying and amplifying a signal generated by special non-digital
Chapter 9 Flip-Flops 9.1 The clock Synchronous circuits depend on a special signal called the clock. In practice, the clock is generated by rectifying and amplifying a signal generated by special non-digital
from ocean to cloud ADAPTING THE C&A PROCESS FOR COHERENT TECHNOLOGY
 ADAPTING THE C&A PROCESS FOR COHERENT TECHNOLOGY Peter Booi (Verizon), Jamie Gaudette (Ciena Corporation), and Mark André (France Telecom Orange) Email: Peter.Booi@nl.verizon.com Verizon, 123 H.J.E. Wenckebachweg,
ADAPTING THE C&A PROCESS FOR COHERENT TECHNOLOGY Peter Booi (Verizon), Jamie Gaudette (Ciena Corporation), and Mark André (France Telecom Orange) Email: Peter.Booi@nl.verizon.com Verizon, 123 H.J.E. Wenckebachweg,
The Measurement Tools and What They Do
 2 The Measurement Tools The Measurement Tools and What They Do JITTERWIZARD The JitterWizard is a unique capability of the JitterPro package that performs the requisite scope setup chores while simplifying
2 The Measurement Tools The Measurement Tools and What They Do JITTERWIZARD The JitterWizard is a unique capability of the JitterPro package that performs the requisite scope setup chores while simplifying
How to Obtain a Good Stereo Sound Stage in Cars
 Page 1 How to Obtain a Good Stereo Sound Stage in Cars Author: Lars-Johan Brännmark, Chief Scientist, Dirac Research First Published: November 2017 Latest Update: November 2017 Designing a sound system
Page 1 How to Obtain a Good Stereo Sound Stage in Cars Author: Lars-Johan Brännmark, Chief Scientist, Dirac Research First Published: November 2017 Latest Update: November 2017 Designing a sound system
Chapter 12. Synchronous Circuits. Contents
 Chapter 12 Synchronous Circuits Contents 12.1 Syntactic definition........................ 149 12.2 Timing analysis: the canonic form............... 151 12.2.1 Canonic form of a synchronous circuit..............
Chapter 12 Synchronous Circuits Contents 12.1 Syntactic definition........................ 149 12.2 Timing analysis: the canonic form............... 151 12.2.1 Canonic form of a synchronous circuit..............
At-speed testing made easy
 At-speed testing made easy By Bruce Swanson and Michelle Lange, EEdesign.com Jun 03, 2004 (5:00 PM EDT) URL: http://www.eedesign.com/article/showarticle.jhtml?articleid=21401421 Today's chip designs are
At-speed testing made easy By Bruce Swanson and Michelle Lange, EEdesign.com Jun 03, 2004 (5:00 PM EDT) URL: http://www.eedesign.com/article/showarticle.jhtml?articleid=21401421 Today's chip designs are
Cryptanalysis of LILI-128
 Cryptanalysis of LILI-128 Steve Babbage Vodafone Ltd, Newbury, UK 22 nd January 2001 Abstract: LILI-128 is a stream cipher that was submitted to NESSIE. Strangely, the designers do not really seem to have
Cryptanalysis of LILI-128 Steve Babbage Vodafone Ltd, Newbury, UK 22 nd January 2001 Abstract: LILI-128 is a stream cipher that was submitted to NESSIE. Strangely, the designers do not really seem to have
Design Project: Designing a Viterbi Decoder (PART I)
 Digital Integrated Circuits A Design Perspective 2/e Jan M. Rabaey, Anantha Chandrakasan, Borivoje Nikolić Chapters 6 and 11 Design Project: Designing a Viterbi Decoder (PART I) 1. Designing a Viterbi
Digital Integrated Circuits A Design Perspective 2/e Jan M. Rabaey, Anantha Chandrakasan, Borivoje Nikolić Chapters 6 and 11 Design Project: Designing a Viterbi Decoder (PART I) 1. Designing a Viterbi
Technical Appendices to: Is Having More Channels Really Better? A Model of Competition Among Commercial Television Broadcasters
 Technical Appendices to: Is Having More Channels Really Better? A Model of Competition Among Commercial Television Broadcasters 1 Advertising Rates for Syndicated Programs In this appendix we provide results
Technical Appendices to: Is Having More Channels Really Better? A Model of Competition Among Commercial Television Broadcasters 1 Advertising Rates for Syndicated Programs In this appendix we provide results
in the Howard County Public School System and Rocketship Education
 Technical Appendix May 2016 DREAMBOX LEARNING ACHIEVEMENT GROWTH in the Howard County Public School System and Rocketship Education Abstract In this technical appendix, we present analyses of the relationship
Technical Appendix May 2016 DREAMBOX LEARNING ACHIEVEMENT GROWTH in the Howard County Public School System and Rocketship Education Abstract In this technical appendix, we present analyses of the relationship
sr c0 c3 sr c) Throttled outputs Figure F.1 Bridge design models
 WHITE PAPER CONTRIBUTION TO 0 0 0 0 0 Annex F (informative) Bursting and bunching considerations F. Topology scenarios F.. Bridge design models The sensitivity of bridges to bursting and bunching is highly
WHITE PAPER CONTRIBUTION TO 0 0 0 0 0 Annex F (informative) Bursting and bunching considerations F. Topology scenarios F.. Bridge design models The sensitivity of bridges to bursting and bunching is highly
Primary Frequency Response Ancillary Service Market Designs
 Engineering Conferences International ECI Digital Archives Modeling, Simulation, And Optimization for the 21st Century Electric Power Grid Proceedings Fall 10-24-2012 Primary Frequency Response Ancillary
Engineering Conferences International ECI Digital Archives Modeling, Simulation, And Optimization for the 21st Century Electric Power Grid Proceedings Fall 10-24-2012 Primary Frequency Response Ancillary
AltiumLive 2017: Effective Methods for Advanced Routing
 AltiumLive 2017: Effective Methods for Advanced Routing Charles Pfeil Senior Product Manager Dave Cousineau Sr. Field Applications Engineer Charles Pfeil Senior Product Manager Over 50 years of experience
AltiumLive 2017: Effective Methods for Advanced Routing Charles Pfeil Senior Product Manager Dave Cousineau Sr. Field Applications Engineer Charles Pfeil Senior Product Manager Over 50 years of experience
On the Characterization of Distributed Virtual Environment Systems
 On the Characterization of Distributed Virtual Environment Systems P. Morillo, J. M. Orduña, M. Fernández and J. Duato Departamento de Informática. Universidad de Valencia. SPAIN DISCA. Universidad Politécnica
On the Characterization of Distributed Virtual Environment Systems P. Morillo, J. M. Orduña, M. Fernández and J. Duato Departamento de Informática. Universidad de Valencia. SPAIN DISCA. Universidad Politécnica
SWITCHED INFINITY: SUPPORTING AN INFINITE HD LINEUP WITH SDV
 SWITCHED INFINITY: SUPPORTING AN INFINITE HD LINEUP WITH SDV First Presented at the SCTE Cable-Tec Expo 2010 John Civiletto, Executive Director of Platform Architecture. Cox Communications Ludovic Milin,
SWITCHED INFINITY: SUPPORTING AN INFINITE HD LINEUP WITH SDV First Presented at the SCTE Cable-Tec Expo 2010 John Civiletto, Executive Director of Platform Architecture. Cox Communications Ludovic Milin,
1022 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 19, NO. 4, APRIL 2010
 1022 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 19, NO. 4, APRIL 2010 Delay Constrained Multiplexing of Video Streams Using Dual-Frame Video Coding Mayank Tiwari, Student Member, IEEE, Theodore Groves,
1022 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 19, NO. 4, APRIL 2010 Delay Constrained Multiplexing of Video Streams Using Dual-Frame Video Coding Mayank Tiwari, Student Member, IEEE, Theodore Groves,
Dual frame motion compensation for a rate switching network
 Dual frame motion compensation for a rate switching network Vijay Chellappa, Pamela C. Cosman and Geoffrey M. Voelker Dept. of Electrical and Computer Engineering, Dept. of Computer Science and Engineering
Dual frame motion compensation for a rate switching network Vijay Chellappa, Pamela C. Cosman and Geoffrey M. Voelker Dept. of Electrical and Computer Engineering, Dept. of Computer Science and Engineering
Skip Length and Inter-Starvation Distance as a Combined Metric to Assess the Quality of Transmitted Video
 Skip Length and Inter-Starvation Distance as a Combined Metric to Assess the Quality of Transmitted Video Mohamed Hassan, Taha Landolsi, Husameldin Mukhtar, and Tamer Shanableh College of Engineering American
Skip Length and Inter-Starvation Distance as a Combined Metric to Assess the Quality of Transmitted Video Mohamed Hassan, Taha Landolsi, Husameldin Mukhtar, and Tamer Shanableh College of Engineering American
BAL Real Power Balancing Control Performance Standard Background Document
 BAL-001-2 Real Power Balancing Control Performance Standard Background Document July 2013 3353 Peachtree Road NE Suite 600, North Tower Atlanta, GA 30326 404-446-2560 www.nerc.com Table of Contents Table
BAL-001-2 Real Power Balancing Control Performance Standard Background Document July 2013 3353 Peachtree Road NE Suite 600, North Tower Atlanta, GA 30326 404-446-2560 www.nerc.com Table of Contents Table
Draft 100G SR4 TxVEC - TDP Update. John Petrilla: Avago Technologies February 2014
 Draft 100G SR4 TxVEC - TDP Update John Petrilla: Avago Technologies February 2014 Supporters David Cunningham Jonathan King Patrick Decker Avago Technologies Finisar Oracle MMF ad hoc February 2014 Avago
Draft 100G SR4 TxVEC - TDP Update John Petrilla: Avago Technologies February 2014 Supporters David Cunningham Jonathan King Patrick Decker Avago Technologies Finisar Oracle MMF ad hoc February 2014 Avago
BAL Real Power Balancing Control Performance Standard Background Document
 BAL-001-2 Real Power Balancing Control Performance Standard Background Document February 2013 3353 Peachtree Road NE Suite 600, North Tower Atlanta, GA 30326 404-446-2560 www.nerc.com Table of Contents
BAL-001-2 Real Power Balancing Control Performance Standard Background Document February 2013 3353 Peachtree Road NE Suite 600, North Tower Atlanta, GA 30326 404-446-2560 www.nerc.com Table of Contents
Low Power VLSI Circuits and Systems Prof. Ajit Pal Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Low Power VLSI Circuits and Systems Prof. Ajit Pal Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No. # 29 Minimizing Switched Capacitance-III. (Refer
Low Power VLSI Circuits and Systems Prof. Ajit Pal Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No. # 29 Minimizing Switched Capacitance-III. (Refer
Hardware Implementation of Viterbi Decoder for Wireless Applications
 Hardware Implementation of Viterbi Decoder for Wireless Applications Bhupendra Singh 1, Sanjeev Agarwal 2 and Tarun Varma 3 Deptt. of Electronics and Communication Engineering, 1 Amity School of Engineering
Hardware Implementation of Viterbi Decoder for Wireless Applications Bhupendra Singh 1, Sanjeev Agarwal 2 and Tarun Varma 3 Deptt. of Electronics and Communication Engineering, 1 Amity School of Engineering
Optimization of Multi-Channel BCH Error Decoding for Common Cases. Russell Dill Master's Thesis Defense April 20, 2015
 Optimization of Multi-Channel BCH Error Decoding for Common Cases Russell Dill Master's Thesis Defense April 20, 2015 Bose-Chaudhuri-Hocquenghem (BCH) BCH is an Error Correcting Code (ECC) and is used
Optimization of Multi-Channel BCH Error Decoding for Common Cases Russell Dill Master's Thesis Defense April 20, 2015 Bose-Chaudhuri-Hocquenghem (BCH) BCH is an Error Correcting Code (ECC) and is used
Set-Top-Box Pilot and Market Assessment
 Final Report Set-Top-Box Pilot and Market Assessment April 30, 2015 Final Report Set-Top-Box Pilot and Market Assessment April 30, 2015 Funded By: Prepared By: Alexandra Dunn, Ph.D. Mersiha McClaren,
Final Report Set-Top-Box Pilot and Market Assessment April 30, 2015 Final Report Set-Top-Box Pilot and Market Assessment April 30, 2015 Funded By: Prepared By: Alexandra Dunn, Ph.D. Mersiha McClaren,
Processes for the Intersection
 7 Timing Processes for the Intersection In Chapter 6, you studied the operation of one intersection approach and determined the value of the vehicle extension time that would extend the green for as long
7 Timing Processes for the Intersection In Chapter 6, you studied the operation of one intersection approach and determined the value of the vehicle extension time that would extend the green for as long
Making the Internet More Free and Accessible For Authors and Readers
 a Making the Internet More Free and Accessible For Authors and Readers A Step towards Decentralization of the Internet 1 Introduction There are no disputes about the fact that the internet has changed
a Making the Internet More Free and Accessible For Authors and Readers A Step towards Decentralization of the Internet 1 Introduction There are no disputes about the fact that the internet has changed
DIFFERENTIATE SOMETHING AT THE VERY BEGINNING THE COURSE I'LL ADD YOU QUESTIONS USING THEM. BUT PARTICULAR QUESTIONS AS YOU'LL SEE
 1 MATH 16A LECTURE. OCTOBER 28, 2008. PROFESSOR: SO LET ME START WITH SOMETHING I'M SURE YOU ALL WANT TO HEAR ABOUT WHICH IS THE MIDTERM. THE NEXT MIDTERM. IT'S COMING UP, NOT THIS WEEK BUT THE NEXT WEEK.
1 MATH 16A LECTURE. OCTOBER 28, 2008. PROFESSOR: SO LET ME START WITH SOMETHING I'M SURE YOU ALL WANT TO HEAR ABOUT WHICH IS THE MIDTERM. THE NEXT MIDTERM. IT'S COMING UP, NOT THIS WEEK BUT THE NEXT WEEK.
data and is used in digital networks and storage devices. CRC s are easy to implement in binary
 Introduction Cyclic redundancy check (CRC) is an error detecting code designed to detect changes in transmitted data and is used in digital networks and storage devices. CRC s are easy to implement in
Introduction Cyclic redundancy check (CRC) is an error detecting code designed to detect changes in transmitted data and is used in digital networks and storage devices. CRC s are easy to implement in
Retiming Sequential Circuits for Low Power
 Retiming Sequential Circuits for Low Power José Monteiro, Srinivas Devadas Department of EECS MIT, Cambridge, MA Abhijit Ghosh Mitsubishi Electric Research Laboratories Sunnyvale, CA Abstract Switching
Retiming Sequential Circuits for Low Power José Monteiro, Srinivas Devadas Department of EECS MIT, Cambridge, MA Abhijit Ghosh Mitsubishi Electric Research Laboratories Sunnyvale, CA Abstract Switching
Feasibility Study of Stochastic Streaming with 4K UHD Video Traces
 Feasibility Study of Stochastic Streaming with 4K UHD Video Traces Joongheon Kim and Eun-Seok Ryu Platform Engineering Group, Intel Corporation, Santa Clara, California, USA Department of Computer Engineering,
Feasibility Study of Stochastic Streaming with 4K UHD Video Traces Joongheon Kim and Eun-Seok Ryu Platform Engineering Group, Intel Corporation, Santa Clara, California, USA Department of Computer Engineering,
THEATRE DESIGN & TECHNOLOGY MAGAZINE 1993 WINTER ISSUE - SOUND COLUMN WHITHER TO MOVE? By Charlie Richmond
 THEATRE DESIGN & TECHNOLOGY MAGAZINE 1993 WINTER ISSUE - SOUND COLUMN WHITHER TO MOVE? By Charlie Richmond Each time we get a request to provide moving fader automation for live mixing consoles, it rekindles
THEATRE DESIGN & TECHNOLOGY MAGAZINE 1993 WINTER ISSUE - SOUND COLUMN WHITHER TO MOVE? By Charlie Richmond Each time we get a request to provide moving fader automation for live mixing consoles, it rekindles
Sonic's Third Quarter Results Reflect Current Challenges
 Sonic's Third Quarter Results Reflect Current Challenges Sales Improve Steadily after Slow March, and Development Initiatives Maintain Strong Momentum Partner Drive-in Operations Slip OKLAHOMA CITY, Jun
Sonic's Third Quarter Results Reflect Current Challenges Sales Improve Steadily after Slow March, and Development Initiatives Maintain Strong Momentum Partner Drive-in Operations Slip OKLAHOMA CITY, Jun
MARKET OUTPERFORMERS CELERITAS INVESTMENTS
 MARKET OUTPERFORMERS CELERITAS INVESTMENTS Universal Displays (OLED) Rating: Strong Buy Stock Price: $101/share Price Target: $130/share MOP Idea of the Month: Universal Displays Business Overview: Universal
MARKET OUTPERFORMERS CELERITAS INVESTMENTS Universal Displays (OLED) Rating: Strong Buy Stock Price: $101/share Price Target: $130/share MOP Idea of the Month: Universal Displays Business Overview: Universal
Programming Distributed Systems
 Christian Weilbach & Annette Bieniusa Programming Distributed Systems Summer Term 2018 1/ 65 Programming Distributed Systems 13 Blockchains Christian Weilbach & Annette Bieniusa AG Softech FB Informatik
Christian Weilbach & Annette Bieniusa Programming Distributed Systems Summer Term 2018 1/ 65 Programming Distributed Systems 13 Blockchains Christian Weilbach & Annette Bieniusa AG Softech FB Informatik
6.UAP Project. FunPlayer: A Real-Time Speed-Adjusting Music Accompaniment System. Daryl Neubieser. May 12, 2016
 6.UAP Project FunPlayer: A Real-Time Speed-Adjusting Music Accompaniment System Daryl Neubieser May 12, 2016 Abstract: This paper describes my implementation of a variable-speed accompaniment system that
6.UAP Project FunPlayer: A Real-Time Speed-Adjusting Music Accompaniment System Daryl Neubieser May 12, 2016 Abstract: This paper describes my implementation of a variable-speed accompaniment system that
An optimal broadcasting protocol for mobile video-on-demand
 An optimal broadcasting protocol for mobile video-on-demand Regant Y.S. Hung H.F. Ting Department of Computer Science The University of Hong Kong Pokfulam, Hong Kong Email: {yshung, hfting}@cs.hku.hk Abstract
An optimal broadcasting protocol for mobile video-on-demand Regant Y.S. Hung H.F. Ting Department of Computer Science The University of Hong Kong Pokfulam, Hong Kong Email: {yshung, hfting}@cs.hku.hk Abstract
Enhanced JTAG to test interconnects in a SoC
 Enhanced JTAG to test interconnects in a SoC by Dany Lebel and Sorin Alin Herta 1 Enhanced JTAG to test interconnects in a SoC Dany Lebel (1271766) and Sorin Alin Herta (1317418) ELE-6306, Test de systèmes
Enhanced JTAG to test interconnects in a SoC by Dany Lebel and Sorin Alin Herta 1 Enhanced JTAG to test interconnects in a SoC Dany Lebel (1271766) and Sorin Alin Herta (1317418) ELE-6306, Test de systèmes
Achieving Faster Time to Tapeout with In-Design, Signoff-Quality Metal Fill
 White Paper Achieving Faster Time to Tapeout with In-Design, Signoff-Quality Metal Fill May 2009 Author David Pemberton- Smith Implementation Group, Synopsys, Inc. Executive Summary Many semiconductor
White Paper Achieving Faster Time to Tapeout with In-Design, Signoff-Quality Metal Fill May 2009 Author David Pemberton- Smith Implementation Group, Synopsys, Inc. Executive Summary Many semiconductor
GROWING VOICE COMPETITION SPOTLIGHTS URGENCY OF IP TRANSITION By Patrick Brogan, Vice President of Industry Analysis
 RESEARCH BRIEF NOVEMBER 22, 2013 GROWING VOICE COMPETITION SPOTLIGHTS URGENCY OF IP TRANSITION By Patrick Brogan, Vice President of Industry Analysis An updated USTelecom analysis of residential voice
RESEARCH BRIEF NOVEMBER 22, 2013 GROWING VOICE COMPETITION SPOTLIGHTS URGENCY OF IP TRANSITION By Patrick Brogan, Vice President of Industry Analysis An updated USTelecom analysis of residential voice
Supplemental Material: Color Compatibility From Large Datasets
 Supplemental Material: Color Compatibility From Large Datasets Peter O Donovan, Aseem Agarwala, and Aaron Hertzmann Project URL: www.dgp.toronto.edu/ donovan/color/ 1 Unmixing color preferences In the
Supplemental Material: Color Compatibility From Large Datasets Peter O Donovan, Aseem Agarwala, and Aaron Hertzmann Project URL: www.dgp.toronto.edu/ donovan/color/ 1 Unmixing color preferences In the
TEST WIRE FOR HIGH VOLTAGE POWER SUPPLY CROWBAR SYSTEM
 TEST WIRE FOR HIGH VOLTAGE POWER SUPPLY CROWBAR SYSTEM Joseph T. Bradley III and Michael Collins Los Alamos National Laboratory, LANSCE-5, M.S. H827, P.O. Box 1663 Los Alamos, NM 87545 John M. Gahl, University
TEST WIRE FOR HIGH VOLTAGE POWER SUPPLY CROWBAR SYSTEM Joseph T. Bradley III and Michael Collins Los Alamos National Laboratory, LANSCE-5, M.S. H827, P.O. Box 1663 Los Alamos, NM 87545 John M. Gahl, University
Behavior Forensics for Scalable Multiuser Collusion: Fairness Versus Effectiveness H. Vicky Zhao, Member, IEEE, and K. J. Ray Liu, Fellow, IEEE
 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 1, NO. 3, SEPTEMBER 2006 311 Behavior Forensics for Scalable Multiuser Collusion: Fairness Versus Effectiveness H. Vicky Zhao, Member, IEEE,
IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 1, NO. 3, SEPTEMBER 2006 311 Behavior Forensics for Scalable Multiuser Collusion: Fairness Versus Effectiveness H. Vicky Zhao, Member, IEEE,
AskDrCallahan Calculus 1 Teacher s Guide
 AskDrCallahan Calculus 1 Teacher s Guide 3rd Edition rev 080108 Dale Callahan, Ph.D., P.E. Lea Callahan, MSEE, P.E. Copyright 2008, AskDrCallahan, LLC v3-r080108 www.askdrcallahan.com 2 Welcome to AskDrCallahan
AskDrCallahan Calculus 1 Teacher s Guide 3rd Edition rev 080108 Dale Callahan, Ph.D., P.E. Lea Callahan, MSEE, P.E. Copyright 2008, AskDrCallahan, LLC v3-r080108 www.askdrcallahan.com 2 Welcome to AskDrCallahan
FPGA TechNote: Asynchronous signals and Metastability
 FPGA TechNote: Asynchronous signals and Metastability This Doulos FPGA TechNote gives a brief overview of metastability as it applies to the design of FPGAs. The first section introduces metastability
FPGA TechNote: Asynchronous signals and Metastability This Doulos FPGA TechNote gives a brief overview of metastability as it applies to the design of FPGAs. The first section introduces metastability
Peak Dynamic Power Estimation of FPGA-mapped Digital Designs
 Peak Dynamic Power Estimation of FPGA-mapped Digital Designs Abstract The Peak Dynamic Power Estimation (P DP E) problem involves finding input vector pairs that cause maximum power dissipation (maximum
Peak Dynamic Power Estimation of FPGA-mapped Digital Designs Abstract The Peak Dynamic Power Estimation (P DP E) problem involves finding input vector pairs that cause maximum power dissipation (maximum
ELIGIBLE INTERMITTENT RESOURCES PROTOCOL
 FIRST REPLACEMENT VOLUME NO. I Original Sheet No. 848 ELIGIBLE INTERMITTENT RESOURCES PROTOCOL FIRST REPLACEMENT VOLUME NO. I Original Sheet No. 850 ELIGIBLE INTERMITTENT RESOURCES PROTOCOL Table of Contents
FIRST REPLACEMENT VOLUME NO. I Original Sheet No. 848 ELIGIBLE INTERMITTENT RESOURCES PROTOCOL FIRST REPLACEMENT VOLUME NO. I Original Sheet No. 850 ELIGIBLE INTERMITTENT RESOURCES PROTOCOL Table of Contents
Combining Pay-Per-View and Video-on-Demand Services
 Combining Pay-Per-View and Video-on-Demand Services Jehan-François Pâris Department of Computer Science University of Houston Houston, TX 77204-3475 paris@cs.uh.edu Steven W. Carter Darrell D. E. Long
Combining Pay-Per-View and Video-on-Demand Services Jehan-François Pâris Department of Computer Science University of Houston Houston, TX 77204-3475 paris@cs.uh.edu Steven W. Carter Darrell D. E. Long
Analysis of Video Transmission over Lossy Channels
 1012 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 18, NO. 6, JUNE 2000 Analysis of Video Transmission over Lossy Channels Klaus Stuhlmüller, Niko Färber, Member, IEEE, Michael Link, and Bernd
1012 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 18, NO. 6, JUNE 2000 Analysis of Video Transmission over Lossy Channels Klaus Stuhlmüller, Niko Färber, Member, IEEE, Michael Link, and Bernd
For the SIA. Applications of Propagation Delay & Skew tool. Introduction. Theory of Operation. Propagation Delay & Skew Tool
 For the SIA Applications of Propagation Delay & Skew tool Determine signal propagation delay time Detect skewing between channels on rising or falling edges Create histograms of different edge relationships
For the SIA Applications of Propagation Delay & Skew tool Determine signal propagation delay time Detect skewing between channels on rising or falling edges Create histograms of different edge relationships
General purpose low noise wideband amplifier for frequencies between DC and 2.2 GHz
 Rev. 5 29 May 2015 Product data sheet 1. Product profile 1.1 General description Silicon Monolitic Microwave Integrated Circuit (MMIC) wideband amplifier with internal matching circuit in a 6-pin SOT363
Rev. 5 29 May 2015 Product data sheet 1. Product profile 1.1 General description Silicon Monolitic Microwave Integrated Circuit (MMIC) wideband amplifier with internal matching circuit in a 6-pin SOT363
Leakage Current Reduction in Sequential Circuits by Modifying the Scan Chains
 eakage Current Reduction in Sequential s by Modifying the Scan Chains Afshin Abdollahi University of Southern California (3) 592-3886 afshin@usc.edu Farzan Fallah Fujitsu aboratories of America (48) 53-4544
eakage Current Reduction in Sequential s by Modifying the Scan Chains Afshin Abdollahi University of Southern California (3) 592-3886 afshin@usc.edu Farzan Fallah Fujitsu aboratories of America (48) 53-4544
IMPLEMENTATION OF SIGNAL SPACING STANDARDS
 IMPLEMENTATION OF SIGNAL SPACING STANDARDS J D SAMPSON Jeffares & Green Inc., P O Box 1109, Sunninghill, 2157 INTRODUCTION Mobility, defined here as the ease at which traffic can move at relatively high
IMPLEMENTATION OF SIGNAL SPACING STANDARDS J D SAMPSON Jeffares & Green Inc., P O Box 1109, Sunninghill, 2157 INTRODUCTION Mobility, defined here as the ease at which traffic can move at relatively high
Modifying the Scan Chains in Sequential Circuit to Reduce Leakage Current
 IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 3, Issue 1 (Sep. Oct. 2013), PP 01-09 e-issn: 2319 4200, p-issn No. : 2319 4197 Modifying the Scan Chains in Sequential Circuit to Reduce Leakage
IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 3, Issue 1 (Sep. Oct. 2013), PP 01-09 e-issn: 2319 4200, p-issn No. : 2319 4197 Modifying the Scan Chains in Sequential Circuit to Reduce Leakage
White Paper Measuring and Optimizing Sound Systems: An introduction to JBL Smaart
 White Paper Measuring and Optimizing Sound Systems: An introduction to JBL Smaart by Sam Berkow & Alexander Yuill-Thornton II JBL Smaart is a general purpose acoustic measurement and sound system optimization
White Paper Measuring and Optimizing Sound Systems: An introduction to JBL Smaart by Sam Berkow & Alexander Yuill-Thornton II JBL Smaart is a general purpose acoustic measurement and sound system optimization
Design of an Error Output Feedback Digital Delta Sigma Modulator with In Stage Dithering for Spur Free Output Spectrum
 Vol. 9, No. 9, 208 Design of an Error Output Feedback Digital Delta Sigma odulator with In Stage Dithering for Spur Free Output Spectrum Sohail Imran Saeed Department of Electrical Engineering Iqra National
Vol. 9, No. 9, 208 Design of an Error Output Feedback Digital Delta Sigma odulator with In Stage Dithering for Spur Free Output Spectrum Sohail Imran Saeed Department of Electrical Engineering Iqra National
Achieve Accurate Critical Display Performance With Professional and Consumer Level Displays
 Achieve Accurate Critical Display Performance With Professional and Consumer Level Displays Display Accuracy to Industry Standards Reference quality monitors are able to very accurately reproduce video,
Achieve Accurate Critical Display Performance With Professional and Consumer Level Displays Display Accuracy to Industry Standards Reference quality monitors are able to very accurately reproduce video,
COMMISSION OF THE EUROPEAN COMMUNITIES COMMISSION STAFF WORKING DOCUMENT. accompanying the. Proposal for a COUNCIL DIRECTIVE
 EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 16.7.2008 SEC(2008) 2288 COMMISSION STAFF WORKING DOCUMENT accompanying the Proposal for a COUNCIL DIRECTIVE amending Council Directive 2006/116/EC
EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 16.7.2008 SEC(2008) 2288 COMMISSION STAFF WORKING DOCUMENT accompanying the Proposal for a COUNCIL DIRECTIVE amending Council Directive 2006/116/EC
RECOMMENDATION ITU-R BT Studio encoding parameters of digital television for standard 4:3 and wide-screen 16:9 aspect ratios
 ec. ITU- T.61-6 1 COMMNATION ITU- T.61-6 Studio encoding parameters of digital television for standard 4:3 and wide-screen 16:9 aspect ratios (Question ITU- 1/6) (1982-1986-199-1992-1994-1995-27) Scope
ec. ITU- T.61-6 1 COMMNATION ITU- T.61-6 Studio encoding parameters of digital television for standard 4:3 and wide-screen 16:9 aspect ratios (Question ITU- 1/6) (1982-1986-199-1992-1994-1995-27) Scope
Submitting a Research Book Proposal
 Submitting a Research Book Proposal Guidelines for Authors Introduction 1. Blurb 2. Statement of Aims 3. Table of Contents 4. Chapter Synopses 5. Length and Schedule 6. Definition of the Market 7. Competition
Submitting a Research Book Proposal Guidelines for Authors Introduction 1. Blurb 2. Statement of Aims 3. Table of Contents 4. Chapter Synopses 5. Length and Schedule 6. Definition of the Market 7. Competition
Example the number 21 has the following pairs of squares and numbers that produce this sum.
 by Philip G Jackson info@simplicityinstinct.com P O Box 10240, Dominion Road, Mt Eden 1446, Auckland, New Zealand Abstract Four simple attributes of Prime Numbers are shown, including one that although
by Philip G Jackson info@simplicityinstinct.com P O Box 10240, Dominion Road, Mt Eden 1446, Auckland, New Zealand Abstract Four simple attributes of Prime Numbers are shown, including one that although
A variable bandwidth broadcasting protocol for video-on-demand
 A variable bandwidth broadcasting protocol for video-on-demand Jehan-François Pâris a1, Darrell D. E. Long b2 a Department of Computer Science, University of Houston, Houston, TX 77204-3010 b Department
A variable bandwidth broadcasting protocol for video-on-demand Jehan-François Pâris a1, Darrell D. E. Long b2 a Department of Computer Science, University of Houston, Houston, TX 77204-3010 b Department
Notes on Digital Circuits
 PHYS 331: Junior Physics Laboratory I Notes on Digital Circuits Digital circuits are collections of devices that perform logical operations on two logical states, represented by voltage levels. Standard
PHYS 331: Junior Physics Laboratory I Notes on Digital Circuits Digital circuits are collections of devices that perform logical operations on two logical states, represented by voltage levels. Standard
ORTHOGONAL frequency division multiplexing
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 55, NO. 12, DECEMBER 2009 5445 Dynamic Allocation of Subcarriers and Transmit Powers in an OFDMA Cellular Network Stephen Vaughan Hanly, Member, IEEE, Lachlan
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 55, NO. 12, DECEMBER 2009 5445 Dynamic Allocation of Subcarriers and Transmit Powers in an OFDMA Cellular Network Stephen Vaughan Hanly, Member, IEEE, Lachlan
Draft Baseline Proposal for CDAUI-8 Chipto-Module (C2M) Electrical Interface (NRZ)
 Draft Baseline Proposal for CDAUI-8 Chipto-Module (C2M) Electrical Interface (NRZ) Authors: Tom Palkert: MoSys Jeff Trombley, Haoli Qian: Credo Date: Dec. 4 2014 Presented: IEEE 802.3bs electrical interface
Draft Baseline Proposal for CDAUI-8 Chipto-Module (C2M) Electrical Interface (NRZ) Authors: Tom Palkert: MoSys Jeff Trombley, Haoli Qian: Credo Date: Dec. 4 2014 Presented: IEEE 802.3bs electrical interface
C. PCT 1434 December 10, Report on Characteristics of International Search Reports
 C. PCT 1434 December 10, 2014 Madam, Sir, Report on Characteristics of International Search Reports./. 1. This Circular is addressed to your Office in its capacity as an International Searching Authority
C. PCT 1434 December 10, 2014 Madam, Sir, Report on Characteristics of International Search Reports./. 1. This Circular is addressed to your Office in its capacity as an International Searching Authority
Chapter 5: Synchronous Sequential Logic
 Chapter 5: Synchronous Sequential Logic NCNU_2016_DD_5_1 Digital systems may contain memory for storing information. Combinational circuits contains no memory elements the outputs depends only on the inputs
Chapter 5: Synchronous Sequential Logic NCNU_2016_DD_5_1 Digital systems may contain memory for storing information. Combinational circuits contains no memory elements the outputs depends only on the inputs
System Quality Indicators
 Chapter 2 System Quality Indicators The integration of systems on a chip, has led to a revolution in the electronic industry. Large, complex system functions can be integrated in a single IC, paving the
Chapter 2 System Quality Indicators The integration of systems on a chip, has led to a revolution in the electronic industry. Large, complex system functions can be integrated in a single IC, paving the
Understanding PQR, DMOS, and PSNR Measurements
 Understanding PQR, DMOS, and PSNR Measurements Introduction Compression systems and other video processing devices impact picture quality in various ways. Consumers quality expectations continue to rise
Understanding PQR, DMOS, and PSNR Measurements Introduction Compression systems and other video processing devices impact picture quality in various ways. Consumers quality expectations continue to rise
RECOMMENDATION ITU-R BT (Questions ITU-R 25/11, ITU-R 60/11 and ITU-R 61/11)
 Rec. ITU-R BT.61-4 1 SECTION 11B: DIGITAL TELEVISION RECOMMENDATION ITU-R BT.61-4 Rec. ITU-R BT.61-4 ENCODING PARAMETERS OF DIGITAL TELEVISION FOR STUDIOS (Questions ITU-R 25/11, ITU-R 6/11 and ITU-R 61/11)
Rec. ITU-R BT.61-4 1 SECTION 11B: DIGITAL TELEVISION RECOMMENDATION ITU-R BT.61-4 Rec. ITU-R BT.61-4 ENCODING PARAMETERS OF DIGITAL TELEVISION FOR STUDIOS (Questions ITU-R 25/11, ITU-R 6/11 and ITU-R 61/11)
F5 Network Security for IoT
 OVERVIEW F5 Network Security for IoT Introduction As networked communications continue to expand and grow in complexity, the network has increasingly moved to include more forms of communication. This
OVERVIEW F5 Network Security for IoT Introduction As networked communications continue to expand and grow in complexity, the network has increasingly moved to include more forms of communication. This
PEP-I1 RF Feedback System Simulation
 SLAC-PUB-10378 PEP-I1 RF Feedback System Simulation Richard Tighe SLAC A model containing the fundamental impedance of the PEP- = I1 cavity along with the longitudinal beam dynamics and feedback system
SLAC-PUB-10378 PEP-I1 RF Feedback System Simulation Richard Tighe SLAC A model containing the fundamental impedance of the PEP- = I1 cavity along with the longitudinal beam dynamics and feedback system
Chapter 3. Boolean Algebra and Digital Logic
 Chapter 3 Boolean Algebra and Digital Logic Chapter 3 Objectives Understand the relationship between Boolean logic and digital computer circuits. Learn how to design simple logic circuits. Understand how
Chapter 3 Boolean Algebra and Digital Logic Chapter 3 Objectives Understand the relationship between Boolean logic and digital computer circuits. Learn how to design simple logic circuits. Understand how
Spectroscopy on Thick HgI 2 Detectors: A Comparison Between Planar and Pixelated Electrodes
 1220 IEEE TRANSACTIONS ON NUCLEAR SCIENCE, OL. 50, NO. 4, AUGUST 2003 Spectroscopy on Thick HgI 2 Detectors: A Comparison Between Planar and Pixelated Electrodes James E. Baciak, Student Member, IEEE,
1220 IEEE TRANSACTIONS ON NUCLEAR SCIENCE, OL. 50, NO. 4, AUGUST 2003 Spectroscopy on Thick HgI 2 Detectors: A Comparison Between Planar and Pixelated Electrodes James E. Baciak, Student Member, IEEE,
An Interactive Broadcasting Protocol for Video-on-Demand
 An Interactive Broadcasting Protocol for Video-on-Demand Jehan-François Pâris Department of Computer Science University of Houston Houston, TX 7724-3475 paris@acm.org Abstract Broadcasting protocols reduce
An Interactive Broadcasting Protocol for Video-on-Demand Jehan-François Pâris Department of Computer Science University of Houston Houston, TX 7724-3475 paris@acm.org Abstract Broadcasting protocols reduce
System Level Simulation of Scheduling Schemes for C-V2X Mode-3
 1 System Level Simulation of Scheduling Schemes for C-V2X Mode-3 Luis F. Abanto-Leon, Arie Koppelaar, Chetan B. Math, Sonia Heemstra de Groot arxiv:1807.04822v1 [eess.sp] 12 Jul 2018 Eindhoven University
1 System Level Simulation of Scheduling Schemes for C-V2X Mode-3 Luis F. Abanto-Leon, Arie Koppelaar, Chetan B. Math, Sonia Heemstra de Groot arxiv:1807.04822v1 [eess.sp] 12 Jul 2018 Eindhoven University
High Performance Carry Chains for FPGAs
 High Performance Carry Chains for FPGAs Matthew M. Hosler Department of Electrical and Computer Engineering Northwestern University Abstract Carry chains are an important consideration for most computations,
High Performance Carry Chains for FPGAs Matthew M. Hosler Department of Electrical and Computer Engineering Northwestern University Abstract Carry chains are an important consideration for most computations,
Performance Driven Reliable Link Design for Network on Chips
 Performance Driven Reliable Link Design for Network on Chips Rutuparna Tamhankar Srinivasan Murali Prof. Giovanni De Micheli Stanford University Outline Introduction Objective Logic design and implementation
Performance Driven Reliable Link Design for Network on Chips Rutuparna Tamhankar Srinivasan Murali Prof. Giovanni De Micheli Stanford University Outline Introduction Objective Logic design and implementation
Analyze Frequency Response (Bode Plots) with R&S Oscilloscopes Application Note
 Analyze Frequency Response (Bode Plots) with R&S Oscilloscopes Application Note Products: R&S RTO2002 R&S RTO2004 R&S RTO2012 R&S RTO2014 R&S RTO2022 R&S RTO2024 R&S RTO2044 R&S RTO2064 This application
Analyze Frequency Response (Bode Plots) with R&S Oscilloscopes Application Note Products: R&S RTO2002 R&S RTO2004 R&S RTO2012 R&S RTO2014 R&S RTO2022 R&S RTO2024 R&S RTO2044 R&S RTO2064 This application
UC San Diego UC San Diego Previously Published Works
 UC San Diego UC San Diego Previously Published Works Title Classification of MPEG-2 Transport Stream Packet Loss Visibility Permalink https://escholarship.org/uc/item/9wk791h Authors Shin, J Cosman, P
UC San Diego UC San Diego Previously Published Works Title Classification of MPEG-2 Transport Stream Packet Loss Visibility Permalink https://escholarship.org/uc/item/9wk791h Authors Shin, J Cosman, P
THE USE OF forward error correction (FEC) in optical networks
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 52, NO. 8, AUGUST 2005 461 A High-Speed Low-Complexity Reed Solomon Decoder for Optical Communications Hanho Lee, Member, IEEE Abstract
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 52, NO. 8, AUGUST 2005 461 A High-Speed Low-Complexity Reed Solomon Decoder for Optical Communications Hanho Lee, Member, IEEE Abstract
A Light Weight Method for Maintaining Clock Synchronization for Networked Systems
 1 A Light Weight Method for Maintaining Clock Synchronization for Networked Systems David Salyers, Aaron Striegel, Christian Poellabauer Department of Computer Science and Engineering University of Notre
1 A Light Weight Method for Maintaining Clock Synchronization for Networked Systems David Salyers, Aaron Striegel, Christian Poellabauer Department of Computer Science and Engineering University of Notre
Simple motion control implementation
 Simple motion control implementation with Omron PLC SCOPE In todays challenging economical environment and highly competitive global market, manufacturers need to get the most of their automation equipment
Simple motion control implementation with Omron PLC SCOPE In todays challenging economical environment and highly competitive global market, manufacturers need to get the most of their automation equipment
Switching Solutions for Multi-Channel High Speed Serial Port Testing
 Switching Solutions for Multi-Channel High Speed Serial Port Testing Application Note by Robert Waldeck VP Business Development, ASCOR Switching The instruments used in High Speed Serial Port testing are
Switching Solutions for Multi-Channel High Speed Serial Port Testing Application Note by Robert Waldeck VP Business Development, ASCOR Switching The instruments used in High Speed Serial Port testing are
The Impact of Media Censorship: Evidence from a Field Experiment in China
 The Impact of Media Censorship: Evidence from a Field Experiment in China Yuyu Chen David Y. Yang January 22, 2018 Yuyu Chen David Y. Yang The Impact of Media Censorship: Evidence from a Field Experiment
The Impact of Media Censorship: Evidence from a Field Experiment in China Yuyu Chen David Y. Yang January 22, 2018 Yuyu Chen David Y. Yang The Impact of Media Censorship: Evidence from a Field Experiment
Marc I. Johnson, Texture Technologies Corp. 6 Patton Drive, Hamilton, MA Tel
 Abstract Novel Automated Method for Analyzing Peel Adhesion Ben Senning, Territory Manager, Texture Technologies Corp, Hamilton, MA Marc Johnson, President, Texture Technologies Corp, Hamilton, MA Most
Abstract Novel Automated Method for Analyzing Peel Adhesion Ben Senning, Territory Manager, Texture Technologies Corp, Hamilton, MA Marc Johnson, President, Texture Technologies Corp, Hamilton, MA Most
DELTA MODULATION AND DPCM CODING OF COLOR SIGNALS
 DELTA MODULATION AND DPCM CODING OF COLOR SIGNALS Item Type text; Proceedings Authors Habibi, A. Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
DELTA MODULATION AND DPCM CODING OF COLOR SIGNALS Item Type text; Proceedings Authors Habibi, A. Publisher International Foundation for Telemetering Journal International Telemetering Conference Proceedings
Dual frame motion compensation for a rate switching network
 Dual frame motion compensation for a rate switching network Vijay Chellappa, Pamela C. Cosman and Geoffrey M. Voelker Dept. of Electrical and Computer Engineering, Dept. of Computer Science and Engineering
Dual frame motion compensation for a rate switching network Vijay Chellappa, Pamela C. Cosman and Geoffrey M. Voelker Dept. of Electrical and Computer Engineering, Dept. of Computer Science and Engineering
LOUDNESS EFFECT OF THE DIFFERENT TONES ON THE TIMBRE SUBJECTIVE PERCEPTION EXPERIMENT OF ERHU
 The 21 st International Congress on Sound and Vibration 13-17 July, 2014, Beijing/China LOUDNESS EFFECT OF THE DIFFERENT TONES ON THE TIMBRE SUBJECTIVE PERCEPTION EXPERIMENT OF ERHU Siyu Zhu, Peifeng Ji,
The 21 st International Congress on Sound and Vibration 13-17 July, 2014, Beijing/China LOUDNESS EFFECT OF THE DIFFERENT TONES ON THE TIMBRE SUBJECTIVE PERCEPTION EXPERIMENT OF ERHU Siyu Zhu, Peifeng Ji,
An Efficient Implementation of Interactive Video-on-Demand
 An Efficient Implementation of Interactive Video-on-Demand Steven Carter and Darrell Long University of California, Santa Cruz Jehan-François Pâris University of Houston Why Video-on-Demand? Increased
An Efficient Implementation of Interactive Video-on-Demand Steven Carter and Darrell Long University of California, Santa Cruz Jehan-François Pâris University of Houston Why Video-on-Demand? Increased
Powerful Software Tools and Methods to Accelerate Test Program Development A Test Systems Strategies, Inc. (TSSI) White Paper.
 Powerful Software Tools and Methods to Accelerate Test Program Development A Test Systems Strategies, Inc. (TSSI) White Paper Abstract Test costs have now risen to as much as 50 percent of the total manufacturing
Powerful Software Tools and Methods to Accelerate Test Program Development A Test Systems Strategies, Inc. (TSSI) White Paper Abstract Test costs have now risen to as much as 50 percent of the total manufacturing
DragonWave, Horizon and Avenue are registered trademarks of DragonWave Inc DragonWave Inc. All rights reserved
 NOTICE This document contains DragonWave proprietary information. Use, disclosure, copying or distribution of any part of the information contained herein, beyond that for which it was originally furnished,
NOTICE This document contains DragonWave proprietary information. Use, disclosure, copying or distribution of any part of the information contained herein, beyond that for which it was originally furnished,
Simulation of DFIG and FSIG wind farms in. MATLAB SimPowerSystems. Industrial Electrical Engineering and Automation.
 CODEN:LUTEDX/(TEIE-7235)/1-007/(2009) Industrial Electrical Engineering and Automation Simulation of DFIG and FSIG wind farms in MATLAB SimPowerSystems Francesco Sulla Division of Industrial Electrical
CODEN:LUTEDX/(TEIE-7235)/1-007/(2009) Industrial Electrical Engineering and Automation Simulation of DFIG and FSIG wind farms in MATLAB SimPowerSystems Francesco Sulla Division of Industrial Electrical
Lesson 25: Solving Problems in Two Ways Rates and Algebra
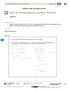 : Solving Problems in Two Ways Rates and Algebra Student Outcomes Students investigate a problem that can be solved by reasoning quantitatively and by creating equations in one variable. They compare the
: Solving Problems in Two Ways Rates and Algebra Student Outcomes Students investigate a problem that can be solved by reasoning quantitatively and by creating equations in one variable. They compare the
The Research of Controlling Loudness in the Timbre Subjective Perception Experiment of Sheng
 The Research of Controlling Loudness in the Timbre Subjective Perception Experiment of Sheng S. Zhu, P. Ji, W. Kuang and J. Yang Institute of Acoustics, CAS, O.21, Bei-Si-huan-Xi Road, 100190 Beijing,
The Research of Controlling Loudness in the Timbre Subjective Perception Experiment of Sheng S. Zhu, P. Ji, W. Kuang and J. Yang Institute of Acoustics, CAS, O.21, Bei-Si-huan-Xi Road, 100190 Beijing,
Practical Application of the Phased-Array Technology with Paint-Brush Evaluation for Seamless-Tube Testing
 ECNDT 2006 - Th.1.1.4 Practical Application of the Phased-Array Technology with Paint-Brush Evaluation for Seamless-Tube Testing R.H. PAWELLETZ, E. EUFRASIO, Vallourec & Mannesmann do Brazil, Belo Horizonte,
ECNDT 2006 - Th.1.1.4 Practical Application of the Phased-Array Technology with Paint-Brush Evaluation for Seamless-Tube Testing R.H. PAWELLETZ, E. EUFRASIO, Vallourec & Mannesmann do Brazil, Belo Horizonte,
Co-location of PMP 450 and PMP 100 systems in the 900 MHz band and migration recommendations
 Co-location of PMP 450 and PMP 100 systems in the 900 MHz band and migration recommendations Table of Contents 3 Introduction 3 Synchronization and timing 4 Frame start 5 Frame length 5 Frame length configuration
Co-location of PMP 450 and PMP 100 systems in the 900 MHz band and migration recommendations Table of Contents 3 Introduction 3 Synchronization and timing 4 Frame start 5 Frame length 5 Frame length configuration
Debugging Memory Interfaces using Visual Trigger on Tektronix Oscilloscopes
 Debugging Memory Interfaces using Visual Trigger on Tektronix Oscilloscopes Application Note What you will learn: This document focuses on how Visual Triggering, Pinpoint Triggering, and Advanced Search
Debugging Memory Interfaces using Visual Trigger on Tektronix Oscilloscopes Application Note What you will learn: This document focuses on how Visual Triggering, Pinpoint Triggering, and Advanced Search
Xpress-Tuner User guide
 FICO TM Xpress Optimization Suite Xpress-Tuner User guide Last update 26 May, 2009 www.fico.com Make every decision count TM Published by Fair Isaac Corporation c Copyright Fair Isaac Corporation 2009.
FICO TM Xpress Optimization Suite Xpress-Tuner User guide Last update 26 May, 2009 www.fico.com Make every decision count TM Published by Fair Isaac Corporation c Copyright Fair Isaac Corporation 2009.
VLSI Technology used in Auto-Scan Delay Testing Design For Bench Mark Circuits
 VLSI Technology used in Auto-Scan Delay Testing Design For Bench Mark Circuits N.Brindha, A.Kaleel Rahuman ABSTRACT: Auto scan, a design for testability (DFT) technique for synchronous sequential circuits.
VLSI Technology used in Auto-Scan Delay Testing Design For Bench Mark Circuits N.Brindha, A.Kaleel Rahuman ABSTRACT: Auto scan, a design for testability (DFT) technique for synchronous sequential circuits.
